Yesterday, the website known as "LeakedSource" went offline. It's still early days and there's not yet an official word on exactly what happened, but the unfolding story seems to be as follows:
Yeah you heard it here first. Sorry for all you kids who don't have all your own Databases. Leakedsource is down forever and won't be coming back. Owner raided early this morning. Wasn't arrested, but all SSD's got taken, and Leakedsource servers got subpoena'd and placed under federal investigation. If somehow he recovers from this and launches LS again, then I'll be wrong. But I am not wrong. Also, this is not a troll thread.
LeakedSource provided sensitive personal information obtained from data breaches to anyone willing to pay for it. It was a service that occasionally popped up in news stories and recently appeared in WIRED. I've been asked for my views on the service in the past and how I felt about them providing passwords to people who didn't own them. If I'm honest, it's not really something I gave much thought too... until someone sent me my own personal data.
A few months back, a friend paid for their service and then went about notifying all their contacts who'd been put at risk. He sent me the following about my own personal data:
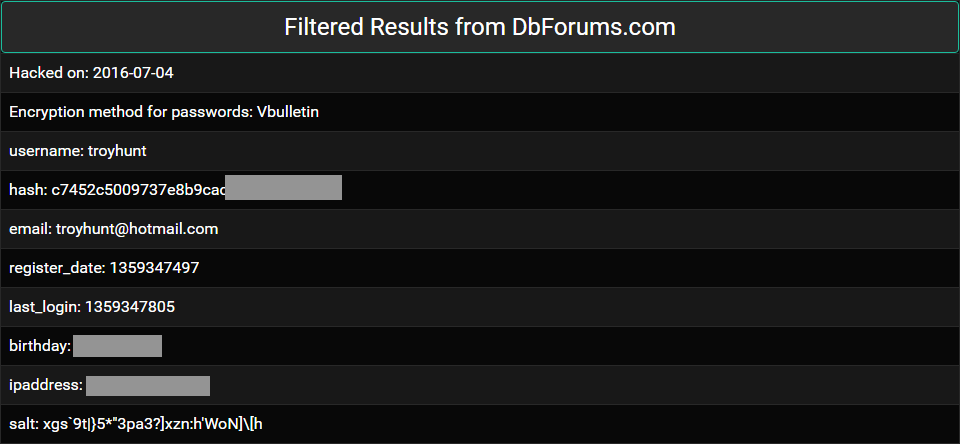
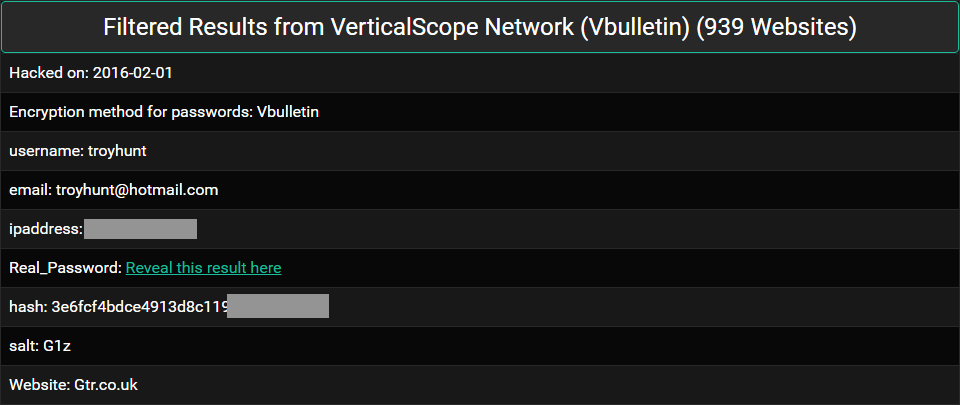
Now let's be quite clear about this: I see a lot of data breaches in my travels but I was still shocked to see my own personal information sold in this way. My birth date. My IP address. My password hashes. My cracked password hash (a very old, very poor one). I know full well that my own personal information is out there in multiple data breaches, but there's a big leap between it circulating in relatively closed circles and being put up for sale for a few bucks. Not just that, but being sold on the clear web with no respect for the personal consequences of data breach victims such as myself.
