I’m pushing the “Publish” button on this just before I go on stage at Web Directions Code because all things going well, what I’m going to talk about in this post will form part of my demo about securing web services.

I’m making some (admittedly very simple) code available and providing some resources that will hopefully help everything I talk about with regards to unprotected wireless traffic make sense. I’d like to begin by introducing you to Pineapple Surprise!
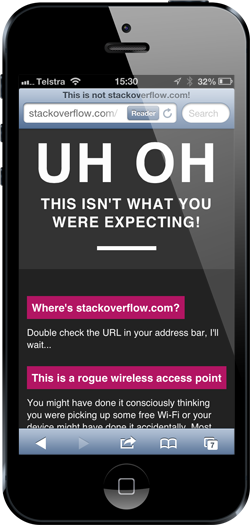
Wait – what?! Where’s my Stack Overflow?! I mean I’m seeing stackoverflow.com in the address bar, what’s going on here?! It gets worse:
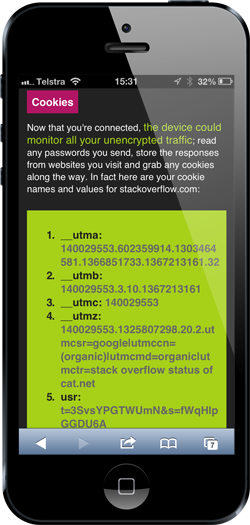
That little usr cookie down the bottom – that’s the money shot. Create a cookie in the browser with that name and value while the session is active (yes, it has expired just in case you were wondering) and wammo! You’re now me on Stack Overflow. You can go and respond to every security question about encryption and tell them to use ROT13, you can abuse Jon Skeet for not knowing his covariants from his contravariants and you can respond to any question about “How do I use ASP.NET to…” by telling them to use SharePoint. Except it’s not you saying that, it’s me and I’ll cop the abuse for it.
Let me explain what’s happening here.
All your Wi-Fis are belong to the Pineapple
This is all the work of the Wi-Fi Pineapple which I initially wrote about a couple of weeks back in The beginners guide to breaking website security with nothing more than a Pineapple and then again a few days ago in Your Mac, iPhone or iPad may have left the Apple store with a serious security risk. It’s this little guy here:
You can go and read the detail in those posts so I won’t repeat too much of it here beyond saying that this little device can trick trusting phones, tablets, laptops and anything else that can auto-connect to an open (i.e. no Wi-Fi password) known Wi-Fi access point (which is pretty much everything) into connecting to it instead. What many people don’t realise is that their wireless devices are constantly sending out “probe” requests looking for networks it has previously connected to (secured or not) and would like to connect to again. Just walking around yesterday morning with the Pineapple resulted in 315 unique SSID’s being probed for, sometimes by multiple different unique MAC addresses (the amusing ones are in bold):
#HKAirport Free WiFi, #WiFi@Changi, @yvrairport, _FREE Wi-Fi by inlink., 120wire, 14 Stewart Gibson Place, 2WIRE361, 474Labs-N, 4ten.net, ABC_PSK, ABC_WIFI, ACCESS-StarHub (2 MACs), aconex-wifi, AdshelWifi, Airport Free Wifi, ajfisher, allen, Anchors Aweigh, AndroidAP (3 MACs), AndroidAP5, AndroidHotspot1982, AnthB, ANU-Access, Apple Demo, Apple Store (3 MACs), Auckland Wi-Fi @ Tomizone, Aussieville, AUVIC-AEGIS-WIRELESS00, Axiom 5, B715 (2 MACs), BAIADAWL03, BAIADAWL04, BALoungeWiFi, BAMBI, bazillion, BBY Guest, BigPond022391, BigPond1D0761, BigPond47C6, BigPond4C0F55, BigPondD3DFA4, BigPondD7E713, BIPAC, BLERG, BlingBlingNet, Bliss, BO-AP03, Bordo, Brayza, BTHomeHub2-7J2T, BYOD, Cafe Caldera, CafeScreen_Free_WiFi, camphone, CCLA-HOTSPOT, Centre Wireless, chelagarto, ChinaNet-E3Ex, ChinaNet-Starbucks, ci+reactor, CiscoA4309 (2 MACs), CITWIRE, COKE Zero FREE WiFi, Colonial-One, Connect Free WiFi, Connect2UoM, Crush, Dan's White 64GB 4S, Darling Harbour Hotel2, db155, deblank, deblank2, deblanks, default, DEL C:, devgeeks (2 MACs), DH Studio, dh-int2, DigProd-Mixed, DigProd-N, DJ_Corp, dlink, Dodo, Dragonfly, DrayTek, DWLaptop, E583C-27a3 (2 MACs), Earth-shattering Kaboom!, Eden, Elfin, Emerald Hotspot, f9sml9fX, Fanta Wi-Fi, Finch, FinPa New