Back in August, I pushed out a service as part of Have I Been Pwned (HIBP) to help organisations block bad passwords from their online things. I called it "Pwned Passwords" and released 320M of them from real-world data breaches via both a downloadable file and an online service. This was in response to NIST's Digital Identity Guidelines and in particular, the following recommendation:
When processing requests to establish and change memorized secrets, verifiers SHALL compare the prospective secrets against a list that contains values known to be commonly-used, expected, or compromised. For example, the list MAY include, but is not limited to: Passwords obtained from previous breach corpuses.
Seen a password in a data breach before? Then now it's a pwned password and per NIST, you really don't want to be letting your customers use it any more. I followed up the first version with version 2, complete with just over half a billion passwords. But the really cool bit was the k-anonymity model devised by Cloudflare which I talk about in that blog post. That really started getting the service traction, but it wasn't until last week that things really started to fire:
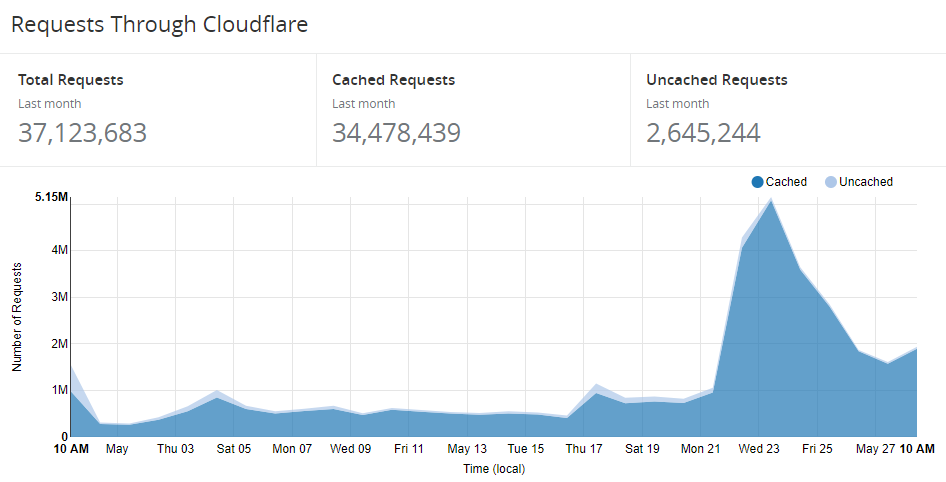
That up-tick on the 17th and then the really sizeable one on the 22nd are due to a few big players making really good use of the service. I want to detail those use-cases here because I'm always getting asked by people how the service is being used. So here it is - including some inside stories - Pwned Passwords in practice!
1Password
7 years ago now, I realised that the only secure password is the one you can't remember and from that day forward, I've been using 1Password exclusively as my password manager. When I released version 2 of Pwned Passwords, out of the blue they built it into their product. This wasn't some big effort on their behalf which took lots of planning either, they literally did it overnight:
I'm *so* impressed with what they've done here; I launched this service only 27 hours ago and they've already pushed this out. They had no prior knowledge I was doing this, they just got hands on tools right away and made it happen. That's awesome.
— Troy Hunt (@troyhunt) February 22, 2018
That was impressive and they gave people the ability to check any individual password against the online Pwned Passwords service (it was also part of the reason I ended up partnering with them on HIBP). It used the k-anonymity model to ensure the original password wasn't redistributed, but it was a one-by-one effort. Until this happened:
If you use 1Password account you now have a brand new Watchtower integrated with @haveibeenpwned API. Thank you, @troyhunt ❤️
— Roustem Karimov (@roustem) May 3, 2018
Also, looks like I have to update some passwords ? pic.twitter.com/toyyNRPI4h
They built in the ability to check your entire set of passwords against Pwned Passwords in a single action. That was via the web-based version of the tool and they followed that up last week with the launch of 1Password 7 for Mac, including Pwned Passwords as a first class citizen of the desktop app:
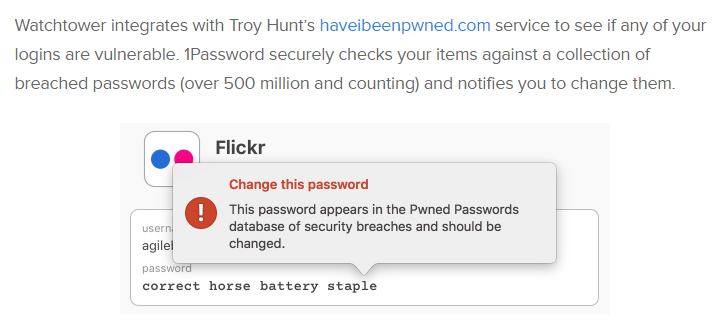
This week will see the launch of 1Password 7 for Windows so I'll be jumping on that one pretty promptly. I've been told the Pwned Passwords integration will come shortly after launch, but it's available to everyone already via the web version if you just can't wait.
