Let’s assume you log onto a bunch of different websites; Facebook, Gmail, eBay, PayPal probably some banking, maybe a few discussion forums and probably much, much more.
Do you always create unique passwords such that you never use the same one twice? Ever?
Do your passwords always use different character types such as uppercase and lowercase letters, numbers and punctuation? Are they “strong”?
If you can’t answer “yes” to both these questions, you’ve got yourself a problem. But the thing is, there is simply no way you can remember all your unique, strong passwords and the sooner you recognise this, the sooner you can embrace a more secure alternative.
Let me help demonstrate the problem; I’ll show you what happens when you reuse or create weak passwords based on some real world examples which should really hit home. I’ll also show you how to overcome these problems with a good password manager so it’s not all bad news, unless you’re trying to remember your passwords.
The tyranny of multiple accounts
Think about it; how many accounts do you have out there on the internet? 10? 20? 50? I identified 90 of mine recently and there are many more I’ve simply forgotten about. There is absolutely no way, even with only 10 accounts, you can create passwords that are strong, unique and memorable.
What happens is that people revert to patterns including family names, pets, hobbies and all sorts of natural, somewhat predictable criteria. Patterns are a double-edged sword in that whilst they’re memorable, they also predictable so even if the pattern might seem obscure, once it’s known, well, you’ve got a bit of a problem.
Patterns and predictable words are bad, but what’s even worse is password reuse. Because we simply end up with so many of the damn things, the problem of memorising them gets addressed by being repetitive. Easy? Yes. Secure? No way.
The problem with weak passwords
Firstly, what exactly is a weak password? Let me answer this in a roundabout way by focussing on strong passwords; a strong password is one which has a high degree of what we call entropy, or in simple terms, one that is as long and as random (in terms of both character types and sequence), as possible. As the entropy link explains:
People are notoriously remiss at achieving sufficient entropy to produce satisfactory passwords.
People struggle with strong password because they revert to patterns that are easily memorable. The patterns may be in a natural form such as someone’s name, a date, or a place or they may be memorable keyboard patterns such as “qwerty” or “123456”. These are all highly predictable patterns.
Let me demonstrate the problem with this based on a few recent events. Firstly we have Gawker who last December were the victims of an attack which lead to the disclosure of somewhere in the order of one million user accounts. Worse still, these accounts were posted online and readily accessible by anyone who wanted to take a look at who had signed up to the service and what their password was.
The interesting thing in the context of password strength is the prevalence of bad password choices. Take a look at these:
123456, password, 12345678, qwerty, abc123, 12345, monkey, 111111, consumer, letmein, 1234, dragon, trustno1, baseball, gizmodo, whatever, superman, 1234567, sunshine, iloveyou, fuckyou, starwars, shadow, princess, cheese
These 25 passwords were used a total of 13,411 times by people with Gawker accounts. The first one – 123456 – was used over two and a half thousand times alone.
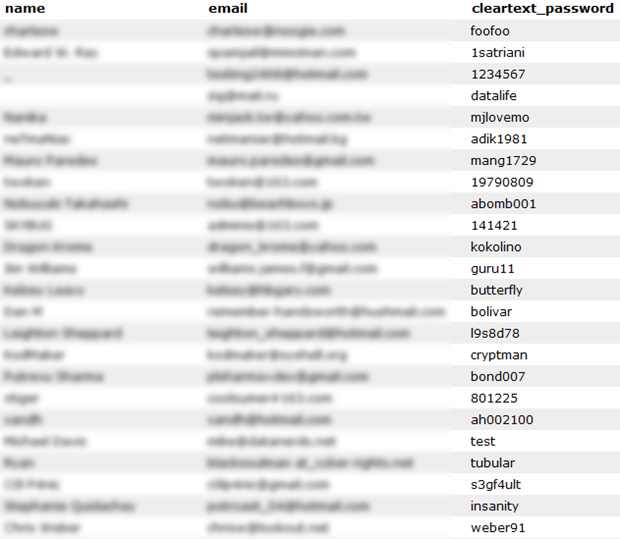
Another very similar example was an attack last month on rootkit.com. Password analysis on the breached database showed these top 25 passwords:
123456, password, rootkit, 111111, 12345678, qwerty, 123456789, 123123, qwertyui, letmein, 12345, 1234, abc123, dvcfghyt, 0, r00tk1t, ìîñêâà, 1234567, 1234567890, 123, fuckyou, 11111111, master, aaaaaa, 1qaz2wsx
Look familiar? Worse still, you can easily see the corresponding username if you know where to look (I’ve deliberately blurred these but the originals are still there in the link):
But here’s what’s really interesting about both these cases and the relevance to why password strength is important – all of these were stored in an encrypted fashion in the database. Without delving into cryptography concepts, the crux of the problem with both these sites is that the encryption was implemented badly.
