Just over a year ago to the day, my wife and I walked into the Apple store in Sydney’s CBD and bought her a shiny new MacBook Air. Macs weren’t familiar territory for us so we happily accepted the offer for a staff member to walk us through some of the nuts and bolts of OSX. That was a handy little starter and we left the store none the wiser that the machine now had a serious security risk that wouldn’t become apparent for another year.
A couple of weeks ago I wrote about my new favourite device, the Wi-Fi Pineapple. Despite its friendly tropical name, the Pineapple is a piece of cigarette-pack-sized professional security equipment I picked up online for $100 to help me demonstrate secure coding practices. Specifically, it’s helping me educate web developers about the risk of not using encryption between browsers and the websites they’re communicating with, something that needs to be built into the design of the site itself.
Among various party tricks packed into this little piece of equipment is a feature called “Karma” and it works like this: When you connect a device to a wireless network – let’s imagine the network is named “WILSON” for the purposes of demonstration – the device then continues to look for that network for perpetuity. What that means is that the device (laptop, smart phone, tablet, etc.) is running around shouting “WILSON, WILSON, where are you WILSON?” What Karma says when it hears this is “I’m Wilson, let’s get connected” and if WILSON wasn’t originally secured with a wireless password, the device connects to the Pineapple automatically. It now looks just like a normal wireless connection and it has been made without any action whatsoever on the user’s behalf.
You didn’t know this could happen? It’s written right there on the wireless network screen of every iOS device, albeit without explaining that “Known” means nothing more than an access point claiming to be exactly what the device has just publicly broadcast it’s looking for:
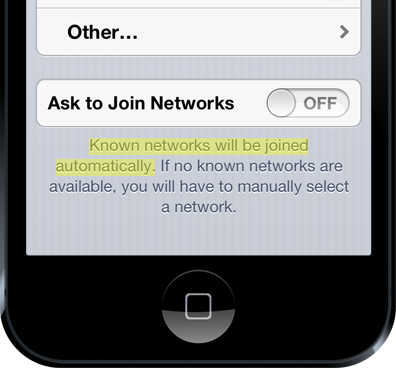
So what’s the risk of a device connecting to the Pineapple (or any similar equipment – it’s not the only one) without knowing it? It means that every single byte of data that passes through that connection and is not encrypted can be read or changed by an attacker. Passwords, personal information, photos, videos and anything else not properly protected by the website can be intercepted. Links to secure login pages, documents, emails and even banking websites can be manipulated when that protection doesn’t exist.
What’s now evident is that a large number of devices are leaving Apple stores after having been connected to an insecure network leaving them at risk for years to come. Let me explain.
The “Apple Demo” conundrum
When I wrote the blog post I mentioned above I commented that whilst testing the Pineapple I noticed some unexpected traffic flowing through it, traffic that looked like this:
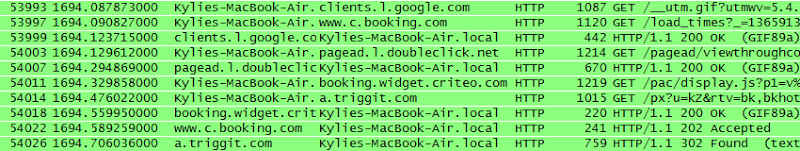
This is my wife’s MacBook Air and I was able to intercept her internet traffic simply because she had wandered into range. This struck me as odd at the time because she had already been connected to our (secure) home wireless that also had a much stronger signal than the Pineapple’s. Sure enough though, she was now connected to the Pineapple’s rogue access point under the name “Apple Demo”:
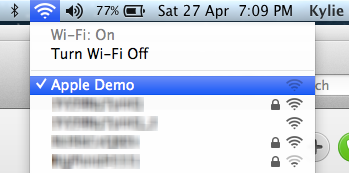
I made a note of this in the post then moved on.
Then this weekend just gone I was at a Microsoft event in a small room with dozens of fellow techie people, all with their laptops out for hours on end. Some of them were Macs. In amongst participating in the activities of the day, I was also preparing for a conference talk I’m doing down in Melbourne later this week which will involve using the Pineapple to demonstrate the risk of websites that don’t implement sufficient security measures. Without giving away the details of a yet-to-occur event, I had configured the device to simply see if anything would connect to it – and it did. Here’s what happened:
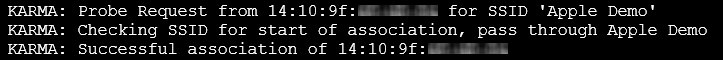
This is a “Probe Request” from a Wi-Fi device which as I explained earlier, is essentially the device calling out “WILSON” except that in this case, it’s calling out “Apple Demo”. The Pineapple then responds with “I’m Apple Demo” and a successful association is made. Had the Pineapple been connected to the internet, all the unencrypted communication between the device and any websites it visited or services any apps connected to could have been logged or manipulated.
