Day 16: The news headlines continue. Conspiracy theories keep emerging. The FUD evolves as people take further liberties with the truth (no mate, you didn’t get done by Heartbleed, you just chose a crap password).
A few days ago I caught up with Richard Campbell of RunAs Radio fame to talk about Heartbleed. You may remember Richard from such .NET Rocks episodes as talking security with Carl, Richard and Troy and Hacking yourself first with Carl and Richard on .NET Rocks. RunAs tends to be a more IT infrastructure orientated show but the thing about Heartbleed is that it really know no bounds; sys admins, devs and even consumers are copping it left right and centre.
This show panned out to be more about a couple of guys talking through how the bug and the security implications are panning out rather than being about what the Heartbleed bug is per se (read my post on Everything you need to know about the Heartbleed SSL bug if you want to know that). It’s about 33 minutes and you can grab it from the RunAs Radio site or listen to it here:
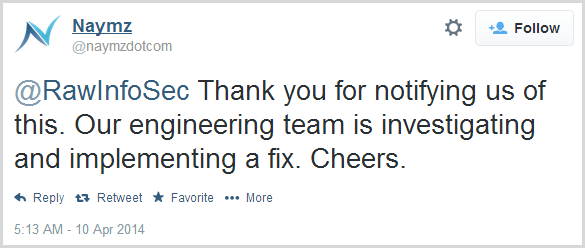
Oh – one more thing. You may be thinking “Wow, Heartbleed was bad but I’m glad it’s behind us now” and that would be a fair assumption as it’s such a simple bug to patch. Yeah, about that – as I say in the show, there’s evidence of a huge number of websites remaining unpatched. Let me give you one example here and it goes back to this tweet from RawInfoSec on April 10:
Naymz (they do social media management bits and pieces) responded a few hours later:
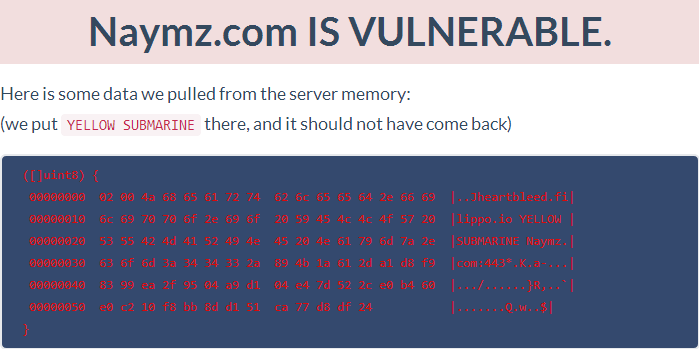
Fair enough, keep in mind that we first heard of this bug only a few days earlier. So how are things looking today almost a fortnight on? Let’s see:
Assuming this test is correct (and let’s face it, it’s dead easy to check it yourself and exploit a vulnerable system), you’d need to assume that all the data customers are sending to this site is easily retrievable by anyone with an internet connection and a few minutes of spare time on their hands. Guys – it’s more than two weeks already – you know your system is vulnerable and your customers are exposed, what on earth is going on over there?!
I don’t mean to only single Naymz out as they’re one of very, very many that simply haven’t worked out the severity or the risk to customers yet, but I do want to make the point that we’re still a long way from having this issue behind us.