When a database such as rootkit.com is released into the wild with poorly implemented encryption, hackers are able to recreate the encryption process by feeding in a dictionary of common passwords and attempting to compare them to the database to find matches. The nature of encryption can mean this process needs to be repeated millions of times, but it’s an entirely automated process.
Password dictionaries are commonly available (wonder if you see any of yours in there?), as is the software to run them against the breached database. The biggest limitation is the computing power required to perform a fairly resource intensive process but as we all know, compute power is increasing at a very rapid pace and besides, you can easily acquire enough processing power to test 400,000 passwords per second for only 28 cents per minute.
But the bottom line is this; if your password conforms to a recognisable pattern, there’s a good chance it will either be in a password dictionary or guessable based on other known information about you (wife’s or kids name, etc.) If it is short or doesn’t contain sufficient variations in characters, the number of attempts required to guess it are going to be much lower; you become the low hanging fruit.
The problem with password reuse
You’re probably already aware that you shouldn’t be reusing the same password in multiple locations, but let me illustrate as clearly as I can, from a firsthand perspective, why not. Here’s what was waiting for me in my email when I logged on recently:
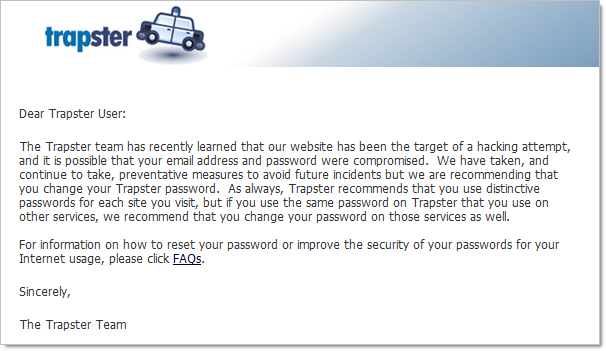
In case it’s not perfectly clear, having your email address and password compromised isn’t exactly ideal. When the scope of those credentials is one website, it’s an inconvenience. However, if those credentials were reused across your financial institutions, your social networking sites or particularly your email account, that’s not inconvenient, that’s downright scary and potentially very expensive for both your hip pocket and your reputation.
Only the day after the Trapster incident, tweets like this started popping up:
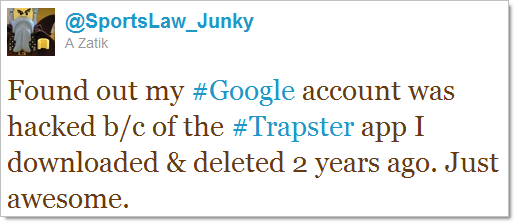
 Going back to the Gawker incident I mentioned earlier, shortly afterwards, something odd started happening to the Twitter accounts of people who also had accounts with Gawker; they started ranting on about Acai berries.
Going back to the Gawker incident I mentioned earlier, shortly afterwards, something odd started happening to the Twitter accounts of people who also had accounts with Gawker; they started ranting on about Acai berries.
This is a crystal clear example of what happens when you reuse credentials. The Gawker database was large enough and the whole password reuse phenomenon rampant enough that the perpetrators were bound to compromise a lot of Twitter accounts. What these incidents are showing us is that based on real-world data analysis, password reuse is alarmingly high.
Undoubtedly, much of this problem is related to poor security implementations on websites. It’s very, very easy to build websites with fundamental security flaws. Another problem in this area is that all too often software developers take the attitude of “The information on our site isn’t that sensitive so security isn’t too important”. Of course if you’ve gone and used the same credentials for that site and your PayPal account, you could have a serious problem just around the corner.
Because we all reuse usernames – and often your username is your email address so there’s not much choice – it’s a very short hop from one compromised account as a result of a database disclosure to another compromised account simply by matching usernames and passwords. In fact there’s a school of thought that usernames betray you and Hotmail even recently gave you the ability to easily create additional email addresses which could mitigate the risk of matching accounts but that’s probably going a little further than what you really need to right now.
Just how prevalent is this sort of thing?
