I was at the Web Directions South conference the other day and you know what really struck me? There is a lot of very cool, very connected stuff either here now or coming very soon. Hackable stuff!
So there’s this term going around which is The Internet of Things (it has its own Wikipedia page so it must be real), or in human speak, stuff that’s connected to the web. Unusual stuff like domestic appliances and cars – literally “things” rather than devices as we know them such as PCs and phones. The term isn’t new, but the rapid emergence of “things” is.
One of the best presentations I saw was from Tom Coates who talked extensively about all sorts of “things” that were connected to services. In fact Tom had gotten his “things” so organised that his house even has its own Twitter account called @TheHouseOfCoates which tells you everything that’s going on in, well, Tom’s house:
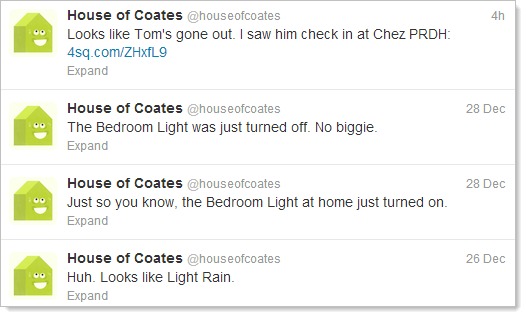
I harboured a brief pipedream of setting up something along the lines of RobTheHouseOfCoates.com which would provide would-be burglars with an easy notification system to identify prime periods where Tom’s house was unoccupied. This was partly inspired by PleaseRobMe.com but I ended up thinking better of it partly because Tom’s a nice bloke who I don’t want to see robbed and partly because it gave me grander, more devious ideas; just what opportunities is all this connectedness of “things” opening up to the evil-minded?
Clearly these “things” have the ability to improve our lives in all sorts of wonderful ways, but frankly, that’s a bit boring. Well at least it’s boring compared to the potential for misuse. That’s the exciting frontier; it’s one thing having your passwords breached on a website, it’s quite another when bad guys are controlling physical devices in your house. Let me speculate on just where this might be leading us…
Lockitron: The modern thief's best friend
In times gone by, the tools of the trade for a burglar looked something like this:

But in the very near future, the burglar’s best friend could look far more innocuous, it could look like this:

Welcome to Lockitron which brings thieves you the convenience of no longer needing a physical key. This is great in terms of convenience because it opens up a whole new world of access controls for the physical world such as granting guests the ability to unlock the home and monitoring lock status from afar. Lockitron sums up the options quite well:
Lockitron connects to the internet thanks to built-in WiFi. You can control Lockitron and receive notifications from Lockitron anywhere in the world.
Now the really neat thing about this device is that it snaps right onto existing deadlocks so almost anyone can get in on the remote unlock action:

But here’s the other interesting thing: Lockitron connects to your home wifi, right? And you can unlock it from a remote location, right? So in short – authentication aside – all that’s required is an internet connection. It has NFC and Bluetooth compatibility, but clearly there remains the ability to unlock the thing over public IP. But who would do this? I mean hacking electronic door locks is the stuff of fiction, right?
Yeah, not so much. Only last year we saw how millions of electronic hotel locks were vulnerable to 50 bucks worth of hacking equipment. Disclosing a vulnerability is one thing, but it seems that it’s already being exploited which really ratchets up the stakes. Now of course none of this means Lockitron itself is a risky device, in fact they’re quite clear on their security position:
Lockitron relies on the same security protocols used in online banking. We implement robust encryption using open, published standards.
Ah, yes, I’ve heard of online banking security in the past. I’ve also had some personal experience with robust, industry standard security! Look, maybe they’ve done a great job of things and everything will be fine, but hey, these guys can remotely unlock your door! That would make for an interesting insurance discussion…
The health consequences of poor security
Fans of the Homeland TV series will recall the demise of Vice President Walden towards the end of the last series. The VP was assassinated when terrorists gained remote access to his pacemaker and upped the rate of his heart until the poor fella suffered a fatal heart attack. That was fiction.
What Barnaby Jack demonstrated at the recent Breakpoint conference in Melbourne is not fiction. How about an 830 volt shock delivered remotely to one of these little guys:

Now of course this requires the victim to have a pacemaker installed, but whoa! I mean this is literally deadly force with nothing more than a laptop. But really, how much effort do you think goes into pacemaker security? I mean surely the priorities are things like efficacy and longevity, would security not naturally be an afterthought? (ok, maybe it’s not that different to traditional software development!)
A year back it was the same deal with insulin pumps. Once again, it was Barnaby Jack who demonstrated the ability to wirelessly control the pump to deliver potentially fatal doses of insulin.

Again, we’re talking serious adverse health impact here. The level of connectivity of these devices will differ, but the mere fact they can be controlled by an external piece of equipment starts to open up all sorts of interesting security discussions.
Hacking the smallest room in the house
There was a time when the toilet was a sanctuary away from the distractions of everyday life. Then came the mobile phone (followed by the smart phone) which allowed these distractions to join us in our daily rituals. But now things are being taken to a whole new level; there is the real risk of the toilet itself being hacked if you have one of these babies:

Naturally, because this is a quirky toilet-related product it comes to us from Japan (those of you who have visited understand). So how do you hack a toilet? Consider the following statement:
The Bluetooth-enabled INAX Satis model toilets can be controlled via your smartphone. All you need to do is to get the MySatis app and you will be able to flush, raise and lower the seat or turn on the bidet wirelessly. Moreover, you also have the option to control the intensity of the flush or the bidet spray. If that wasn’t enough, it also records your daily bowel movements, thanks to the Toilet Diary app.
In fact there’s also a nice little video tutorial which is somewhat enlightening:
Whilst it may not be an internet device per se, there are many documented precedents related to hacking Bluetooth devices. Then there’s the fact that this toilet seems to be designed for Android compatibility (how weird did that just sound?!) which seems to hit the headlines every other day at the moment with various malware or other security related exploits being discovered.
The thought of a malicious party remotely controlling the proboscis shown in the video above during a moment of quiet contemplation doesn’t bear thinking about. Plus of course there’s the Toilet Diary app tracking your bowel movements; what’s the security model around that little guy? How long before Facebook is showing you ads for high-fibre cereal based on a liberal approach to data privacy by the Satis app?
The lighter side of hacking
Ok, I’ll admit that these are pretty cool and I like the idea of having them in my home:

As you can clearly see, these are light bulbs with their own IP addresses. Let me say that again: they’re bulbs that fit into standard sockets and have their own fricken IP address! Somehow that just seems so much cooler than something like a fridge or a microwave being connected to the web.
So why does a light bulb need an IP address? Here you go:
Essentially, the lights include chips that give each bulb an Internet IP address so they can be monitored and controlled wirelessly online
Now this actually makes a lot of sense because it means you can do all that funky home automation stuff with a zero-friction install then control it all from the rich GUI of the device you’re carrying around in your pocket. Question is, who else can potentially control it? Whilst I’ve not seen it explicitly said, you can imagine how great it would look on the brochure to be able to say “Control your lights from anywhere!” or “Turn of those lights you forgot from the office”. It’s a great energy saving initiative, you see.
But it’s not just these guys, Philips has a similar system they call Hue. Let’s meet Hue:
Hey, what was that?
This is how Hue can be a better guard dog – than your guard dog – by making it look like you’re home, even if you’re miles away.
And this is in the context of lazing back by the pool from some remote location – told you it was coming!
So what are the options for malicious use? Well firstly, there’s the equivalent of the old “drive by and see if the lights are on” except that, well, you don’t actually need to drive by. If an attacker can gain access to what is inevitably an externally facing service, the old drive-by can be done from anywhere. Same deal with casing the place to identify behavioural patterns such as when people come home or go to bed except that it can still be done for Hue-equipped homes not visible from the road. Now combine that with PleaseRobMe.com and consider the potential…
Twine: Hack Listen to your world
Who’s seen one of these little beauties before?