EVE Online
Last month, I got the first indication that EVE Online - the massive online multiplayer RPG - was planning to implement Pwned Passwords:
WIP: Helping our @EveOnline players to be aware if their passwords are on a list of known compromised passwords. Thanks @haveibeenpwned ! CC: @troyhunt #tweetfleet #security #workinprogress pic.twitter.com/miovu6g25q
— Stefán Jökull Sigurðarson (@stebets) April 27, 2018
Stefán and I ended up talking quite a bit, especially around optimisations to the Cloudflare caching implementation to ensure it was going to be super-fast for them. Working with Junade Ali from Cloudflare who devised the original k-anonymity model, we got the cache-hit ratio way up:
But here's the really cool bit - check out that cache ratio at @Cloudflare over the last 24 hours - 98.4%! pic.twitter.com/hTm9risTx5
— Troy Hunt (@troyhunt) May 23, 2018
I've actually seen it round to 99% before as well but hey, now I'm splitting hairs! The point is that almost every single request to the service is now hitting one of Cloudflare's 150+ edge nodes around the world and returning the result in what is usually no more than low double-digit milliseconds.
Because I really wanted to share some real-world info on how the service is being used, I asked Stefán if he'd mind me publicising some stats which he kindly agreed to. Keep in mind that at the time of writing, the Pwned Passwords check is only on the login, it'll shortly be rolled out to the registration and change password features as well:
- EVE online is making 40k requests per day to the API
- The median response time for the service is 18ms
- The 99th percentile response time is 930ms
- On launch of the service, 18.6% of passwords were found to be previously pwned
- Several weeks later, that's now dropped to 17.3%
- They've also seen an up-tick in people updating their passwords and enabling 2FA
Stefán also shared some info on failure rates and I'm just going to quote him directly here:
Errors almost nonexistent, usually caused by network blips on our side. Out of almost 300k requests we've seen only 100 errors in the last week. That's a 99.96% successful request ratio and we can't for sure blame those 0.04% on the API as they could be on our side :)
I don't think that's entirely fair, I have actually seen 2 failed requests in the last week:
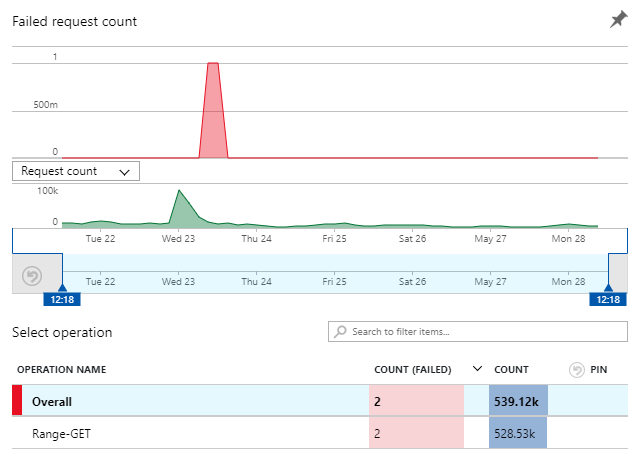
But depending on how you look at it, that's either a 99.999% success rate on Azure Function executions or a 99.99999% success rate on all calls made to the API because so many are returned by Cloudflare. Seven nines - I'm happy with that ?
Kogan
Kogan is one of our largest online retailers down here in Australia. Like most stores on the web, people log on, store personal account info and, of course, buy products. As of last week, Kogan is using Pwned Passwords to help protect those accounts:
Well it took a bit longer than we thought, but our signup and change password flows are now using the HIBP password API. https://t.co/OEwx4V1wBs is linked to in the validation errors. We'll iterate over time. Happy to hear feedback too!