In the image above, the first and last lines contain the partially blurred MAC address – the uniquely identifying fingerprint that all network devices have – of the device that connected. The first three sets of two digits are the organisationally unique identifier which tells us who manufactured the device. You can check it up online and you’ll get a result that’s not too surprising:
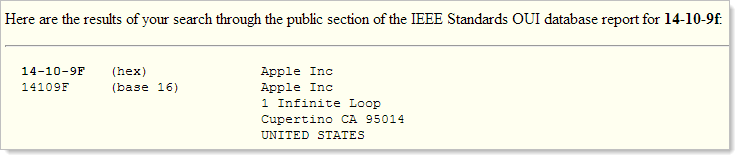
In the very small amount of testing I’d done with the Pineapple, this was the second Mac that had connected to the same insecure network it had previously been associated to. This was more than just coincidence and far too prevalent for such a small sample size. It was time a visit to the Apple store.
The Sydney Apple store
As is usually the case with Apple, the Sydney store is an impressive piece of architecture with an amazing glass facade:

I’d made an appointment with a Genius to take a look at my iPad and had a bit of time to kill first so thought I’d take a look at what all the display models were connecting to. First up was an iPad mini:
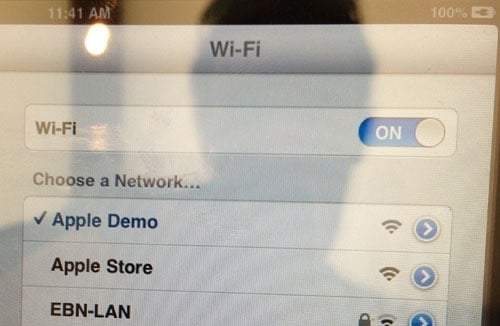
And then a MacBook Pro:
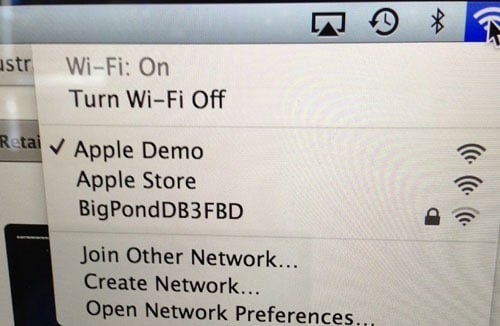
Although not surprising, it’s reasonable validation of the assumption regarding the origin of the other “Apple Demo” machines I’d been seeing. Of course the main thing is that the network is still insecure – there’s no padlock icon hence no Wi-Fi authentication is required. Now none of that matters in this case anyway – you’re not exactly about to do anything of a nature where you’d want to protect your data using floor stock.
I go upstairs for my appointment with the Genius and explain two issues I’m genuinely having with the iPad that irk me. Both issues will require internet to demonstrate. The Genius – let’s call him “John” – is exceptionally helpful and he promptly directs me over to the Wi-Fi settings on the iPad and has me select this:
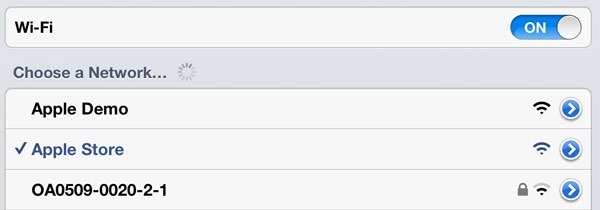
It’s “Apple Store” rather than “Apple Demo” but the risk is identical – there’s no wireless password and the device will now happily remember this name and attempt to reconnect to it at any time. We finish our session and I leave the store.
I come home, turn on the Pineapple and immediately see this:

My once-secure iPad has now become vulnerable. As soon as I walked out of the store the device started looking to reconnect to anything that would acknowledge it. Consider the consequences of this: as soon as someone walks out of the Apple store after receiving support it’s highly likely that an attacker can begin immediately monitoring their internet traffic. It’s that easy.
What can you do if you own a Mac?