Media, Flightfox.com, FLOATdroid, fluffyland, fontenayDL001, Four Points by Sheraton, Free wifi (5 MACs), free-hotspot.com, FreeSkydeckWifi1, FRITZ!Box Cubitt, Fuck-Off, FWMM2, FWMM2-guest, GAGAWAVE, Galactica, Galactica Guest, Gareth Edwards...s iPhone4, GoogleGuest (3 MACs), hahd.fr (Cette), Havana, Hertzpert, HH-GUEST, hhonors, Holiday Inn Public Wireless (2 MACs), HollerWF, home, home2ng8wlanv, HOTEL BRUNY FREE INTERNET, Hotelpuri.com, Hotspot-TXL, HTC Portable Hotspot (2 MACs), Hypnotoad, ibahn, Ibis, ii005745primary, iMac G5, Inspire9 (2 MACs), inteddies, Internode (2 MACs), Io, iROOM-Akama 2, ISIS, J and P, j74eX5drDdgf, James's iPhone, Jason, JOHNDEBLANK-PC_Network, JScamp2012, JSConf EU 2012, Kevin Yank...s iPhone, KINWOWLAN (2 MACs), KIT-GUEST (2 MACs), kylevermeulen, L n J, LAX OneWorld Lounge, LAX-WiFi, Link (2 MACs), linksys_reception, linuxconfau, Little Shed, LittleWireless, lovenest, LtBourkeSt, Luana 1207, Macquarie Public, MagicJohnston, Marty McWiFi, MAXSPOT, MAYA, McDonald's FREE WiFi, Melbourne Virgin Lounge, meteorology, metguest, Metro Wifi (2 MACs), met-wlan999, Miller Street Brewery Mobile 4G, Millhood, mka-27784, MOBILE, mojito, monstrouswifi, Mort, MOTOROLA-E5BE7, Movistar-Vex, Mozilla Guest, MPLUX AirPort, MRC-Guest, MTH Functions (6 MACs), museumcg, museumpublic, NDABBAYE, NetComm Wireless, NETGEAR (2 MACs), NETGEAR2, Nexus, no-one here but us chickens, Norah Han...s iPhone, Novotel-Canberra, NPS Wireless, ntegrity.com.au, Ogilvy_Melbourne, OgilvyWiFi, OptimusPrime, Optus E583C f0b5, OPTUS_B1, OPTUSA82B5A1, OptusCD3_365c80, OPTUSV6FF126, OPTUSV8D64B0, Other... (2 MACs), PalaceMeetingRooms, Panasonic Display1, pandy, password: ken sent me, Patient, Pegasus, pgh-wireless, Pluto, Porto, Porty Extreme, pp, PP-AP, Pretty Fly For A Wifi, Pretty Fly for a WiFi..., Prometheus-2-4, public, Qantas Free WiFi, Qantas-Lounge (2 MACs), QANTASWebConnect, RAMMMOODIEWLAN, RCSWIFI_1, redlea (2 MACs), Residence du Rougier 1, rhapsody (2 MACs), Ricky...s iPhone 5, RMIT, Robot, roomlinx, ROSENEATH_WIFI, rtw, Scarlett Extreme, Sceptre, ScottiePippen, Seaport Wireless, SFR_E8C8, Shanghai_Wireless, Sherwood Forest, SH-Wireless, SJS, sky-free-e872b5, SKYMESH, Skynet Global Defence Network, Skynet mobile defence unit, Skynet Mobile Unit, SOH_Guest, SpeedTouch913EE2, Squareweave - We build web apps, squiz.net, State Library of Victoria, StormsEnd, studiocea, Subaru_Customer_Lounge, Super_Dragon, SuperDragon, T1 Free wifi by SYD, t1fg, TASSWEB Wireless, Telecom wireless hotspot, TelerikAPAC, TEWM_0A7E0B, The Lounge Sydney, The Office of Marketing, THE PARLOR (2 MACs), thebrook, theinterweb, TheOffice, thisismyhouse, ThousandPoundBend, tobyandloz, Tomizone @ Movenpick, Tony le Pony, trust me, TULIP (4 MACs), Tygwyn1, UConnect, ULTIMATE-4F77, ULTIMATE-Rhapsody, UniWireless, vanessa's Network, Ventura_Free_WiFi, Verizon MIFI4510L 2412 Secure, vermeulen, Victoria Hotel, VirusProwler, W3710, WANADOO-6058, Wards, Wayport_Access, wdc-a, wdc-b (2 MACs), weatherzone, webteam (2 MACs), webteam2, WIFI@CintaAyu, WIFI@CintaTerrace, wilnet, winboard, wireless, Wireless@SG (3 MACs), wireless01 (2 MACs), WLANadmin, wlan-ap (2 MACs), WME, WME iinet, WME Wireless, www.koodoz.com.au, Xperia S_284e, YBF-b, Young Henrys, Zentrum_Der_Macht, ZyXEL
Tricks are one thing, but it can also act is a normal Wi-Fi access point which people connect to of their own free volition; see an SSID called “Free wifi” – sounds good, let’s go! Once you’re connected, you’re in a whole world of trouble, at least you are if you visit any websites that don’t implement sufficient transport layer protection. And that’s the real story here – unprotected Wi-Fi traffic.