— Josh Smeaton (@jarshwah) May 24, 2018
By virtue of me already having an account on the site, testing this was an easy one:
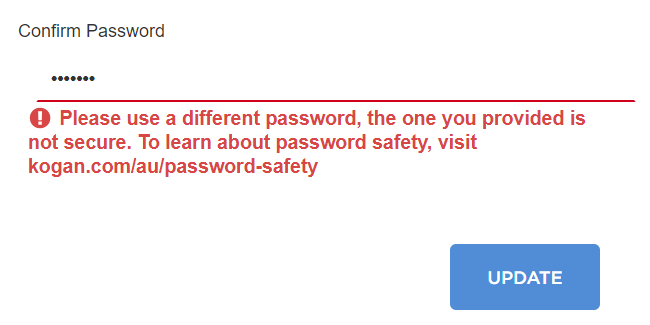
Pretty simple stuff, as is the password safety page they refer to. A site like Kogan's is used by the masses and we know empirically that your average person doesn't make the best choices when it comes to choosing passwords. How bad are some of those choices? This bad:
Today it's World Password Day: choose a word that's already in your heart. Like "Nutella", for example! #WorldPasswordDay #Nutella pic.twitter.com/Q9EERc6244
— Nutella (@NutellaGlobal) May 3, 2018
Yes, that's a real account and yes, people do actually use "Nutella" as their password:
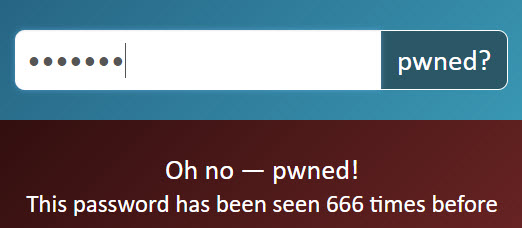
Except people on Kogan - they don't use Nutella anymore ?
Okta
I actually had Randall Degges from Okta reach out a couple of weeks ago and mention he was building a little tool called PassProtect to check passwords against the API using a browser extension. That's cool, I get a lot of people