When I looked at the network properties of my wife’s Mac, obviously there was a stored connection to Apple Demo:
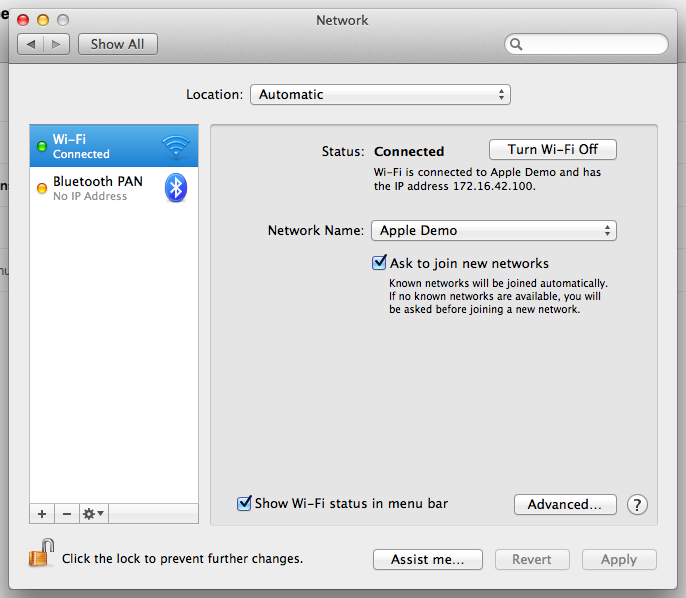
What really made the risk hit home though was when I looked at the “Advanced…” settings of the network:
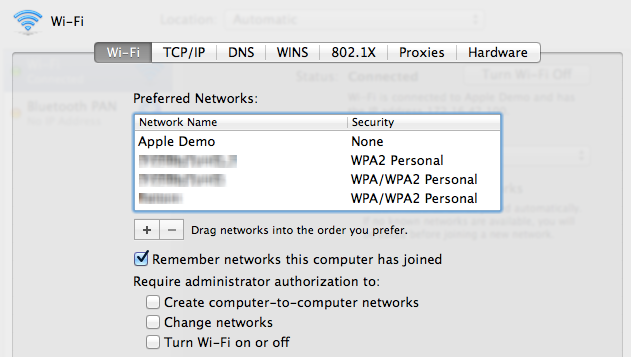
The Apple Demo network is the first on the list and will take priority over all networks that came after it. My wife’s machine first connected to Apple’s network then we came straight home and set it up on our own. Even now, one year later, the machine is still prioritising the first network it connected to and dropping off the newer one. This meant that the Pineapple was able to hijack the connection even when the machine already had a perfectly legitimate association to a wireless access point.
The solution is simply to delete any networks where the Security is “None”. That’s easy on the Mac, not so much on iOS.
What can you do if you own an iOS device?
It’s a little trickier in iOS as there’s no way of viewing the networks the device has previously connected to and consequently no way of removing the insecure ones. In fact the only way you can forget an individual network and not automatically reconnect to it is by selecting it when the network is in range:
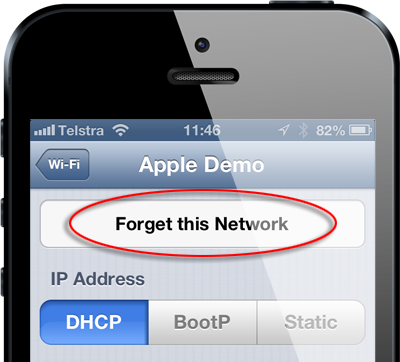
This isn't going to do most people much good as they’re not exactly going to travel back to the store just to have their device forget the network. If you think it might have gone through the demo or support process in store or for that matter connected to any unprotected wireless network you’ll need to erase all your trusted ones and start from scratch.
Jump over to “Settings” –> “General” –> “Reset” and then “Reset Network Settings”:
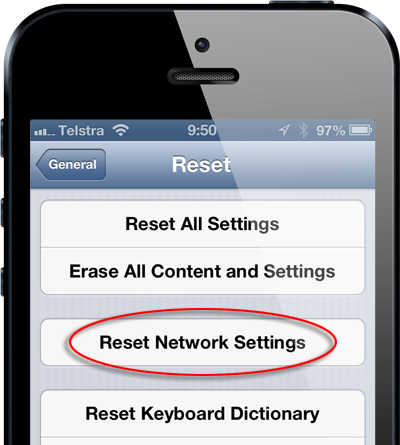
It’s going to make it unpleasant if you regularly connect to secure networks you now need to go and retrieve passwords for again, but it will ensure your iOS device hasn’t left Apple with a serious security risk.
Can’t this happen after connecting to any insecure wireless network?
