As I’ve now widely publicised, I left Pfizer a few months back after 14 years with the firm. You build up a lot of dependencies over 14 years, a lot of access to systems and a lot of people who count on you. As I was preparing to exit, I made a bunch of notes in a draft blog post because firstly, as I recently wrote in How I optimised my life to make my job redundant, I find this helps me ensure I get things right. But secondly, this should be useful for others because we do tend to create a long tail of dependencies on us as technical people.
It’s not just about not leaving people in the lurch, mind you, it’s also about your responsibility to the organisation to ensure you don’t still have access to things you shouldn’t have. Ex-employees often have easy access to corporate data and really, it’s in nobody’s best interest for you to depart the workplace still being able to mess with their things.
With almost four months of corporate-free air now behind me, I’ve had zero cases of people needing me for knowledge, access rights or anything else to do with my previous job. Maybe I did a good job of the exit strategy, maybe people just forgot about me quickly or maybe it was a bit of both, point is it was a clean exit and I’d like to share the things I did which contributed to that.
My old machine – I hoped for the best and planned for the worst
You want to hope that your previously loved machine will be handled ethically and simply wiped, but I planned for it to be pilfered in the most obscene of ways. For example, you build up a lot of baggage over 14 years – try 71,141 sent emails for a start. Almost all of those existed in PSTs on the local machine along with who knows how many tens of thousands (hundreds of thousands?) of received emails. I permanently removed all of those from the machine before handing it back.
Same again for “My Documents” (the pronoun “my” is somewhat debatable on a corporate machine anyway) and other places I accumulated files. Yes, it was a corporate machine for corporate purposes but most people accumulate some things of a personal nature they do not wish to necessarily share with who know who. Now let’s be clear – all material of an ongoing work nature goes into shared locations – but I worked on the assumption that the machine would be nuked and anything of ongoing value to the org was moved off. Basically I left it clean of things I had received or created.
Of course there will still be backups of various files to varying degrees so this is not about “covering your tracks”, rather it’s about not consciously leaving things laying around in an easily accessible location. The machine might have been passed off to a helpdesk to be rebuilt or it might have been passed to a temporary assistant in there for a week to back-fill some paperwork. I don’t know, so I didn’t take chances.
Remove any backup email addresses
This is a really important one and with the benefit of hindsight, I probably wouldn’t create this dependency again. Let me how explain: I had my Pfizer address as an additional email on things like GitHub and Facebook, for example:
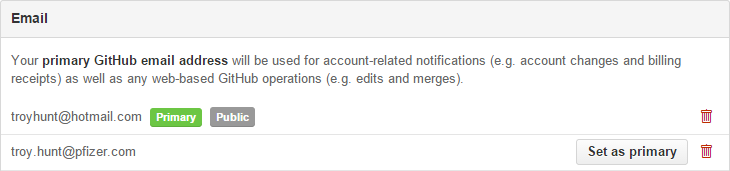
Controlling my Pfizer account meant controlling these assets (various services handle this differently but the “backup” account often serves as a recovery key). Whilst I have no reason to suspect anyone would abuse this, not only did I not want to take any chances, I wanted to put alternative backup accounts on them for the purposes of future recovery if need be. Think carefully about this fellow exitors – how many places have you spread your work address over that could actually give people controlling that account access to things you still own beyond the tenure of that job?
Remove any software with your keys
Inevitably this happens to many of us – we have personal software products with valid licenses that end up on corporate machines. All of the “There should be a corporate license” ranting and raving in the world won’t overcome insurmountable procurement problems with purchasing that $49 piece of software you can only get online. So it happens.
Obviously you want to get this stuff removed. Not only do you want to be sure it’s not now being used by someone else in ways it wasn’t intended to be used, many products also have central activation with a limited number of keys.
