This was always going to be a huge incident given not just the scale of the number of accounts impacted by the Ashley Madison breach (well over 30M), but the sensitivity of the data within it. However the interest has surprised even me – I loaded the breached data into Have I been pwned? (HIBP) about 8 hours ago and I’m presently seeing about 30k visitors an hour to the site. I’ve had a commensurate number of media and support queries such that I just can’t respond to them all individually so I’m putting together this Q&A instead.
One very important point first: HIBP will not expose any Ashley Madison data to the public. I wrote about this last month in anticipation of the Ashley Madison data being leaked and I stand firm on that today. Even though there are now multiple sites making it easy for anyone to check any email address, as someone very aptly said yesterday “you don’t want to be that guy” – the one who could be the channel through which information is learned that has a serious adverse impact on peoples’ lives.
Important 1: You’ll see a common theme in these answers which is this – I cannot do individual data lookups for you. The request volume has been huge and not only is it infeasible for me alone to run arbitrary queries, clearly it’s sensitive information which I’m avoiding getting involved in on an individual basis. I’m going to do my best to answer general queries that are helpful to as many people as possible.
Important 2: I’ve had a number of emails from very distressed individuals. If you need help, reach out to someone local.
Here’s the Q&A, I’ll continue to add to these as questions arise:
Q. HIBP says I was pwned – is there any way to see which site this was on?
It says it immediately under that notice, for example I was pwned in the Adobe breach so I see info about Adobe directly underneath the heading “Breaches you were pwned in”.
Q. I signed up to Ashley Madison with an email account I’ve since closed – how do I check if I was in the breach?
HIBP depends on you being able to verify your address by clicking on a unique link you’re sent via email. If you can no longer access the email account then you cannot verify that you own it and therefore you cannot check if you were in the Ashley Madison breach. This is for your privacy as well as for everyone else’s. An alternative would be to check one of the sites that’s making everyone’s address publicly searchable (I won’t provide links here for the obvious privacy reasons).
Q. I subscribed to notifications via HIBP and saw I was in the Ashley Madison breach but can’t see it listed when I consequently search for my email address.
This is intentional and it’s to ensure that you can only see Ashley Madison appear as a pwned site during the verification process. You cannot see it if you search HIBP again outside that context – this is to ensure that others also can’t see that you were in the breach.
Q. Can you tell me what other data of mine Ashley Madison had and has since been leaked publicly?
The only data HIBP holds are email addresses. Short of going back to the source data breach and filtering out your personal info ad hoc (which is not data I want to see on an individual basis), this is not feasible. If HIBP shows you were in the breach after you subscribe to notifications, work on the assumption that any information you gave Ashley Madison is now public.
Q. Do you know if [other data attributes] were leaked? For example private chats, photos, etc?
I’ll do a more detailed write up at a later date (as I’m sure many others are already doing), for now the only data attributes I can confirm are those I list in the “compromised data” section of the Ashley Madison entry on HIBP.
Q. I was a member on Ashley Madison but I can’t find myself when I search HIBP
Per the introduction to this Q&A, you will not find your email address against Ashley Madison if you search HIBP via the public interface. If you subscribe to notifications you’ll see whether you were in the breach or not after verifying your email address. A negative result means you were not in the “member email” table included in the data breach.
Update: searches also include all email addresses in the payment files.
Q. Can you please remove my email address so that nobody else can search for it?
You can only see that you were in the Ashley Madison data breach after verifying that you own the account. Nobody else can simply come to HIBP, search for your email address and find you in the Ashley Madison breach. Do be conscious though that people can do this through other sites which allow anonymous searching. At this point, attempting to remove your data from the internet is futile and you should consider how best to minimise the impact on you personally assuming anyone can now discover you were an Ashley Madison member.
Q. Can you please unsubscribe me from further notifications?
There’s an opt out link in the email that was originally sent for you to verify your account. If you no longer have this email, subscribe to notifications again you’ll get an email indicating you were already subscribed and containing another opt out link at the bottom.
Q. Can you check if my partner was a member of Ashley Madison?
The only way to check if an account was in the data breach via HIBP is to use the notification feature and follow the verification link that is emailed to the subscribed address. For obvious privacy reasons, I will not disclose the presence of another party’s email address.