LeakedSource appeared in late 2015 and quickly attracted controversy. Last year there was the cease and desist order from LinkedIn where they took issue with the redistribution of their members' passwords:
We have demanded that parties cease making stolen password data available and will evaluate potential legal action if they fail to comply. As a result we have sent a C&D to LeakedSource
A little while later, they were booted off Twitter with the account remaining suspended to this day. They returned under the guise of @BigSecurityNews but there was never any question that it was merely a facade to promote their activities in lieu of the primary account now being off air. Perhaps foreseeing the inevitable result this week, that account has been dormant for the last couple of weeks.
By late 2016, it was becoming apparent that their actions were erring very much on the black side of grey. There was a constant flow of data that wasn't appearing anywhere else in the usual trading circles before first coming to air via their service. Speculation was rife that there was incentivisation occurring not just to provide data that had already been obtained, but to actively seek out new targets that could subsequently be added to the feed of data then monetised by selling the personal information of the victims to whomever was willing to pay for it. This was always rumoured amongst those "in the scene", but it's not yet clear whether this contributed to the take down or if it was solely due to the services directly provided on the site.
There was never any doubt that the service was being used for destructive purposes. A quick trawl around Twitter shows just how other people's personal information was being used:
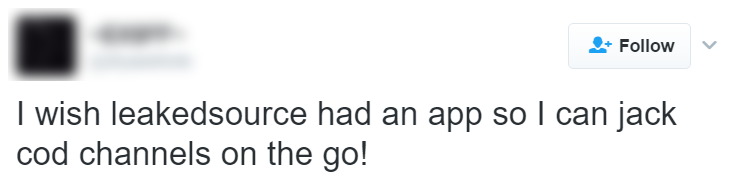
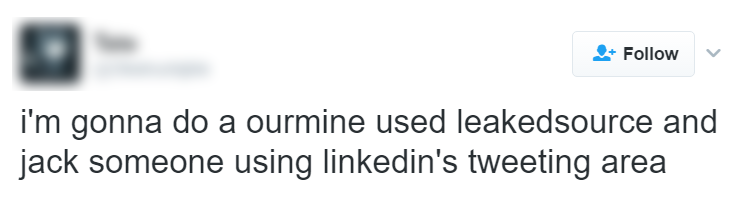
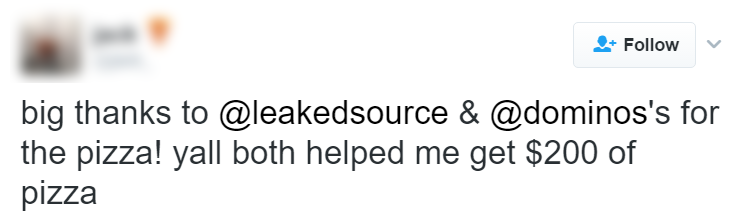
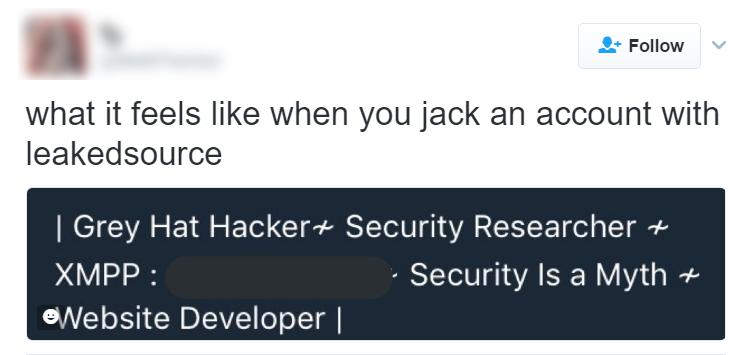
I've obfuscated these identities as I don't know what consequences those who paid for the service may now face, especially those who used it for malicious purposes. The theme here is very clear; the service was frequently used to do harm to others. Malicious use was broadly known and broadly discussed, even in the media:
The hacker will then run that username through LeakedSource.com and pay the website 76 cents for full results. In return, he’ll receive an email address (which can be run through the database again for even more information) and password.
In fact, that piece went on to explain how other notorious hacking collectives regularly used the data to compromise victims' accounts:
Other hackers have stated that J5Z’s LeakedSource method is the preferred strategy of OurMine, the collective that hacked Mark Zuckerberg’s Twitter account.
