How much really changes in only three short years in the world of application security? Ok, a few sites get owned and some nasty hackers come up with some new ways of making some poor developers lives a misery but that’s about the extent of it, right? Yeah, turns out it’s a lot more complex than that.
The very first course I wrote for Pluralsight and the one that continues to be the most popular is the OWASP Top 10 Web Application Security Risks for ASP.NET. This course is now an integral part of the security training for many organisations who have recognised that it kinda makes sense that their .NET developers know a thing or two about web security. This is an awesome course, but it has one problem: it’s written against the 2010 edition of the OWASP Top 10.
Now there’s nothing actually wrong with this in terms of the actual content and as you’ll read shortly, it all remains 100% relative. But it’s superseded by the 2013 edition and that in itself poses a problem as people feel like they’re getting out-dated info. So enter my latest course, What's New in the OWASP Top 10 for 2013. Let me tell you a little about it but firstly, let’s recap on just how much really does change in those three short years.
Contextualising three years of web security
That 2010 edition of the OWASP Top 10 hit in April four years ago. For a sense of just how much water has gone under the bridge since then, that was the same month as this guy was launched:

The iPad simply didn’t exist when the 2010 edition of the OWASP Top 10 was written. In fact as the forbearer for so many tablets that came after it, arguably the whole class of computing didn’t even exist back in April 2010. Now that may not actually have a big impact on web security per say (although it has certainly had an impact on the emergence of web based APIs), but it gives you a sense of time.
Here’s another one that’s had significant impact on the technology landscape: In April 2010, Chrome was at version 4 and it had about 8% of the browser market according to Statcounter. By the time the 2013 edition of the OWASP Top 10 came along in June last year, it was version 28 and had 43% of the market. Some people will argue the actual usage figures, but there’s no denying that is went from near obscurity to internet dominance.
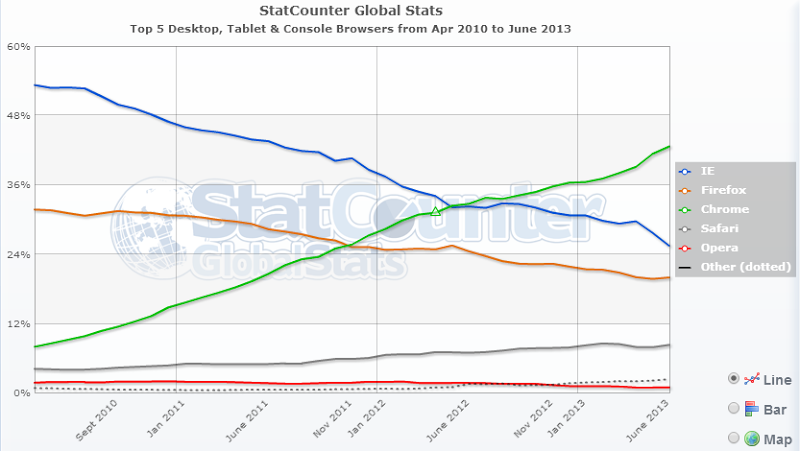
But let’s just focus on security for a moment – how about these guys:

Anonymous hadn’t yet mounted their campaign of “hack anything that moves” and whilst they existed in various corners of the web, it wasn’t until later in 2010 and Operation Payback that they really hit the mainstream. We hadn’t yet heard of LulzSec and most of the havoc they wreaked didn’t kick off until 2011. Arguably, the 2010 document was created before hacktivism was really even a thing, certainly before it was regular mainstream news and recognised as the threat we know today.
The other thing that really stands out about this three year period between Top 10 docs is the volume and scale of attacks. For example, here’s the number of attacks experienced each month according to datalossdb.org:
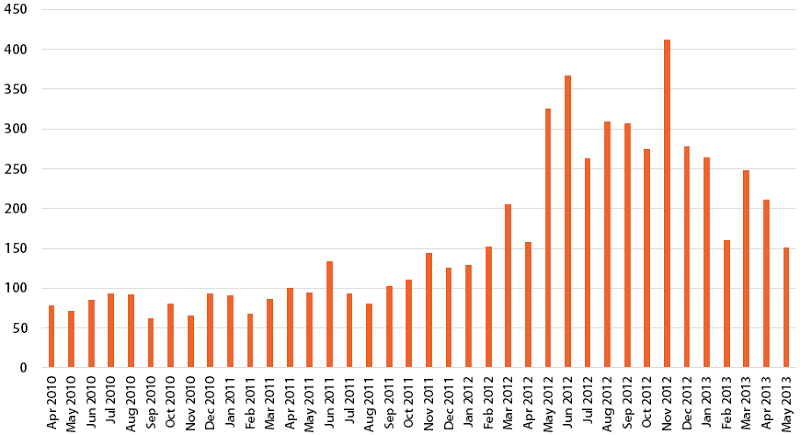
We went from less than 100 documented attacks each month to somewhere north of 250 on all but two months after April 2012. That’s a significant increase in the rate of attacks, but it’s actually worse than the number suggests:
2013 Data breaches exposed over 822 million records nearly doubling the previous record high, according to Risk Based Security
Not only are we seeing more attacks, but their scale is increasing. Of course this is now talking about the entire period of 2013 and that includes the likes of the Adobe and Target attacks, but you get the idea.