Q. I can see my email address in the breach using the HIBP notification system but I never signed up to Ashley Madison – why is this?
There’s nothing to stop someone else creating an account using your email address. Any addresses that appeared in the Ashley Madison data breach were imported into HIBP so it’s possible to appear “pwned” but to have never visited the site yourself.
Q. I can’t login to Ashley Madison or reset my password using an email address that HIBP says was in the data breach – why not?
I’m not able to comment on why the Ashley Madison website wouldn’t function as expected in this regard, all I can do is make the email addresses that appeared in the breach searchable by verified users of HIBP.
Q. How do I now remove my data from the internet?
Unfortunately that’s simply not possible – once information has been sufficiently socialised and redistributed (which the Ashley Madison data has certainly been), the exposure is irretrievable. At this point it is better to focus on damage control – consider the impact of your Ashley Madison membership being known by everyone and what actions you might take in order to minimise the impact (i.e. discussing with a spouse).
Q. How come I still see my account as being pwned on Ashley Madison via the public search feature?
The public search feature feature will not return your presence in the Ashley Madison data breach. A separate paradigm within HIBP is a “paste” which is explained in detail on the pastes page. Being found in a paste may still result in a message like this:
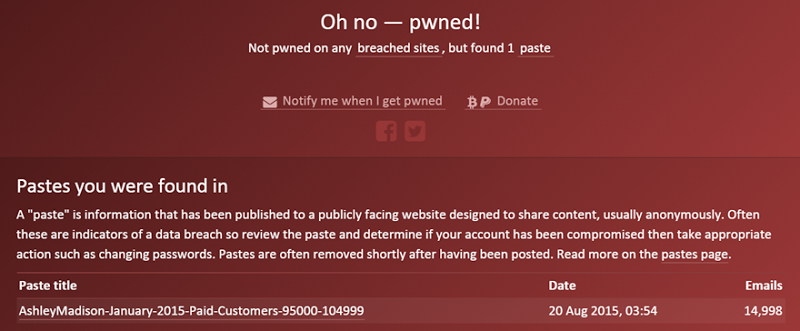
A paste is anonymously published data for which absolutely no verification is done. They are very frequently fraudulent and must be assessed on their own merits (i.e. view the paste and draw your own conclusions on the legitimacy). Email addresses are automatically imported into HIBP from publicly facing services like Pastebin and are not manually reviewed (there can be hundreds per day).
Update: This was causing too much confusion and shining HIBP in a bad light. I’ve now pushed a change to exclude all pastes that indicate they’re from the Ashley Madison breach. Subscribers will still get notifications, the only change is that the Ashley Madison pastes won’t show up when searching for someone’s email address.
Q. My email address says “pwned” – does that mean I was in the Ashley Madison data breach?
It’s important to read the information below the “pwned” message. My email address has been pwned:
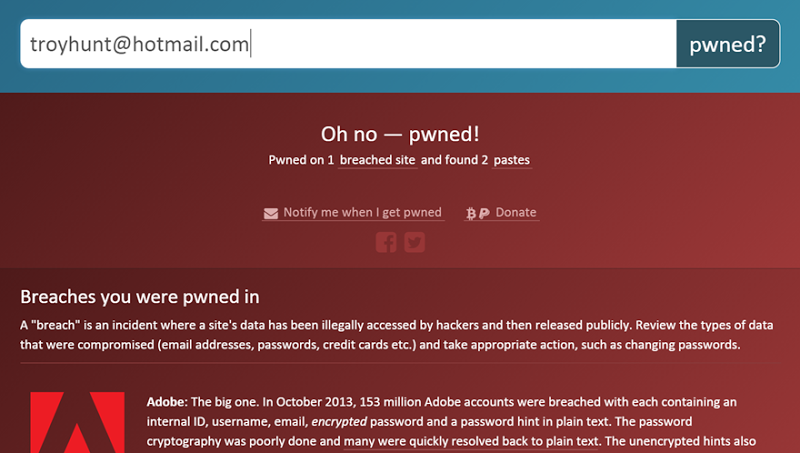
Clearly this is entirely unrelated to Ashley Madison. Any report of an account being pwned is always accompanied by details of where the account was pwned. Do read this information and consider which actual service HIBP is referring to.