Very. Gawker, rootkit.com and Trapster are all very recent examples but there are many, many more. Into online dating? You’ve probably heard of “Plenty of Fish”:
Like the scented, soapy goodness from Lush? Their UK site got hit earlier this year:
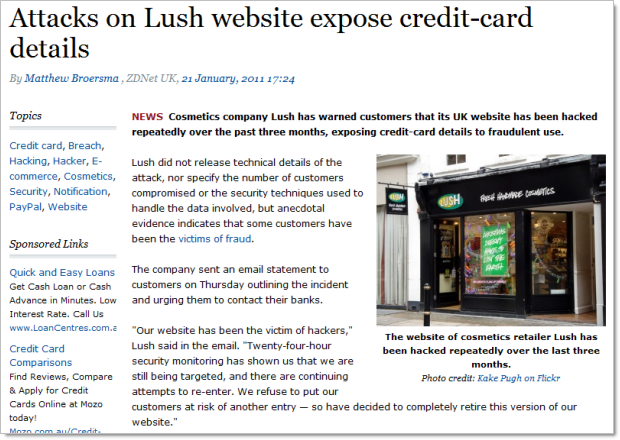
Not in the UK and think your Lush details are safe? Not quite (but don’t worry, the incidents are “unrelated”…):

Of course these were all very targeted attacks. Malicious computer activity goes well beyond this and is often very indiscriminate. We’re now at about 50 million viruses and counting, 20 million of those having hit people just last year.
I’m making these points not to scare you, rather I’m trying to make it evident that this is a very, very common thing indeed. The examples above are just a few of the ones we actually know of from very recent times. There’s a significant order of magnitude more where your credentials have been exposed that we don’t know of, and probably a good proportion of those where the website operators don’t even know of the breach. This is commonplace folks, and it’s up to you to make a preemptive strike against the bad guys.
The myths of “secure” passwords
First and foremost, the word “secure” is frequently thrown around like it’s an absolute term. It’s not. Look no further than the Stuxnet virus; computers running the centrifuges in Iranian nuclear facilities entirely disconnected from the internet were successfully targeted by the virus. Surely those systems would have been considered “secure” by any reasonable definition of the word.
It’s a little bit like saying a car is “safe”. Some are better than others, no doubt, but at the end of the day it becomes a risk mitigation exercise. You trade some things off – such as the simplicity of a password or price paid for a car – and you get a better risk profile in return such as longer to crack the password or more airbags in the car.
Here’s how some people (Google, in this case), believe you should create – and remember – secure passwords:
Seriously? Can you imagine trying to remember dozens of “I love sandwiches” style of passwords? Keep in mind you need to remember what the phrase was, which characters you substituted and which one you used for which site.
Besides, the whole idea of strong passwords is to avoid predictable patterns. Is substituting an “@” in place of an “a”, or a “3” in place of an “e” really going to throw the bad guys off the scent? Memorised patterns with substituted characters are a very thin veneer of security and trust me, the bad guys have heard of this trick.
In fact, the password dictionary I linked to earlier contains many common occurrences of character substitution. In there you’ll find examples such as “s@yg00dbye” and “s0cc3rRul3s” – not exactly “secure”.
Writing your passwords down on paper also isn’t going to do you any favours. Because you’ve got so many of them (and face it, you do), you’re going to need to also write down which account the password belongs to which means you’ve got the mother lode of credentials sitting there ripe for the burglar / kids / nosy guests.
The other problem with handwritten account details is that these days many of us are logging in to many different locations such as the home PC, work PC and increasingly, our mobile devices. We can’t practically have the keys to our online world locked away in a drawer somewhere – it’s simply too big of an inconvenience for many people.
And finally, the handwritten strong password is just too damn painful to continually re-enter every time you logon somewhere. Remember, a strong password is very long and very random; exactly the attributes which makes manually typing them tedious and error prone.
So what about just storing them in a Word doc or in a notes system like Outlook? Because they’re just too easy to steal and when this happens, they’re easy to extract because they’re not encrypted. Someone gets their hands on that file and you are well and truly compromised in a most unpleasant way.
Liberating yourself from the tyranny of passwords
At face value the title of this post sounds odd. How on earth can you continue logging on to websites if you’ve forgotten all your passwords?! You need a dedicated password management system, pure and simple. There is just not another practical and secure way of dealing with it in the current day.