Hopefully that gives you a sense of just how much things are changing, let’s move on and take a look at the new course.
About the 2013 edition and the new Pluralsight course
As you can see from the table of contents, I’ve broken this course into four modules:
- Introduction: Background on what’s been changing in the industry, the impact on data breaches and how the OWASP Top 10 evolves in response to the environment
- Understanding the Risk Assessment: This is actually really good info for understanding how risks are assessed (there’s a science to it, y’know?!) both for the Top 10 and how you can do your own risk assessments in your apps using the OWASP methodology
- What’s Changed in the Top 10: This is the key info in this course as it goes through each of the Top 10 and explains how it’s changed since the 2010 edition and what the drivers for the change were
- Additional Risks to Consider: This goes beyond the Top 10 and looks at risks that didn’t make the cut as well another very valuable resource, the SANS Top 25 Most Dangerous Software Errors
I wanted to make sure there was enough new content in there so that people who’ve watched the original OWASP for ASP.NET course can take away things they wouldn’t have seen before. But I also wanted to ensure that when both of these courses are done – the 2010 and the 2013 – that it left people feeling they had a really comprehensive view not just of the current state of security, but of how it changes over time. Sometimes these changes are actually reflective of our good work – we’ve gotten much better at CSRF so it dropped three spots down to position eight. I hope the previous course is maybe even just a little bit responsible for that :)
Who’s the course for?
The 2010 course is very in depth – over eight hours of deep code level training for people working in .NET. This was only ever going to make sense to developers (my Big Picture course is much more broadly consumable) and then mostly to those working in Microsoft’s web world.
This course is only an hour and a half and there’s no code, rather it focuses on describing the changes in the environment and the way the risks are assessed. Because of this, it also works across technology platforms. If you’re a PHP guy or gal and you’ve already got a grip on the 2010 edition, this is equally relevant to you as it is to your Microsoft brethren.
If you’re new to these courses, do them both. No really, you need the depth and detail that’s covered in the first ones as this is where the risk is demonstrated first hand, the fix applied and then the secure position shown. That’s really the most important first step, but then back it up with this new one and get aligned with what the current state of web security looks like as well as learn a few all new things like performing risk assessments.
So that’s where it all stands now and in many ways I see this latest course as an addendum to the first. We discussed modifying the first course or turning it into an all-new 2013 edition course but it really didn’t make a lot of sense, primarily because the first course remains 100% relevant in terms of the content, I mean it’s not like SQL injection 1.0 has now been upgraded to version 2!
Beyond the 2013 edition of the OWASP Top 10
Continuing the theme of how rapidly this industry changes, let’s take a moment to consider what’s already gone down since the 2013 edition of the Top 10. The biggies in terms of hacks, of course, were Adobe and Target with 152M and 110M records respectively granting them the dubious honours of the world’s largest data breach and the world’s largest breach of payment card info. That’s pretty serious stuff, but is it reflective of a general changing of attack scale or are they a couple of outliers?
Actually it’s quite clear where the trend of attack scale is skewed when you look at the largest recorded attacks:
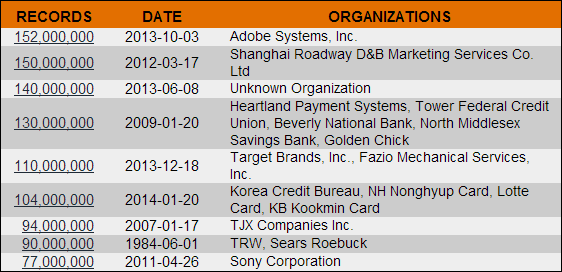
Five of the largest seven attacks ever have occurred in the last eight months. Whoa.
So that’s attacks, but of course one of the most significant changes in the security landscape is the change in sentiment towards governments. If you asked someone back in June last year when the 2013 edition was released where they thought the biggest nation state threats were coming from, they almost certainly would have said “China”. After all, only a few months earlier Mandiant had released its APT1 report detailing all sorts of cyber-nasties going on in the far-east. Damning stuff, but then Edward Snowden popped his head up and totally changed the public perception of the kinds of stuff governments are sticking their noses into.
The point is that even in the small amount of time that has passed since that 2013 edition hit, there have been significant changes in the information security space. I don’t yet know quite how much impact that will have on the next edition of the OWASP Top 10 and there’s a lot of water to go under the bridge yet, but you can see how dynamic this landscape is and how it inevitably impacts on the way we view risks and prioritise our defences.
For now, I hope this course helps all those wondering about what was new to fill that gap in their understanding and teach them a bunch of new things while they’re at it. Enjoy!