A couple of Saturdays back I spent a day down in Melbourne at DDD doing the usual combination of showing people some of the ridiculous stuff we’re doing on the net in relation to privacy, how we as developers are building some woefully insecure apps and generally making everyone depressed about the state of web. I do mean that in a constructive way though and indeed that’s the entire premise behind the Hack Yourself First courses I’ve been writing; see what it is we’re doing wrong, understand how it’s exploited – I mean actually exploit it yourself – then learn the secure patterns.
I did a workshop in the morning which went off just great. A few dozen people got to pick up some fundamental security concepts and experience things first hand which may have been familiar acronyms yet foreign concepts, at least in terms of actually understanding the mechanics and being able to execute it themselves.

XSS for example – using my faithful deliberately insecure website, everyone got to actually construct a cross site scripting attack then set forth on one of a number of “Hacker Challenges” that got them moving beyond alert boxes and actually doing something genuinely malicious with this attack.
Same again with SQL injection – everyone got to have a play with pulling data from a system that in theory, should never have seen the light of day. Now something like SQLi is the kind of thing that can get you into rather a lot of trouble if you go testing the boundaries of injection on live websites so having a “safe” playground where everyone could experience this firsthand was a real boon for the participants.
Here’s one bloke (sorry mate, name escapes me now!) who got a very good firsthand experience of just how important security on the web is. During the SQLi workshop he put his hand up and explained that someone had already destroyed the site and it was no longer functioning correctly. Ok, that’s possible, but it didn’t quite add up so I took a look at his machine and saw…
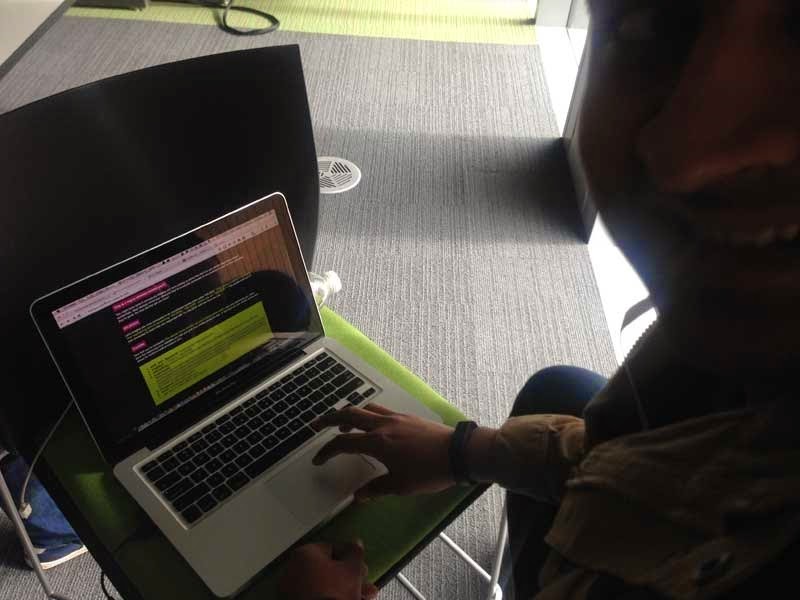
That’d be Pineapple Surprise, my little DNS spoof page that runs on the wifi pineapple. Old mate’s Mac had decided to connect itself to the Pineapple I had running while preparing for the locknote and every single insecure request he was making (i.e. HTTP and not HTTPS) was serving a page that explained his connection had been hijacked. He seems happy enough in the pic and certainly it was a lesson he’ll not forget any time soon!
I also did the locknote at the end of the day, a session not dissimilar to some of the others I’ve done recently in other parts of the world, although there’s always topical issues to cover so plenty of new material too. The good folks at SSW kindly recorded the whole thing and you’ll find it here:
Now – a little clarification with regards to the exercise Sarah did about the 24 minute mark: This was not actually in the plan:
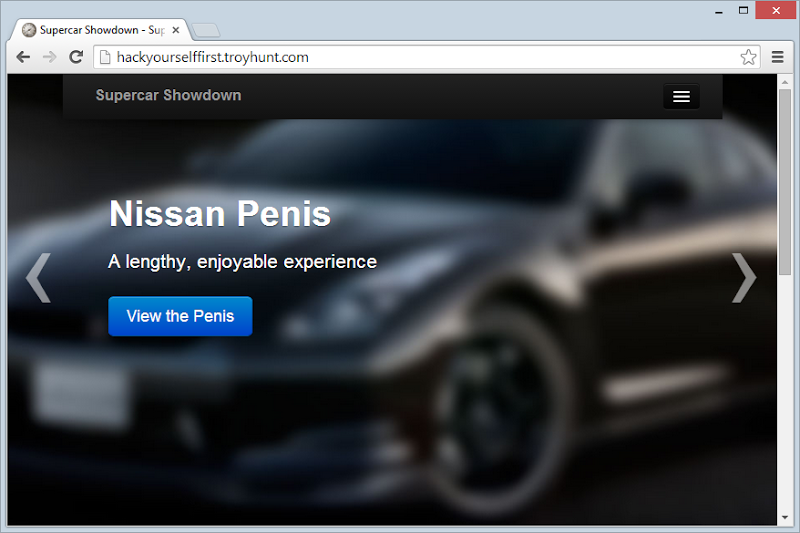
I’ll be honest – I’ve never been so proud to see penis on a webpage before. No really, some enterprising soul from the earlier workshop had gone well and truly above the call of duty and figured out how to run update statements across the database. As you may have noticed in the video, when I got Sarah up on stage we had the Aston Martin Penis, the Nissan Penis and the Pagani Penis, all of which professed to be both lengthy and enjoyable experiences. I didn’t realise when it first came up on the screen, I was just running through my usual well-rehearsed process and not paying much attention to individual words. The penny finally dropped when Sarah clicked on the button to view the Aston Martins (I hope my reaction then is sufficient defence!) and if ever there was a good example of how a little SQLi vuln can catch you off guard, this is it!
On a serious note, I want to set some context around the workshop and the intent of teaching people to “hack”. The workshops I do of this nature are targeted at developers, many of whom don’t know their XSS from their CSRF from their XFO. This is not unusual, indeed it’s the norm and it goes a great way to explaining why the web is in such a vulnerable state today. Security, by all accounts, is simply not a concept that’s consistently understand well enough by developers.
Anyway, the whole point is that workshops like these give developers an opportunity to look at security from the other side – the attacker’s side – and experience firsthand what it means to break through website defences. They mount SQL injection attacks (as is now obvious from the screen above), they learn the mechanics of XSS and they get to do a bunch of stuff that’s not only fundamentally important in their software development careers, it’s also surprisingly satisfying when they break through a hacking challenge.
I’ll be doing a lot more of these in the future so stay tuned!