Fortunately there are tools out there focussed at doing just that. For example, there’s LastPass, KeePass and my personal favourite, 1Password. All of these tools give you the ability to record all your passwords in a single, strongly encrypted location. Of course you still need a password in order to unlock the encrypted file, but as a couple of the earlier mentioned product names suggest, you only need to remember a single one.
Here’s the critical point: this single password must be strong! If you’re going to lock up the keys to every single website with just one password, you can forget about birthdays and kids names and sandwiches, you really need to pick something decent this time.
The 1Password approach
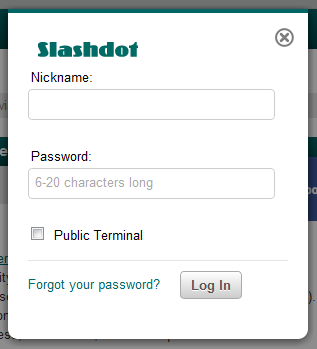
Running 1Password, let me show you what happens when I log on to a website in the traditional way. I’m going to log into Slashdot which is a bit of a techie website but the process is pretty much the same for almost every website out there.
We start off with the usual username and password:
But after I hit the “Log In” button, 1Password offers to save the credentials:
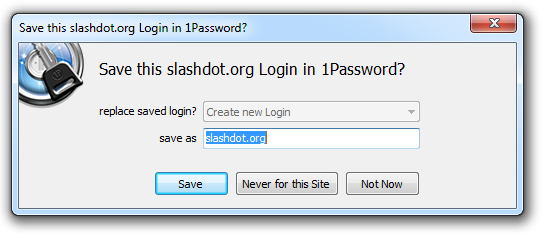
The name defaults to the address of the page but I can always rename it to something more logical either now or a little later on. Once I hit the “Save” button, 1Password asks me for the “Master" Password”, that is the single password required to manage all my other ones:
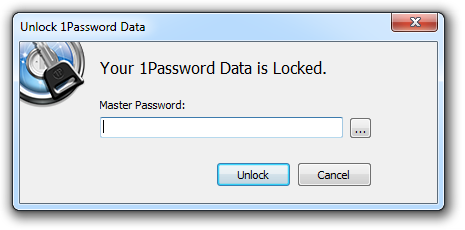
This is one, single, strong password which I have memorised. In fact it’s now the only one I’ve memorised and no, it’s not “Iloves@nDwich3s”!
With this saved, let me now log out of Slashdot then go back and attempt to login again but this time, rather than entering my Slashdot credentials (which I’ve conveniently and deliberately forgotten), I’m going to hit the little key icon to the right of the URL bar:
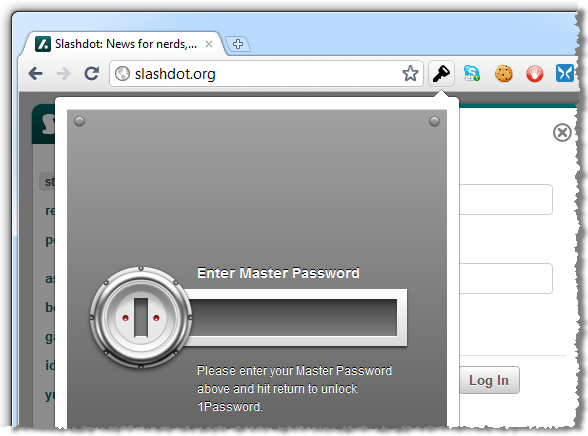
This is now asking for my master password again – the only one I ever need to remember. After entering this, I can see the entry created earlier on:
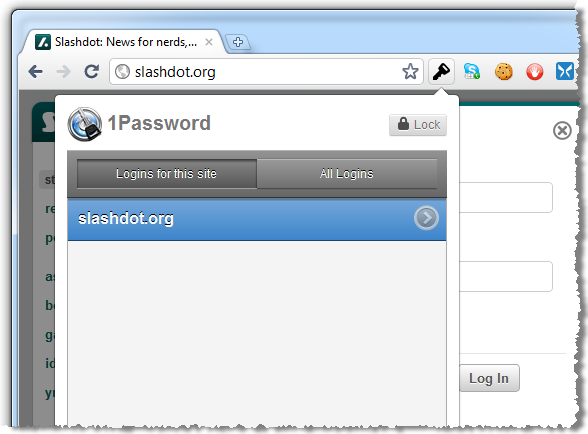
I could have multiple entries in here (you might have more than one account at a particular site), but I’ll just double click on the existing entry. And that’s it – we’re now logged on!