Q. Does the appearance of someone’s email address in the Ashley Madison breach mean they were having an affair?
An email address alone could mean many things; the individual may have been curious how the service operated and never actually engaged with anyone else. They may have used the site years ago whilst not in a relationship. Their email address may have even been signed up by someone else. The presence of an email address alone is not indisputable evidence of infidelity.
Q. Are the email addresses on the payment records also in HIBP?
They were added at approximately 07:30 UTC on Aug 20, around 21 hours after the original data breach was loaded. There were 1,039,602 unique emails in these records that have now been combined with the 30,636,380 records from the original data breach. I’ll do an update of the total record count in the coming days.
Q. Why did I just receive a breach notification about Ashley Madison almost a day after the data was published to HIBP?
See the previous question about adding the payment records. After inserting these, breach notifications were sent to all subscribers who were in the 1M+ payment records and hadn’t already received a breach notice from the initial data load the day before. This resulted in almost 4k additional notifications being sent (the initial breach had 5k notifications).
Q. I wasn’t in the Ashley Madison breach when I subscribed to notifications earlier but now I’ve just received an email saying I am – why?
See the previous two questions on the payment records subsequently being loaded. Particularly where individuals used a different email address in the membership database to what they used for payment, a notification may only have been sent after the second set of data was loaded.
Q. Are people who paid by PayPal or Apple / iTunes in the payment files?
I’ve not analysed the contents of the files, only extracted the email addresses. If you can subscribe to notifications on HIBP and see the Ashley Madison breach against your email address then it was in the payment files.
Edit: The payment files all appear to relate to credit card transactions; they contain partial credit card information.
Q. Can I provide you with a link to torrents or enable you to download the data en mass?
No. Whilst the data is now readily discoverable online, I won’t be the channel through which it’s released publicly.
Q. Can I search HIBP by name?
No, searching by email is not possible because the notification system is used to confirm that only the owner of the email sees whether they were in the breach. I can’t implement that same functionality for a name search because there is no way of me verifying the owner so no, searching by name is not possible.
Q. Other search services don’t show my address as being in the breach but HIBP does – why?
I loaded the published email addresses into HIBP and made them discoverable by people who could verify they owned them. I can't speak to how other sites have handled them, it may simply be that they didn’t import the entire data set.
Update: I have now verified that other services I’ve checked are missing emails from the payment history files which is why a hit may be found in HIBP but not elsewhere. Absence of evidence in those services is not always evidence of absence.
Q. I want to monitor multiple email addresses on HIBP – how do I do that?
Just sign them up one by one on the notification page. If you have a large volume of individual email addresses you wish to monitor, there’s a link on the notification page to get in touch with me and I’ll bulk load (typically hundreds of email addresses).
Q. I’m in the Ashley Madison breach – what do I do now?
I can only give accurate advice based on what I know of the technical and security implications of the breach. How each impacted individual deals with the situation is very specific to them. If it was me (and this is as far as I can go with personal advice), I’d be talking transparently with my wife on the assumption that she will learn everything about my interactions on the site. In addition, I would be taking out identity protection from a service in my country of residence.
Q. How far back does the data in the breach go?
The earliest record of a member in the database shows a creation date of 17 January, 2002. The earliest payment record appears as 21 March, 2008.
Q. If I paid for the “full delete” service, is my data in the breach?
I haven’t personally verified this and can only refer to online reports. The Guardian is saying that the database suggests paid-delete option left identifiable data intact and would work on the assumption that all information ever given to Ashley Madison is now public, including any requests to remove that data.
Q. I never knew I had an account on Ashley Madison and I can’t get into it by doing a password reset – why not?
I can only speculate on how AM implement their accounts and reset features; it’s possible the account was deactivated or deleted at some time. The only thing I can have confidence in is that if you’re address appears in HIBP as having been present in AM then it was in either the membership database or the payment files.
Q. Have Avid Life Media’s other online assets such as CougarLife or Established Men also been compromised?
Whilst I have not personally seen evidence of these services being compromised, given the extent of the Avid Life Media breach including the release of source code for various assets (including Swappernet) and the CEO’s email, if I was a member of their other brands I would work on the assumption of them being breached. I also don’t know how much information is shared across their assets – for example billing records – but would make the same assumption of total compromise.