And then there's the folks behind the service. Or the guy. Or girls. Or who really knows because from the outset, it was pretty clear they didn't want to be identified. The earlier mentioned WIRED article quoted them as saying:
if nobody knows who we are or where our site is located, bad people can’t attack us
The veil of anonymity provided them with a veneer of protection which was always a thin one. It's easy to see why they would have wanted to remain anonymous given the nature of the service and how everyone knew it was being used. However, even whilst operating from behind Cloudflare, the location of the service was readily discoverable by the casual observer and was always going to be easily accessed by law enforcement. There's a lesson in there for anyone who believes they can operate with impunity whilst trading on the misfortune of others.
Now, to Have I been pwned (HIBP). Some people have drawn parallels to services that both myself and others run:
So I wonder how the feds justified raiding @leakedsource vs @haveibeenpwned, @breachalarm, @IsLeaked, etc.
— Mark Burnett (@m8urnett) January 26, 2017
I don't think that Mark genuinely considered HIBP or BreachAlarm to be operating in the same realm as what LeakedSource was (he later acknowledged the shadiness of the now defunct service), but let's address the fundamental differences in ethics and approaches anyway.
HIBP never makes any sensitive personally identifiable data available to anyone, not even the legitimate owners of the data. In fact, some time back I wrote about how I will not provide data breaches to other parties either in full (I've never passed a breach to anyone else), or in part (I always point individuals to that post when they ask for their data). The only exceptions I can think of is when I'm verifying a breach and I've written publicly before about how I'll reach out to existing HIBP subscribers and seek their support in verification by providing them snippets of data. Certainly, under no circumstances would I ever provide someone who doesn't own the data any access to it whatsoever. If you can demonstrate that you own the domain then you can see which accounts have appeared in which data breaches (many companies use this as a means of monitoring the risk their organisations are exposed to), but that's a far cry from handing over sensitive PII to strangers.
I've also never paid for data nor traded any of the breaches I've obtained. Creating a commercial market in no way improves the state of security, it merely provides incentive for malicious parties to obtain even more data.
Over the 3 and a bit years I've been running HIBP, I've found myself continually making small changes in direction in order to respond to changing sentiments and indeed changes in the data breach landscape. For example, when news of the Ashley Madison data breach hit, I elected to build out functionality to keep data from "sensitive" breaches beyond the reach of anyone who doesn't own the email address impacted by the incident (or the domain it sits on). At the time, that took a lot of thought but in retrospect the conclusion was simple: the data could cause serious harm to people so let's make sure that can't happen.
Some people expressed concern over them being discoverable in any data breach so I introduced the opt out feature. In that same post, I wrote about removing the VTech data because it was the right thing to do. Parents were able to get some comfort in knowing that data about their kids and indeed themselves had been removed from every possible location beyond VTech themselves and that was a very good outcome. In a similar vein, I never loaded the Red Cross data because like VTech, that was an incident we could contain and me not having the data was a very positive outcome (I didn't even retain my wife's or my own blood donation records from the leak).
I recently also added a rate limit to the API. I was seeing activity which I didn't believe was in keeping with the objectives of the project and posed the potential to put data breach victims at further risk so I put an immediate stop to it. (I later wrote about how I blocked large volumes of malicious traffic using Azure functions and the Cloudflare API, a model which continues to run beautifully to this day.)
I'm writing this at the end of my second week abroad doing back to back talks and workshops focused entirely on trying to help people keep their data out of services like HIBP.
Just had a really nice two-day workshop on web security by @troyhunt! Oh btw, thanks for mentioning that Belgian bank KBC so many times ;-) pic.twitter.com/MAw9hCIuYJ
— Jef Hermans (@jefhermans) January 26, 2017
I've said many times before that the best possible future for this service is that no more data flows into it; it would be an enormously pleasing result if more resilient systems were to stem the current flow of data taken out of vulnerable websites.
HIBP will continue to evolve. If public sentiment changes and, for example, the premise of searching via email address become legally or socially unacceptable then I'll adapt. If other regulations require it, then I'll work to keep the service running responsibly and in a way that keeps both regulators and data breach victims happy. I think about this every single day.
As for whoever is behind LeakedSource, I hope this incident presents an opportunity to rethink the ethics of how personal data should be handled. The WIRED article stated that some of them "are still in school" and they may well just be kids who were attracted by the allure of some easy bucks without actually being malicious individuals. I genuinely hope the consequences aren't too severe and that they're afforded the opportunity to go on and do awesome things. For now though, the web just became a safer place by their absence.