As part of my general wish to be a good netizen and advocate of website security, I made a responsible disclosure the other day, you know, the kind where you privately email an organisation and pass on security flaws in their online presence that they might not otherwise be aware of. Anyway, the response was, well, you decide:
To date we've not had a single security issue stemming from [insert risk I sent to them here]
Really? Not a single one? Clearly whatever defences this particular organisation has in place is akin to Lisa Simpson’s tiger repelling rock:

Lisa: Dad, what if I were to tell you that this rock keeps away tigers.
Homer: Uh-huh, and how does it work?
Lisa: It doesn't work. It's just a stupid rock.
Homer: I see.
Lisa: But you don't see any tigers around, do you?
Homer: Lisa, I'd like to buy your rock.
Or in other words, absence of evidence is not evidence of absence. Not knowing you’ve had a security incident is not the same as not having had a security incident and there are some interesting precedents that illustrate this rather well.
Specious reasoning
See if this resonates:
Specious reasoning is an argument which seems to be followed by and described with valid points, but which is in reality misleading or false. The proof used in these lines of reasoning are often speculations that could be possibilities but are in no way actually backed up by any evidence or truth. Specious reasoning can give great comic effect and is used often in television and movies to add levity to caricatures of conspiracy theorists and cast members that are meant to be viewed as ignorant or uneducated.
That’s pretty much the argument of never having been hacked – speculations that could be possibilities but are in no way actually backed up by any evidence or truth.
Update: 22 September 2013: One of the sources I originally used as a reference in the remainder of this post has since changed the wording of their article at the subject's request. Consequently, I'm redacting the individual's name and their company.
Let me give you another example related to my piece on [redacted] a few months ago. [redacted] sought feedback from their technical director who stated:
[redacted], technical director and one of the founders of [redacted], said there had never been a breach of a customers’ bank account as a result of poor security on the site.
Ok, I also read the bit about specious reasoning giving “great comic effect” but c’mon, this is just ridiculous! This was in response to my writing about numerous deficiencies in their HTTPS implementation after their Twitter account espoused the efficacy of some pretty mediocre practices. When insufficient HTTPS implementations are attacked it’s by a man in the middle or in other words, an attacker compromising the transport layer. That might mean the sniffing of wifi traffic or other similar attacks that are absolutely nowhere near the server itself. An attacker does not leave a helpful note somewhere after intercepting unprotected traffic – there are usually no obvious indicators of compromise.
Words such as [redacted]’s are nothing more than an attempt to build confidence without any basis of evidence whatsoever on which to do so. Of course he could have said “We are not aware of any previous breaches of customers’ bank account” but that doesn’t sound quite as convincing, does it?
The thing is, no matter how confident you are about your security position you cannot emphatically say that you haven’t had any breaches. Not convinced? Let’s look at a couple of examples that illustrate this.
Advanced persistent threats
Last week there was an article in Secure Computing Mag about 182,000 accounts at investment research company Morningstar being compromised. Unfortunate, but not uncommon. This statement, however, is rather interesting:
An intrusion in April 2012 is thought to have compromised the Morningstar Document Research, formerly 10-K Wizard, which provides a global database and search tool to the company.
What?! That’s 15 months ago and they only know about it now?! Had someone from Morningstar been asked about their security position during those 15 months in the same way [redacted] from [redacted] had been, how do you think they would have responded? Exactly.
Back on SC Mag again, in May they reported how hackers may have had access to resort's credit card system for eight months. This time it was Callaway Gardens and the resort unfortunately had some nasty Malware running for some time:
According to a Callaway Gardens spokeswoman, the breach started in early September.
Now keep in mind that this is malware – malicious software running on one or more compromised machines – the sort of stuff that’s often not overly difficult to detect (with some notable exceptions). Certainly it’s generally more overt than sniffed network traffic yet Callaway Gardens didn’t know it was there until well after the damage had already been done.
Advanced persistent threats (or APTs) are a well-established phenomenon and Wikipedia summarises it nicely:
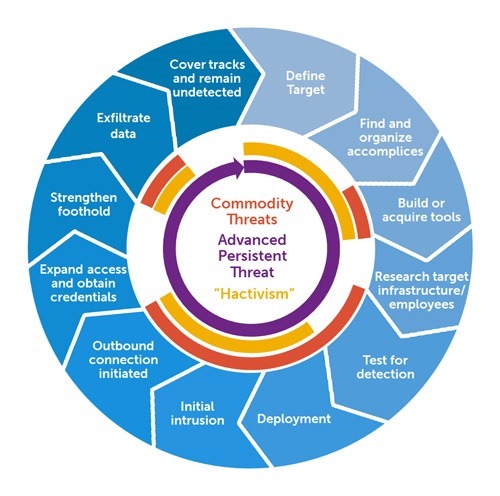
They also refer to a recent report from Mandiant exposing cyber espionage originating in China where they make the following findings with regards to APTs:
In incidents analysed by Mandiant, the average period over which the attackers controlled victim's network was one year, with longest – almost five years
That’s not too inconsistent with the previous SC Mag articles – about a year, give or take, before the victim actually realises what’s going on. If they ever do.
Ignorance is bliss (at least until complacency gets you pwned)
The attitudes described at the beginning of this post – the one about never having had security issues stemming from a risk then [redacted]’s from [redacted] – are dangerously wrong. They breed complacency and demonstrate arrogance in the sense they imply that if these individuals are not aware of a breach then surely they could not have occurred. Specious reasoning indeed.
More than just ignorance to the basic mechanics of how website attacks often work though, these responses demonstrate a dangerous level of ongoing complacency. In the example from the opening paragraph of this post, the website in question stores plain text passwords in a cookie, doesn’t flag them as HttpOnly, has XSS flaws, emails passwords in plain text, locks out old credentials on password reset, emails a persistent short password of limited character set on reset, has mixed mode HTTPS flaws and sends the session ID over insecure connections. They know this and deem it acceptable. They hold personal data. They handle credit cards.
But don’t worry folks, they’ve not had a single security issue. To date…