Q. Has any subsequent data been added to HIBP from the second or third public data dumps?
No. The subsequent dumps containing source code and the CEO’s email do not contain volumes of member data like the first dump did.
Q. I used fake profile details for my membership but may have been exposed in the payment files – what was recorded there?
The payment files recorded the amount paid, the type of card, the last 4 digits of the card (often used for identity verification on other services), first and last name, email address, physical address, post code, city, state, country and IP address. Not all records contain all data attributes.
Q. Can identity protection services remove my data from the web?
There are various things identity protection services can do to help defend against risks such as identify theft (i.e. monitor credit enquiries), but they cannot “remove your data from the web”. They may have limited success with removing some information from some places but they cannot, for example, have the torrent files which contain the entire Ashley Madison database removed. This information will forever remain in the public domain.
Q. I now have a different email address to what I used with Ashley Madison – can people still discover I was a member via background checks?
It depends on whether the email address you used on AM can be associated to your real name. Background checks will often look for different aliases or identities you may have used in the past and if that email can be matched to your name then you may be identified as an AM member. Matches may occur because you used the address on a loan application, signed up to online services with it, used it at a former place of employment or communicated with others using that address and your real identity.
Q. What website activity was disclosed in the breach?
The payment files have the users’ IP addresses and the membership database has a history of login by user. The attackers also claim to have user chats and messages.
Q. What is the most recent payment file included in the breach?
The latest payment file is dated 28 June, 2015. The last transaction in that file is dated just before midnight that day. All the records in the file have have contact information per the earlier files.
Q. Can other people get my information from other online services and will HIBP notify me if they try?
I can’t comment on the controls other services put in place. HIBP will not send any further notifications about AM unless more data is leaked by the hackers containing a new set of email addresses.
Q. I’ve heard that other Ashley Madison search services are publicly disclosing personal data without identity verification – can you share the links?
Given my approach with HIBP, clearly I don’t believe it’s responsible to provide absolutely anybody with the ability to locate anybody else within the AM breach. I’ve made a conscious decision not to redistribute these links; if you’re worried about your exposure and you’ve found yourself on HIBP after verifying your email, assume that everything you gave AM is now public.
Q. I would like to make a donation to HIBP but am reluctant to use PayPal – is there another way?
I have a Bitcoin address on the donations page and it’s either that or PayPal. When PayPal is used, payment happens entirely from their site and the only information I receive is an email with the details of the “buyer”. No information is stored on HIBP or any website other than PayPal.
Q. Ashley Madison have said they’ve deleted my account – is it really gone?
I have no way of verifying if AM have removed an account after the breach occurred. If you can find your account details by subscribing for notifications on HIBP then they had not removed your account before the breach occurred.
Q. Will it help if I now delete the email address I signed up to Ashley Madison with?
There’s very little that will do to help you, at least in the immediate term. It might stop you receiving solicitations from unethical identity monitoring services or any of the blackmail messages that are currently doing the rounds, but it won’t erase your historical association with the site. At best it might mean that by using a new email address in the future, people you later meet will not be able to search for you on public AM databases. However any half-determined investigations in the future (i.e. background checks), will likely still be able to make the association between your identity and your historical email addresses.
Q. Can the payment files be linked to the membership database if the latter used a manufactured identity?The payment files do not explicitly include record identifiers that can be linked to the membership database. However, both the payment files and the membership database include the users’ IP addresses. If the user had the same IP at signup as they did during a payment, the records could be matched with a high degree of confidence.
Update: The payment files appear to be using the “first name” to store an ID that reliably maps to the membership files. The “last name” in the payment files then contains both the first and last name. This was quite possibly done to enable an existing merchant system to track the mapping to members by persisting the ID in the first name field. The guidance above remains the same: assume that payment records can be mapped to membership records.
Q. I didn’t provide Ashley Madison with any personal information but I used my real email address – is there any way they could have got my actual info from that?
Not directly from your email account; they couldn’t take a Gmail address and pull your personal details out of Google. However, many services allow personal information such as real name and photo to be retrieved via email address, for example both Facebook and LinkedIn enable this. I haven’t seen anything to suggest that AM did this in order to populate their database, but it’s technically feasible.