It sure can. If you go down to McDonalds and jump on their free Wi-Fi and it doesn’t require a password, you’ve got exactly the same problem. The difference, of course, is that McDonalds makes fast food whilst Apple makes devices with networking capabilities. McDonalds (and similar) need to lift their game and secure their network (and of course deal with the usability issues that creates) but to some degree they can be forgiven for the oversight.
When you buy a brand new phone or tablet or laptop you expect to walk out of the store with a secure piece of equipment, certainly one that would take some amount of effort to exploit. That’s not what’s happening after Apple connects it in-store and that’s the real story – it’s insecure by default and vulnerable to a simple attack from day one.
This may well be the case with other stores as well. I don’t know how Microsoft or Samsung or other retail outlets selling similar devices and offering a similar setup service handle wireless connections, but clearly if they’re not using a protected network then they’re leaving consumers with exactly the same risks.
Keeping customers safe is as easy as pie
Paradoxically, there’s a little meat pie shop just around the corner from Apple’s gleaming architectural masterpiece. The pie shop is nothing more than a hole in the wall with a counter one staff member can barely fit behind. Somehow they still manage to offer free Wi-Fi and use an ingenious means of properly securing it for their customers. It works like this:

That’s all it takes – kindly provide customers with a Wi-Fi password when they ask and this entire problem just disappears. Good work by the pie shop!
For the more technically minded
For those who want some more detail, here are a few key points:
Traffic sent via HTTPS can’t be intercepted and either read or manipulated by a man in the middle, at least not without resorting to attacks against the protocol such as BEAST. Apps that make calls to APIs over SSL and validate the certificate are in good shape as are browsing sessions which occur entirely over HTTPS.
Browsing sessions that begin over HTTP are not safe even if they redirect to HTTPS, for example if you simply type americanexpress.com into the address bar and the browser defaults to an unencrypted scheme (read about sslstrip if you want to know more). Webpages which load login forms over HTTP or embed them in an iframe within an HTTP page (even if the login page is HTTPS) are also at risk as the original HTTP request can be manipulated to load any other content an attacker desires (such as a rogue login page). Authentication cookies not flagged as “secure” and sent over an unencrypted network also pose a serious risk.
The Pineapple can detect probe requests for WPA protected networks but devices looking for them won’t automatically or even manually make the association if you try it that way. You’ll see the names of secure networks listed in the device’s Wi-Fi settings but that’s it – the initial authentication handshake won’t occur and the device won’t connect.
In this case, Wi-Fi security isn’t about protecting the network from unauthorised access nor is it about protecting any given client’s data from monitoring by other clients. This is entirely about not leaving the device in an insecure state long after the association with the network in question has ended.
Summary
What all this means is simply this: if Apple helped you set your device up or provided you with support in the store it’s now exceptionally easy for an attacker to monitor and manipulate the majority of internet traffic that passes through it. So long as an attacker can get in range of the wireless (and I’ve already done it accidentally and with good intent on multiple occasions), they own your device.
Obviously this was all tested on devices that had been through the Sydney store (this was the most likely source of the one I observed at the conference on the weekend). I don’t know how other Apple stores in other locations handle the situation described above, but given the carbon copy design, staff and experience in stores across the globe, I’d be surprised if the practice differed.
I’m still a happy iPhone and iPad user. My wife is a happy Mac user. There is nothing about the products per se that is insecure with regards to the information above, it’s simply an in-store process which leaves them vulnerable. It’s also easily rectified by simply putting a password on their wireless – any password and the devices won’t be fooled into connecting to rogue access points in the future. I know that doesn’t make for as slick an experience as it currently is for customers, but it’s the only way to solve the issue short of the staff manually removing the connection again at the end of the session. Unfortunately, all this is also only any good for new devices and I’ll wager that as of right now there are thousands of devices in Australia alone that have been left vulnerable.
Disclosure
Yesterday I contacted Apple and shared the risk regarding their in-store practices:
Recently I've learnt that customers are receiving support for their Apple products in store with the help of Geniuses who connect their devices to unprotected wireless networks, from my experience named either "Apple Demo" or "Apple Store" (certainly this is the case in the George St store in Sydney). The association to a network with no security then leaves the devices vulnerable to inadvertently connecting to rogue access points which respond to probe requests the devices send out specifically looking for the presence of an insecure network it has once known.
In short, when a device leaves an Apple store after having been connected to an insecure network it is now at risk of an attacker hijacking internet traffic. This is a trivial process and easily exploited by those with malicious intent. I've observed this first hand with my wife's MacBook Air and my own iPad as well as observing other Apple devices exhibiting the same behaviour.
Your review and comments would be most appreciated.
I’ll update the post with any responses.