What you saw in the screens above is the work of dnsspoof which in simple terms, was able to intercept the request for stackoverflow.com and rather than routing it to their server, routed it to the web server running in the Pineapple instead. The screens above were served from the Pineapple in response to the Stack Overflow request and in fact configured this way it will respond with that same page regardless of the site being requested, so long as it’s an HTTP request and not an HTTPS one.
What this demonstrates is that the Pineapple controls the traffic – anything sent over HTTP can be manipulated with clever software, including where requests are routed to. Now let’s imagine that there is no DNS spoofing and the Pineapple simply passes requests through to a network bridge and out over an internet connection. It might look like this:
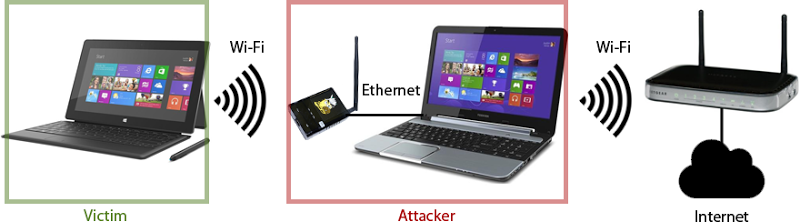
What this means is that the Pineapple and the attacker’s PC it’s connected to now control the unencrypted traffic. Anything sent over that connection – including Stack Overflow’s cookies – may be intercepted by the attacker. As you’ll see in the demo while I’m on stage, that is a very serious security risk.
What’s the risk?
I mean it’s just some cookies, why should you care? Let’s go back to the basics for a moment which means understanding what SSL is about and it boils down to three things:
- Assurance of identity – only the legitimate owner of the site should be able to serve up a certificate for it
- Integrity – the content moving backwards and forwards over the connection can’t be manipulated
- Confidentiality – the content also can’t be eavesdropped on
It’s that last point that most people associate with SSL and they expect passwords and banking info to be kept from prying eyes. But there’s other info that needs to be protected as well and it’s not as immediately obvious. Should the demo gods be kind to me, the audience will see one simple request to a Stack Overflow API appear on the attacker’s PC. It’s a request to the up-vote service and along with the request is the authentication cookie used to identify the user. Because it’s sent over an unencrypted connection it can be intercepted and once it’s intercepted then the session can be hijacked. The attacker will simply recreate the cookie in his browser (that’ll be me) and badaboom – they’re logged on as the victim!
One thing I do want to point out is that the guys at Stack Overflow understand this intimately. As I’ve written before, these are without doubt some of the smartest developers on the planet and they’ve made a conscious decision about the risk versus benefit of SSL. They know exactly what they’re doing. In fact Nick Craver wrote a very good blog post just last week on the road to SSL where he outlines the sort of challenges they need to overcome in order to secure the transport layer. As you can read in this question, clearly there is an intention to make Stack Overflow SSL only so that’s a very positive move in the right direction security wise.
Get Pineapple Surprise! on GitHub
I want to make the implementation of this freely available to the community in part so that others can take it and adapt it (contributions are welcome!) and in part so that it’s clear that despite the obvious opportunity to do evil, it’s not doing anything nasty. You can find it on GitHub here: https://github.com/troyhunt/PineappleSurprise
Told you it was rudimentary! The index page merely replaces the default one on the device that did nothing other than a client-side redirect by meta tag to redirect.php. Replacing the existing index page keeps the URL clean – whatever resource is requested is served over that URL.
There’s some logging that happens right up front in the file but it is very, very consciously only grabbing info that would be logged by a webserver anyway: time stamp, requested address, HTTP accept headers (to identify whether it’s an API call or a browser call), the IP address of the device (helps for looking at associated requests and the user agent (should give you an idea of the client being used).
What’s not logged is far more important and that’s cookies. They’re reflected back to the screen as you can see above, but they are absolutely, positively not logged anywhere and for those that did (do?) come along to my talk, the reason will be crystal clear.
tl;dr
Secure your web services! Anything you don’t want an attacker observing or manipulating needs to be sent over HTTPS and that includes auth cookies. Oh – and turn off your Wi-Fi in public!