Q. The attackers have advised they have pictures from Ashley Madison users – will they release them and will they be searchable via the public?
We’ve seen three torrents of data released by the attackers so far and they’ve proven very effective at disseminating breached data to the public. It would be consistent with their behaviour to date for more data to be released and it would also be consistent with the behaviour of some people (and organisations) – independent of the attackers – to then make it publicly searchable.
Q. Are Impact Team (the hackers) being pursued and can they be stopped from dumping further data? What’s being done to catch them?
Impact Team is being actively pursued by law enforcement. There is now a C$500,000 reward being offered by Avid Life Media for information that leads to their identification and assumedly, their arrest. Whilst capturing the perpetrators will likely stop the leaks of information, until that time it’s entirely possible they’ll release further information such as the private chats and photos they claim to have obtained.
Q. Is it wise to login to Ashley Madison and review what information is stored about me?
There is very little further harm that can come from logging back into the site. The login and browsing activity may be captured, but the vulnerability that lead to the data originally being leaked has almost certainly been rectified and any further leaks are highly unlikely within the scope of this incident. Whilst logging in may enable you to view some aspects of data stored about you (for example profile information you provide), other information such as full payment history and logs of your activity is unlikely to be discoverable.
Q. I used the same username on Ashley Madison as on other websites – what should I do?
If the username is generic enough and not likely be personally identifiable, I wouldn’t be too concerned given the ability for anyone to create an account with the same username. If it’s uniquely identifiable (i.e. a very unique first and last name combination), consider the impact that exposure on Ashley Madison may have. If concerned, change the username on other accounts or recrate them where necessary.
Q. How can I browse through the dumped data myself?
The data is not in a consumer-friendly fashion. It’s tens of gigabytes of database statements and thousand of CSV payment records. There are also false copies of the data on the web as well as malicious software purporting to be the AM data. It is strongly recommended that you do not attempt to process the raw data yourself.
Q. Should I pay a third party to retrieve my data from the breach?
We’re seeing very questionable practices from online services promising to provide data from the breach. Often the cost is hundreds of dollars to provide access to your own data. If you find your email address was present in Ashley Madison after using HIBP, I recommend working on the assumption that everything you provided AM is either now public. If not public now, it may become so in the future if additional data is released (naturally commercial services also can’t tell you what further leaks may expose).
Q. I tried to subscribe to notifications on HIBP but I haven’t received an email yet – what’s happening – is it delayed?
Verification emails are sent immediately upon subscribing, although sometimes there can be delays in you receiving it due to other latency on the internet or within mail services. If you haven’t received the verification email after a few minutes, check your junk mail and if it still doesn’t arrive, you can always subscribe again and it will resend the message. Occasionally, a mail server may reject email from HIBP entirely and not deliver it to your mailbox which is unfortunately beyond my control. All email from HIBP comes from the address noreply@haveibeenpwned.com
Q. Can other people find me within the Ashley Madison data by searching for attributes like my name or location?
Not via HIBP, it specifically keeps identities private to ensure personal privacy is not compromised. Other public sites have made this information searchable and whilst they’re often quickly shut down, other are regularly emerging in their place. Work on the assumption that you can be discovered by people searching for any data you provided to Ashley Madison.
Q. Can I pay you to show me what data was leaked for your identity?
I’m not doing specific searches for individuals’ data nor am I accepting payment in return for the services I’m providing (discretionary donations aside which have been on HIBP for the last 18 months).
Q. Will Avid Life Media or the authorities be successful in suppressing this breached data from the web?
Unfortunately, there is absolutely no chance of this data being removed from the web. It is too broadly distributed across too many services both in the source torrent form and through the continued emergence of online search sites. The data will forever more exist in the public domain.
Q. I have no idea how my email address got into the Ashley Madison database – can you help me?
It is near impossible to identify how an account was created with someone else’s email address. The IP addresses stored in the database may disclose where the account was created from but beyond that, it would be a case by case situation of trying to assess profile data and establish a possible source. This is highly unlikely to yield tangible results and it won’t change the fact that the email address is associated to Ashley Madison and discoverable by third parties. Unfortunately this is not something I can assist with.