Disconnect auth’d accounts
There’s plenty of software you inevitably end up with that requires you to authenticate with credentials that will stick with you beyond your corporate role. For example, GitHub for Windows; I have a personal GitHub account and I obviously didn’t want anyone else having access to that post-Pfizer. There are cases where it probably makes more sense to create a separate corporate account on external services but this is frequently made very difficult (try setting up multiple accounts using 2FA with the one mobile number…) resulting in you using the one across both personal and corporate uses.
iTunes is a perfect example – it was part of our standard build (corporate iPhone users backed up via it) and of course you can sign in and manage various aspects of your iThings via there. I made sure all these things were well and truly disconnected before my exit. Yes, you’d have to login to the machine under my identity to actually have any access to these accounts but being ever cautious, that’s the assumption I worked on.
Get yourself out of public groups and ACLs
These days you cannot help but find yourself spread across all sorts of different external assets as part of your corporate duties. GitHub is a perfect example – I was in various teams that had access to Pfizer’s things and I had to get myself removed from those before my departure. Do make this happen before you depart too because you never know when you’ll have a dependency on your corporate email or someone inside the org in order to get you properly disconnected.
Azure subscriptions is another good example. There’s some serious stuff that can be done with access to an Azure account and I definitely didn’t want to be leaving with that hanging over my head. Besides, it’s a nice little guarantee that you won’t be called on to fix anything once you’ve moved on to other things :)
Cover your (browser) tracks
No, I don’t mean destroy the evidence of your misdeeds! What I do mean is to not leave yourself vulnerable by handing back a corporate machine with Chrome signed in to Stack Overflow, GitHub and Twitter. Whilst it would be a massive breach of trust (at least in my mind), it’s certainly possible that once that machine is back in the helpdesk’s hands they can reset your network creds, log back in as you and open up a browser with long-running sessions to services anyone would reasonably deem to be personal. Job-relevant, of course, yet still personal.
Sign out of everything and the easiest way to do that is to nuke all cookies and the browser history as well while you’re there (I frankly don’t trust all sites not to persist auth via the URL). Sign out of Chrome as well and de-auth anything under a personal identity.
To “out of office” or not “to out of office”
By pure coincidence, my wife left her job a few months earlier and summarily enabled her OOO with “Hey, I’ve moved on, here’s who to contact in my place” which to me, seemed like a perfectly reasonable thing to do. Until she was directed to hand over her account to her old boss which to me, seemed like a massively creepy, invasive and downright unprofessional thing to do. Yes, yes, I know it’s company property but let me explain:
Firstly on the company property thing: ownership of the asset should not give the owner total free reign to do what they will with it and privacy implications be damned. You employer owns the toilets – they do not have the right to monitor your movements there – see what I did? :) – and there’d be outrage if they tried. Yes, that’s a stretch from taking control of your email but the point is that there are reasonable expectations of privacy that supersede corporate ownership.
A corporate mail account should, of course, be used for corporate purposes. However, it’s your name on the account and the expectation that others have when they send email to it is that it goes to you and to you only. That others may send information of a personal nature or indeed, may send information about the person who has since inherited the account is beyond your control. In fact particularly in the latter case, if there has been any sort of dispute or grievance with the person who now receives the mail and now has access to the mailbox complete with Human Resources discussions, that could get rather sticky.
I bring it back to this: a clean exit means tying up your loose ends and leaving the place in a sustainable state which means also advising those not aware of your departure that you’ve now moved on. That’s what OOO does, at least until IT yoinks the account. Being forced to (metaphorically) hand over the keys to your account is a sign of failure on behalf of those orchestrating the handover process.
Oh – and I left Pfizer with an empty mailbox and OOO firmly on. Within about a day it started bouncing mail (I check these things!) so that’s that end well and truly tied up.
Summary
I had an entirely positive exit experience from Pfizer and that’s the sort of memory you want to leave with. If I hadn’t consciously done the things above it would have undoubtedly been harder. I also had the luxury of several months lead time to prepare things and inevitably if I’d been “marched” or had a very small window of time then things would have been hard. Plan in advance, leave a clean environment behind you and things can go very smoothly.