Clearly, this is a Twine but what’s not so clear is that Twine is a WiFi connected device with a whole bunch of different sensors to monitor things like temperature, orientation, moisture and proximity (via a magnetic switch). And what can you do with this? Well, for example:
Maybe you want to get a tweet when your laundry's done, an email when the basement floods, or a text message when you left the garage door open.
In fact the potential is near limitless which is what makes it so cool and helps explain why they achieved 16 times their original Kickstarter target funding. As is the way with many connected devices these days, the Twine serves up a nice little web UI which provides both device status and configuration of alert services:
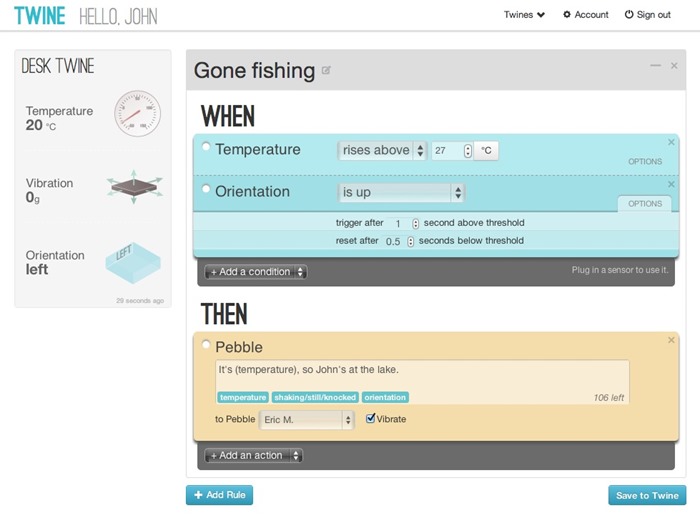
So the device has an IP and the ability to remotely access it plus based on the screen above, it also has an authentication process. Moving back into the evil mind space, one of the problems with this sort of facility has always been default passwords. In fact default passwords and Googleable web UIs have regularly been the catalyst for accessing private IP cameras and you’ll find a raft of information out there on useful info such as the default passwords for various cameras. Hopefully that’s not what Twine has done.
Moving on beyond authentication (a control we know is frequently broken through various means), the scope for doing bad things with Twines is limited only by the applications they’re applied to. The other day I heard Scott Hanselman talking about how he had one monitoring when his garage door opened so now we’re back into the “remotely watch as people come and go from their home” space. One watching for windows that weren’t properly closed would provide the would-be thief with similar options. Of course all of this is dependent on an attacker actually being able to view the device status, but that’s the entire assumption of this post: the potential ramifications when the security of these things goes wrong.
Sharing your vital statistics over the wire
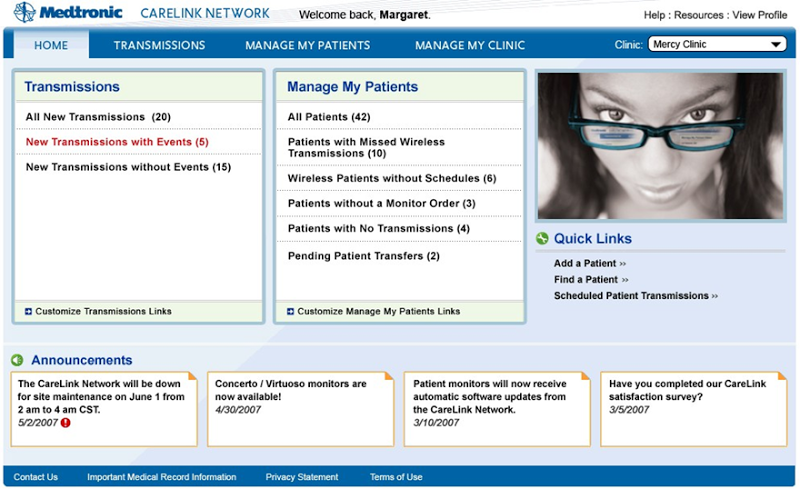
Here’s an interesting one: Medtronic CareLink which allows physicians to remotely monitor cardiac devices in patients:
As a clinician, you have 24/7 access – via a secure Internet website – to a wide range of trended reports offering information comparable to an in-office visit.
Thankfully, it uses a “secure Internet website” so we don’t have to worry, right? Hmmm…. there’s that word again, used as if it’s an absolute. These sort of websites tend to be represented as either totally secure (I assume some sort of impenetrable fortress) or, well, not. Moving on, the idea is that your doctor gets all your info presented via the browser after the cardiac device records the reading and, I assume, makes it available to the system via some form of aggregated, central resource. Here’s what goes into the browser:
Oh – and because this is the smart phone era then these days you have to have a native app as well:
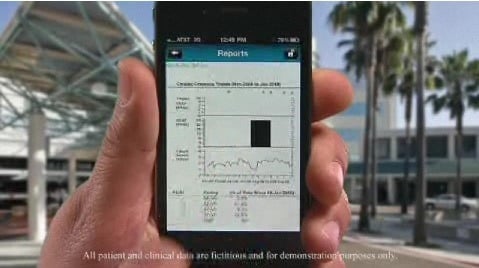
Naturally the app also requires an API so that’s another public access point (or attack vector, depending on your view on things).
But what can attacker do with this? I mean it’s not like the pacemaker earlier on where there’s the potential to actually control it, right? The thing is, if you could, say, get a man in the middle then you could manipulate the readings. What impact would it have if heart rate and blood pressure readings were manipulated? Could someone actually die? Conceivably, yes.
But you also need to consider the data which is now accessible via the public internet. It’s not just the current reading data either, this is almost certainly not just a direct read from the device and there is inevitably intermediary storage involved. What would be the impact of disclosure? The privacy implications of such personal data being leaked are mind boggling.
The security implications of the Nesting instinct
If I’m honest, I’d actually love to have one of these little guys:

This is a Nest or in other words, a very, very smart thermostat for your home’s climate control system. Part of the allure of Nest is that it retrofits to your existing home system and simply replaces the existing interface which is usually that hunk of boring grey plastic on your wall. Being the era of the internet of things, the Nest also exposes itself to the world:
Use the Nest Mobile app to connect to your thermostat from a smartphone. Getting in early? Change the temperature miles from home.
Now “exposes itself to the world” doesn’t necessarily mean that Nest security is a dodo, but what it does mean is that a very significant piece of household infrastructure is taking instructions over the web. I’ve had some climate control problems in the past and one thing I learnt is that they can do a lot of damage and cost a heap of cash. In my case, a condenser malfunction caused an excess of condensation to pool then leak down onto the bathroom ceiling which consequently collapsed. It wasn’t pretty.
So now the function of this very pricey piece of equipment can be controlled via smart phone or even through the browser right here:
Wonder if they’ve properly secured all those API endpoints? But hey, even if they have, the next time there’s a Gawker / Sony / RockYou style data breach it’s just a matter of finding a customer who also has a Nest account they’ve reused their password on and bingo – bad guys control a serious piece of equipment in the victim’s house. This is the unfortunate reality – no matter how good a job Nest has done with their security, the very fact that they’ve made the control of equipment with your house so easily accessible means that, well, it’s very easily accessible! But I still want one.
Hacking things beyond the house
In times gone by, car theft could be a messy business. I know it always looks easy in the movies, but getting into a locked car is harder than it looks and certainly starting it with all those new-fangled immobilisers is no easy task. Of course would be thieves could just go and carjack someone but then you’ve gotta be comfortable with the whole violence thing as well.
Fortunately for the budding criminal, it’s all getting a lot easier with devices such as Viper SmartStart:
It’s really quite easy:
Start, control or locate your car from virtually anywhere with your smartphone
Oh – and there’s also this:
You can also control multiple vehicles – great for families!
You know who else it’s great for? Course you do. The device also enables GPS tracking via the phone so this isn’t all just about remotely controlling the vehicle either.
The risk, of course, is threefold:
- Someone gets hold of your phone. Now you could argue that this is akin to someone else getting hold of your keys so the risk is comparable. But it’s not, because ultimately the capability on the phone is software (it’s not a physical asset) and one of the things we do with our phones is (hopefully) back the software up. Say you’re backing up to iCloud – now you have a capability within Apple’s data centre to start your car, all you need to do is restore from backup. Sound like science fiction? Not so much to Gizmodo journo Matt Honan.
- Someone gets hold of your Viper credentials. As with Nest, this “thing of the internet” can be controlled via the browser so if an attacker can get hold of your credentials (inevitably the same ones they’ve used all over the place), then you’re toast. But it might not be taking breached, reused credentials from somewhere else, it might just be a case of some clever phishing.
- Viper has a vulnerability. Of course I don’t know of any, but what I do know is that the vast, vast majority of assets on the web have multiple vulnerabilities of one kind or another and there are extensive statistics to support this. Maybe there’s a direct object reference flaw somewhere. Maybe it’s failure to restrict a particular API endpoint the smart phone apps users. It could take just one little oversight by one developer…
Then again, maybe everything is secure after all, they even have a padlock icon on the login page!
But of course Viper could do absolutely everything right and still have an issue. Maybe that old IIS6 web server they’re running on (and publicly disclosing via their response headers) isn’t patched. Maybe they’re using a third party product with a vulnerability (this allegedly brought Adobe undone a couple of months ago). The point, once again, is that once a thing can be accessed or controlled via the internet, you only need one little flaw for a catastrophe to occur. And a car is a pretty damn valuable “thing”!
Connecting your unconnected devices
All of this connectedness is great, but the reality is that we’ve got a heap of existing stuff around the house that isn’t connected. Never fear, if you’d like these devices to be hackable connected then help is at hand, all you need is a SmartThing:

And what, exactly, is a SmartThing? Glad you asked:
SmartThings makes it easy to connect the things in your physical world to the Internet. You can monitor, control, automate, and have fun with them from anywhere - at home, office, or on the go.
We've made it possible to install apps that interact with your SmartThings, as well as online and other services. This unlocks a world of possibilities and unlimited potential to make your life easier, more convenient and fun.
We call these SmartApps.
Monitor and control from anywhere? World of possibilities? No argument there!
The scope of this little device truly is unlimited because along with a gamut of sensors, it also includes the ability to control a power outlet which means literally that “anything that can be plugged in, can be turned on and off”. Blender, circular saw, oven – you name it – you can hand over control to instructions passed over HTTP! Smart.
The inherent security risk of connected devices
Look, I’m sure that for every one of the devices above the manufacturers have done their best to appropriately secure them (ok, maybe not the toilet, but I’m trying to give the benefit of the doubt here). The question is whether “their best” is enough because we’ve seen so many times how it simply isn’t. Consider the might of some of the organisations who were hacked in 2012 alone; LinkedIn (disclosed passwords hashed without salt), Zappos (personal information disclosure), Symantec (admitting to stolen Norton code), Adobe (breached code-signing server). These guys all have security resources far exceeding Lockitron’s or Twine’s.
The other thing is that even when we do a pretty good job of security, the frameworks, infrastructure and even protocol’s we’re dependent on have inherent risks. For example, even well-implemented SSL is subject to abuse via sslstrip due to the HTTP handshake that normally occurs after the user enters “www.whatever.com” into the browser (the protocol defaults to HTTP before being redirected by the server to HTTPS).
Or how about the BEAST attack against SSL? Many “secure” implementations remain vulnerable. But even if you get it all spot on, then you’ve got incidents like DigiNotar where the bad guys are signing their own certs for other peoples’ domains. Doesn’t matter how well you do your SSL if someone can plant a man in the middle and serve up a valid certificate for the domain!
Moving beyond transport layer protection, consider the likes of Stuxnet, Flame and Duqu. Granted, these all appear to be government sponsored so we’re talking serious resources behind them but what they all show is that “robust” measures are defeatable when the value of the target is significant enough. I’m sure that by any measure, the nuclear facilities at Natanz were “robust”, but here we are looking back at how they were defeated.
Just last week, the near ubiquitous Cisco IP phone made the news:

Chances are that just like the US president and director of the CIA, many of you reading this have one of these on your desk. Also just like them, you face the risk of a hacker surreptitiously turning the phone into a remote listening device. This is possible because ultimately the Cisco phone, the connected toilet, the clever light globes and everything else above are all dependent on microprocessors and software that is fallible. The point is that every one of the devices discussed here – and all the ones I didn't talk about or don’t know about – are vulnerable to an attacker with enough resources and sometimes, that’s a pretty low bar.
The rapid emergence of more connected “things”
CES was in full swing last week and it’s always a pretty good indicator of things to come. By things, of course I mean “things” and because they’re “things”, well, they’re connected.
For example, Belkin is getting more serious about the connected light switches game with WeMo:

Or how about the QNX Bentley which “features a web-app to remotely monitor and control the vehicle”:

Then there’s the HAPIfork to track your eating habits via smart phone (yes, seriously):

And there’s even the Discovery IQ Wall Oven running Android (what could possibly go wrong?!) which will allow you to “get your luxury oven warmed up before you get home”:

Next time you buy kitchen goods you might just be asking how much RAM the kettle has!
But seriously, all of these devices run operating systems and other pieces of software and they also connect to external devices or are directly accessible via the web. How many people are proactively thinking about the patch cycle for their oven? When should you check for service packs for your fork? Does your light switch need its own firewall? This is the world we’re entering and it’s going to provide exploits none of us have even considered until now.
In summary: this is the perfect storm of “internet thing” exploits
Whilst it’s a bit voyeuristic to sit back and speculate on possible risks and outcomes from the misuse of these devices, there are several very clear trends which make this all just a little bit exciting in terms of the information security ramifications:
- An increasingly large number of devices are getting IP addresses. Of course this is all about communicating and in many cases, controlling said device. With this comes the inherent risk that a device that can be controlled remotely can end up being controlled by a malicious party.
- Devices within internal networks are being controlled externally. This is going to be particularly interesting to watch because frankly, the ramifications are just a little bit horrifying. We’ve already seen many prior incidents of personal security cameras being inadvertently exposed publicly, now it’s going to be cameras, home security, toilet seats and so on and so forth.
- There’s a race to “get connected". We saw from CES last week just how ubiquitous connected devices are becoming; you could almost call it a connectivity arms race. The rush for vendors to compete in this extremely fast moving market will inevitably result in rushing aspects of the product design and we know very well from past incidents that security is one of the areas most frequently overlooked in favour of delivering features.
- Our levels of personal security awareness still suck. Last year I wrote about how 59% of accounts that were common across both Gawker and Yahoo! Voices shared the same password. Password reuse and other sloppy practices such as predictable (or even memorable) passwords are one thing when it means an attacker can make comments under your name on a media site, it’s quite another when they can unlock your front door.
- Our levels of developer security awareness also suck. They must as the software we build keeps hitting the front page of the news with alarming regularity. Look at the series of failures on a site like Tesco which is bad enough, but what if the guys building this are also building the interfaces for your IP-enabled home automation? That’s a little bit scary.
So this is where I see an exciting future for information security simply because all the screwy things we see happening with virtual assets are going to translate through to physical assets. They have to, we’re just simply not good enough at managing security yet for it not to.