Q. Does this hack spell the end of Avid Life Media?
Almost certainly “yes”. Not only is their reputation in tatters, they can not longer feasibly offer the same “discreet” service with this track record (although one week on, their website is still promoting this). They’ll be tied up in significant lawsuits for years to come and it also looks like they were involved in actively hacking competitors which could bring additional charges against the executives. It’s hard to see how they’ll still be operational in a few months time.
Q. Would it be possible for HIBP to return additional data attributes or indicate activities on AM?
I’ve very consciously kept HIBP to email addresses only. This is a long-standing decision to ensure I do not store anything of a sensitive nature.
Q. I’ve found a site or online forum publishing sensitive data from the breach – what can I do?
Start by looking for channels on the site to report inappropriate behaviour. You may also contact your local law enforcement or CERT, but it can be exceptionally difficult to have data removed, particularly when it resides in a foreign jurisdiction.
Q. Is it possible that a name and physical address could exist in the payment files without an email address?
I can’t speak to precisely what practices were used across many years of payment data. An email address is usually present, but it’s entirely possible that data rules may not always be consistent.
Q. What information was requested at the time of signup?
This is what is presently requested after choosing your gender and the gender you’re seeking:
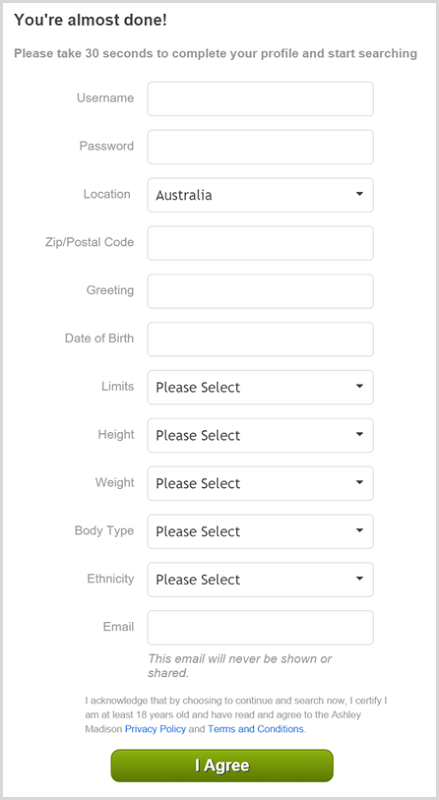
It’s entirely possible that different information was requested at different times in the past.
Q. Who can I trust that is reputable and can provide me with more information about my compromised data?
I’ve not seen any providers of this information that I would personally trust and many that are outright irresponsible, reckless or fraudulent
Q. If photos and chat message are leaked, might they be made available through public search sites?
Given the prevalence of sites already recklessly exposing the existing data that has been leaked, it’s a near certainty. Whether or not the additional data will be leaked is still not clear.
Q. Some notable news and blogging sites include links to search tools allowing you to find anyone. Why is this and how can they be removed?
There are different tolerances and views as to whether these sites should be shared. I’ve elected not to circulate them and remove any comments from this blog that include them. Others sites have elected to link to them or have not noticed their inclusion in comments. If you find a case that concerns you, contact the site owner and express your views.
Q. Do members’ names exist in the membership database as well as the payment files?
Yes, although no membership database records that were created after February 2004 appear to have valid values for the first and last names. The present signup form on the site does not ask for name so it’s possible this is reflective of a change in process more than a decade ago. All payment records I’ve seen have names and contact details.
Q. How are the maps some people have created showing the distribution of users made?
The most likely way would be to take the latitude and longitude from the breach data and plot that. Alternatively, they may use the physical address data or resolve the IP addresses to a lat and long. Either way, I would not expect the data to have a high degree of accuracy down to very localised areas, although it is probably quite representative of the spread of users in aggregate.
Q. Will HIBP still report my email address as being pwned if I closed the email account?
Yes, HIBP merely reports on what data was in the breach. If you signed up to Ashley Madison with an address and later closed it, HIBP will still report it privately to you on subscription verification as being pwned.
Q. What’s the latest data released by Impact Team and is any of it on Pastebin?
The last data released as of 18:00 GMT on August 27 is the email correspondence from the Avid Life Media CEO, also referred to as Dump #3. This appeared one week earlier. All dumps from Impact Team are signed with a cryptographic key that can be used to verify the authenticity of the dump. It’s highly unlikely any Pastebin releases are legitimate; data released there is often fraudulent and Impact Team have thus far only released data via their Tor hidden service.