The beauty of this process is that it’s identical for every single site. I don’t need to remember those 90 odd passwords any more, I simply need to go through the motions of manually logging onto each site once and allowing 1Password to save the credentials.
You can also do this from different browsers. I’m using Google Chrome in the examples above but 1Password also integrates with other browsers.
Getting secure
Of course the chances are your passwords aren’t real secure to begin with and all this process is doing is keeping a secure record of bad passwords. This is a great time to do some housekeeping and 1Password makes it very easy.
When I went through and added all my accounts, each time I came across one with a weak password I went into the 1Password application, opened up the account I just created and generated a new one. There’s a really neat little tool built right in which makes this a breeze:
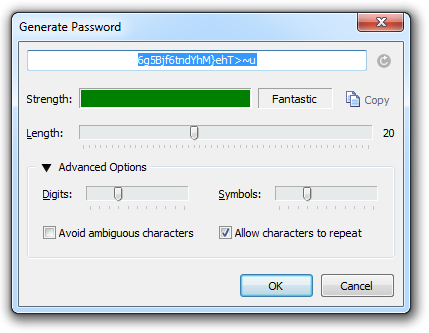
This is what a secure password looks like (highlighted in blue above). If it’s not something you need to be a savant to memorise, it’s not secure enough. But of course with the process described above it doesn’t matter that the password is entirely unintelligible, all you need to remember is your master password.
Now, this process won’t actually change your password on the website, only the one you have recorded in 1Password. You’ll need to copy this one into your clipboard then go onto the individual website and change it accordingly. Yes, it’s a bit of mucking around but for the sake of a few minutes you’ve just created a very secure, very unique password which can’t be used against you on any of your other online accounts.
There’s one gotcha in all of this; some websites don’t let you create secure passwords. Earlier this year I wrote about the Who’s who of bad password practices – banks, airlines and more where I found that some websites – especially banks, oddly enough – simply won’t let you construct long, random passwords. Either they limit the length to a very low number, they disallow many character types or in extreme examples, they insist on a short PIN containing only numbers. Unfortunately you’re entirely at the mercy of the controls these sites place on passwords so when you hit a limitation like this all you can do is maximise what you can within a ridiculous constraint.
Taking your passwords with you
One thing that was important to me was that I could access my passwords from any location, on any device, at any time. Work PC, home PC, iPad and iPhone all needed to sync up.
1Password lets you do all of this by using the Dropbox file syncing service. This is a great product which has proven very robust and is easy to configure to keep your 1Password file synced. In the end, it means all my PCs have the same secure password file and my iPad and iPhone respectively have friendly little apps like these:
Is it risky putting the password file online? Well there’s a degree of risk, sure, but the Dropbox service has proven a very secure implementation over the years. And of course the 1Password file is still securely encrypted so even if someone gets their hands on it, they still need the (strong) master password. In fact the weakest link in the whole thing is probably the password you secure your Dropbox account with which, by now of course, is also very strong :)
Isn’t this “all your eggs in one basket” stuff?
Yes, it is, but it’s a basket that is very well thought out and very firmly secured. Someone would have to firstly obtain the file containing all the passwords exposed and secondly have your master password either disclosed, guessed or brute force attacked, none of which should happen if you choose one securely.
Whilst having all your account details exposed at once is undoubtedly a very bad thing, the risk is infinitesimal compared to the chances of having it breached via website.
Of course the other risk is that an as yet unknown vulnerability is found with the 1Password software. Certainly what we’d call a zero-day vulnerability (one that is not yet known), is possible. In fact there was one found in LastPass just last month and to their credit, they plugged that hole in no more than a few hours. And that’s the point with professional products of this nature; their entire being is centred on offering a secure solution and if a vulnerability is found, you can be pretty damn sure it’s going to be squashed very quickly.
Summary
So now that you’ve got all this super security, you’re pretty much invincible right? Uh…
And this brings me to a neat philosophical conclusion; security is all about risk mitigation -you never actually become “secure”, you merely decrease your risk. On balance, the risk of your account details sitting out there in even a very secure website is significantly higher than having them sit there in your 1Password file.
But beyond just security, the password manager route is a very handy solution. Having all your accounts handy on all your devices and being able to simply logon with the once strong password is a very convenient route indeed.
And finally, when the time comes that you realise one of your accounts has been breached (and trust me, it will come), it’s no good thinking about password security then – it’s too late. So put aside a few hours one afternoon, spend just a few dollars and get yourself organised. Either that or start developing a taste for acai berries!