Q. What should I do if I receive a blackmail email?
Just delete it. It’s an opportunistic attack and there are many being sent to email addresses in the dump. The ones I’ve seen are usually not individually targeted and given the volume, I doubt whether the extortionists will actually follow through on their threats of individually notifying significant others if demands aren’t met. Regardless of blackmail, the data is now public so work on that assumption and take appropriate steps (i.e. discussing with your significant other).
Q. Were passwords leaked in the breach?Yes, although they were exceptionally well protected via cryptographic hashing algorithm (bcrypt with a work factor of 12) so unless someone used a very weak password, it’s unlikely it will be cracked and resolved back to the original clear text version.
Update: On the 10th of September, a mechanism was disclosed that exploited weaknesses in the password storage mechanism rendering it near useless. The use of a legacy cryptographic function in conjunction with the stronger bcrypt implementation means that almost all passwords will now likely be cracked.
Q. I have an account on another site similar to Ashley Madison – what should I do?
This incident has taught us that your data on a website may be made public regardless of the assurances the site gives its customers. You should consider if you’re prepared for that to happen and if not, delete the account. Ensure that you receive written assurance that all data relating to your identity has been permanently removed; email address, physical address, IP address, lat and long coordinates and any payment records that might identify you.
Q. I have no idea how my email address got onto Ashley Madison – how could this have been possible?
Ashley Madison never verified that someone actually owned the email address in order for them to create an account that uses it. There are many examples of email addresses having been used which are certainly not valid. It’s possible that if your address appears in the breach and you genuinely had no prior engagement with the site that someone else signed up using your address.
Q. How many payment records were exposed?
There are approximately 5.652M payment records in the breached data.
Q. Why can’t I find my username in the Ashley Madison data breach?
Ownership of a username cannot be verified like an email address can be. In order to protect the privacy of users, Ashley Madison usernames are not searchable either by the public or by members who verify their email address.
Q. How were physical addresses of members obtained? Could they have been inferred by IP address or lat and long coordinates?
The physical addresses were almost certainly entered by users, either by giving them to Ashley Madison or via their payment provider. It’s highly unlikely that physical addresses would be derived from either IP address or lat and long as there would be a huge number of false positives produced by doing so.
Q. Does HIBP send an email to the person you are searching for?
No, not unless you’re explicitly subscribing the email address to notifications which you must do in order to search for a presence in the Ashley Madison data. Searching for an email address on the front page of HIBP does not send the owner of the address an email.
Q. I signed up to HIBP for notifications – will I be notified of future breaches and pastes and for pastes, how long after they appear will I be told?
Yes, subscribing will notify you of all future braches or pastes your account is involved in. On average, HIBP retrieves pastes within 40 seconds of them appear on sources such as Pastebin and an email is usually sent within minutes.
Q. How many accounts appear to have used the paid “full delete” service?
There are 185,948 accounts that have had their first name replaced with “<paid_delete>”. Personally identifiable data has been removed from those membership records, although the corresponding payment records still positively identify the individuals.
Q. When did the first paid delete occur?
The first payment record associated with a user who’s name is now “<paid_delete>” is from the 17th of April 2008.
Q. I’ve signed up to the notification service on HIBP and haven’t received any emails about pastes – does this mean there haven’t been any with my email?
It means that HIBP hasn’t seen any with your email. However, there are many, many sources where data is reproduced online via copy and paste that HIBP cannot monitor so absence of evidence is not evidence of absence. The paste service is useful for monitoring many common sources on the web, but the nature of this type of data means that it can never monitor all of them.
Q. Did the breach disclose any national IDs?
This is a data class that differs between countries (i.e. we have no concept of this in Australia) but from what I’ve seen, there is no facility to store this information anywhere within the data that has been released.
Q. Where can I find identity theft protection or credit monitoring services?
This is a very locale-specific question. In Australia, I personally use Veda. In the US, I’ve worked with mylife.com in the past and can vouch for their legitimacy although have not been a customer. Do your research in your local area and find a reputable organisation. I always use an identity protection service regardless of specific threats like the Ashley Madison breach.