emailing me about similar things, so I replied and moved on. And then Okta launched it and somehow snagged a heap of news headlines:
I love that this isn't just tech headlines either, it's consumer press like Fortune and the Daily Mail (do read the comments on that one, just for fun...) The point is that it gets the concept of how poor passwords are exploited out in front of the masses, and that has the potential to lead to very positive changes in our overall security posture as an online community.
Okta wrote about their extension last week and they have a neat little demo GIF here that sums it up nicely too:
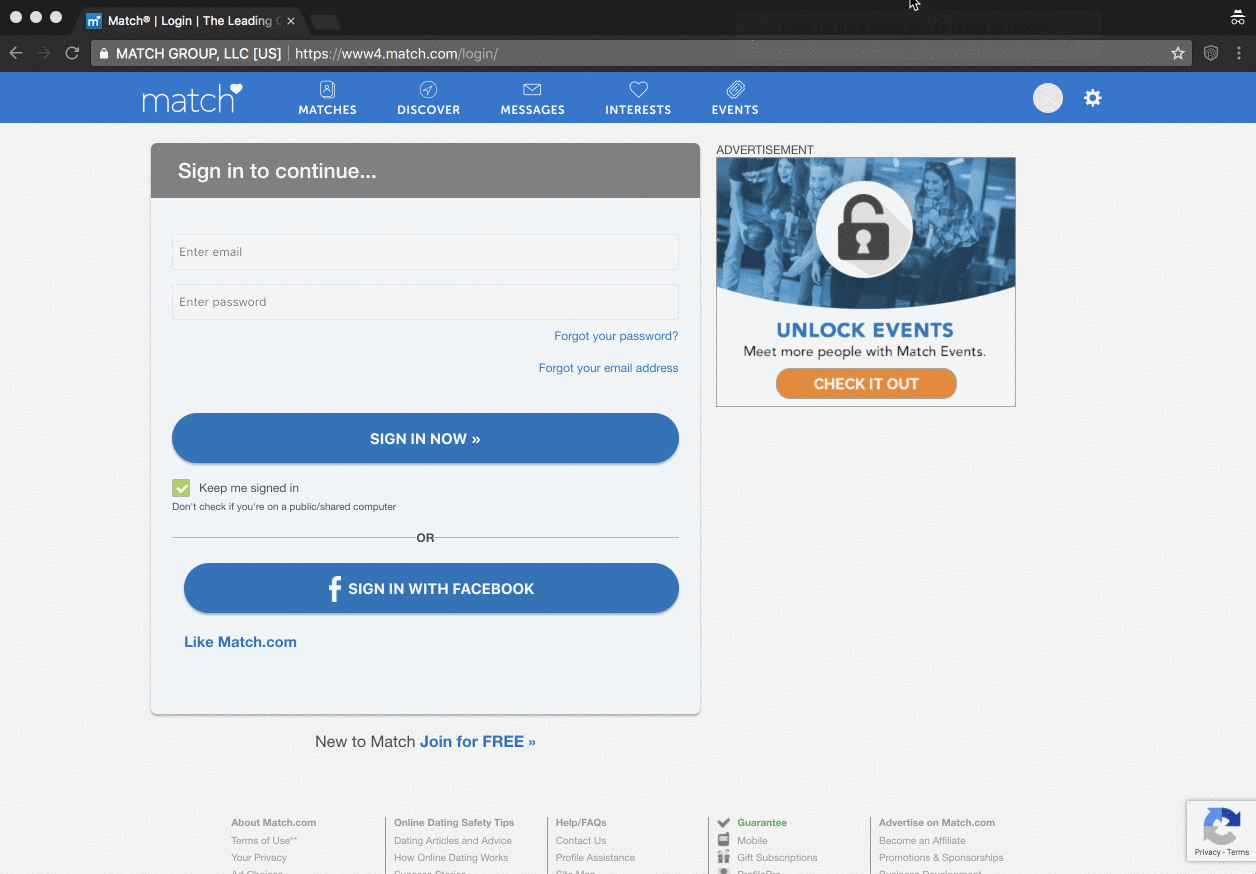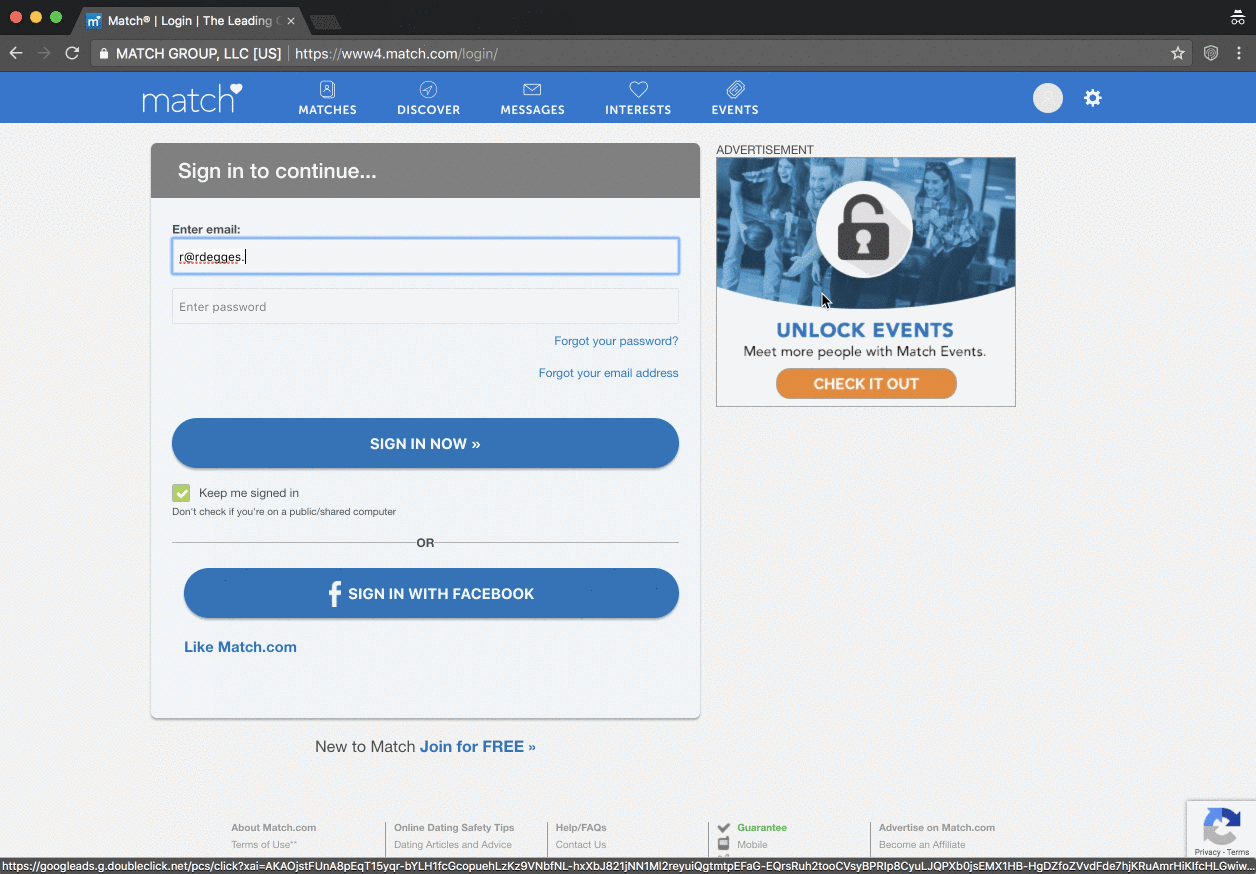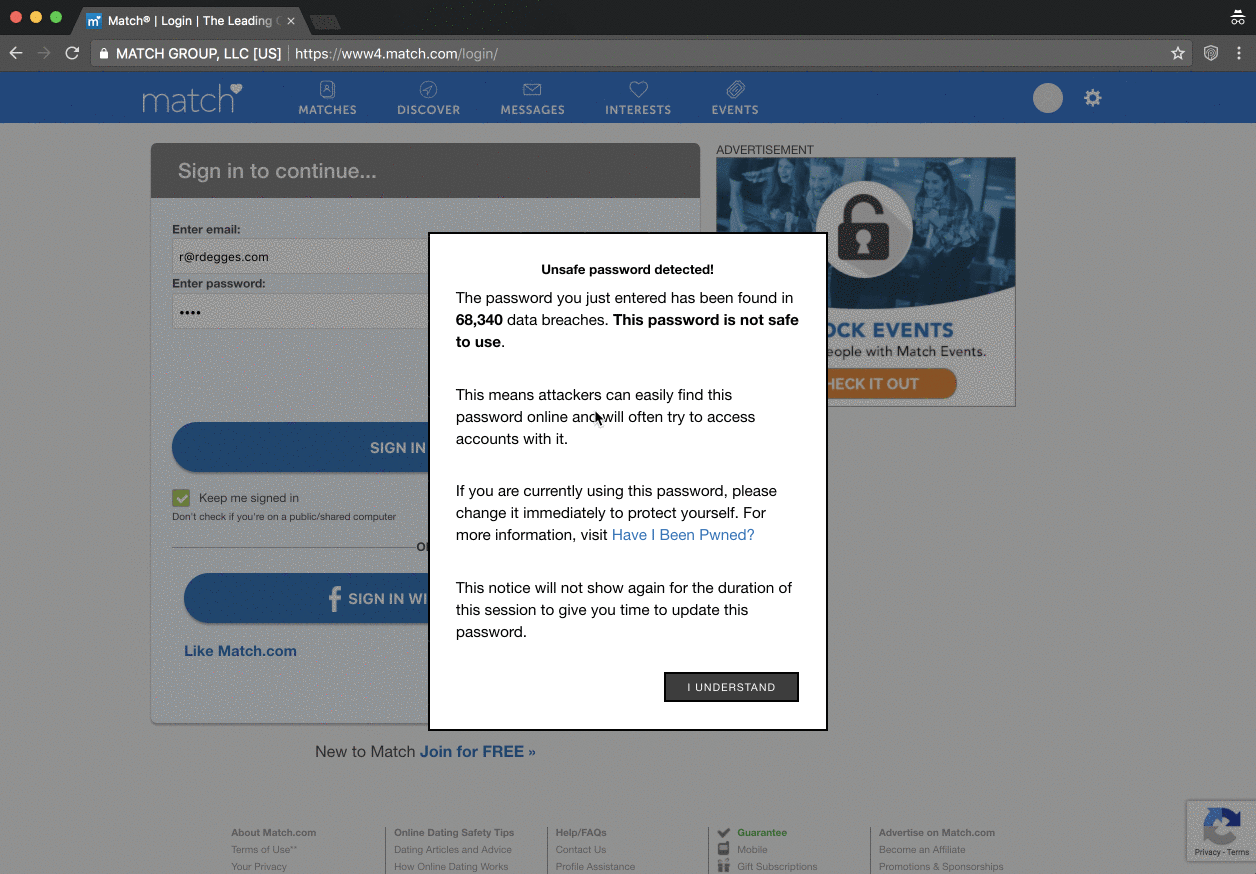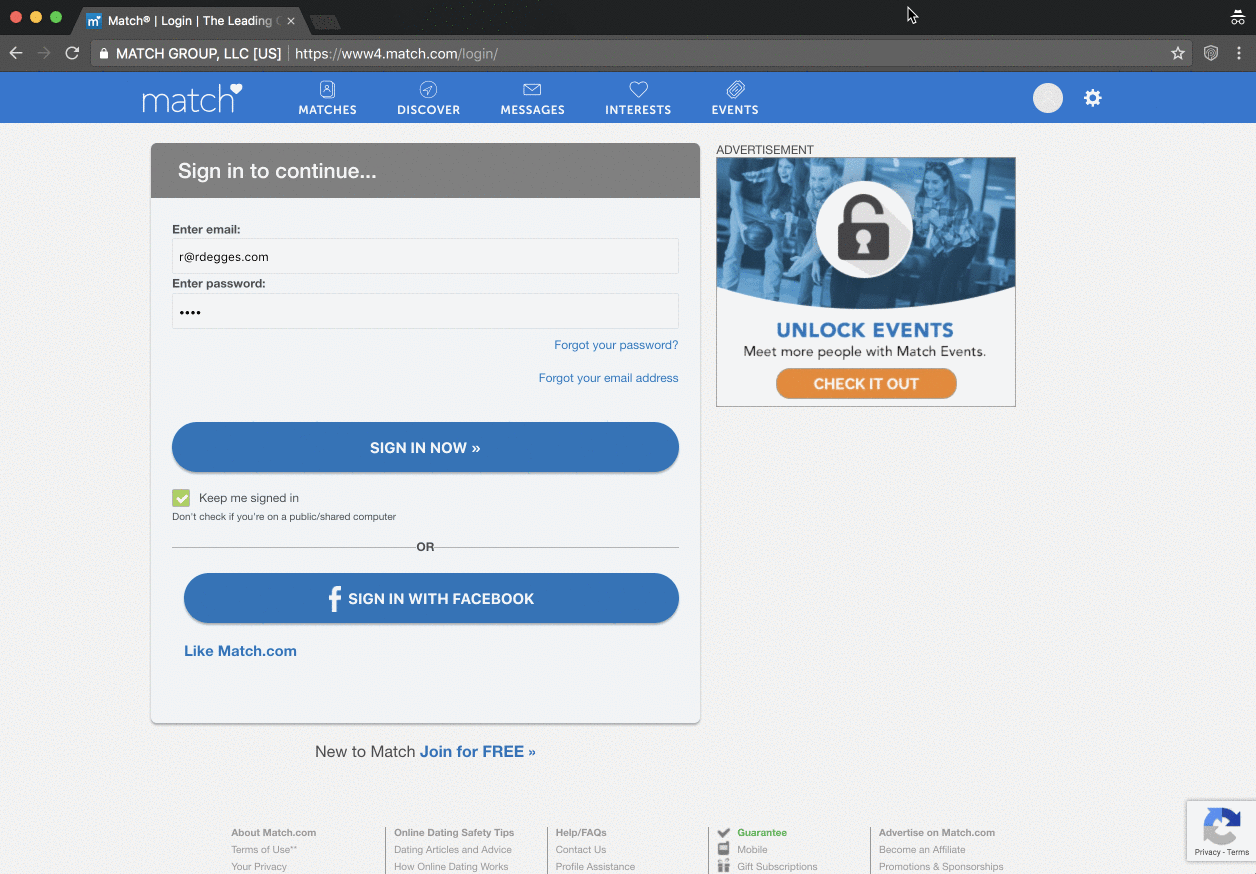
They've also got a dedicated PassProtect website and as you'll see there, they've made the extension both free and open source. I thought I'd give it a run on the login page of my Hack Yourself First site (a deliberately vulnerable site I use for training) and it worked beautifully:
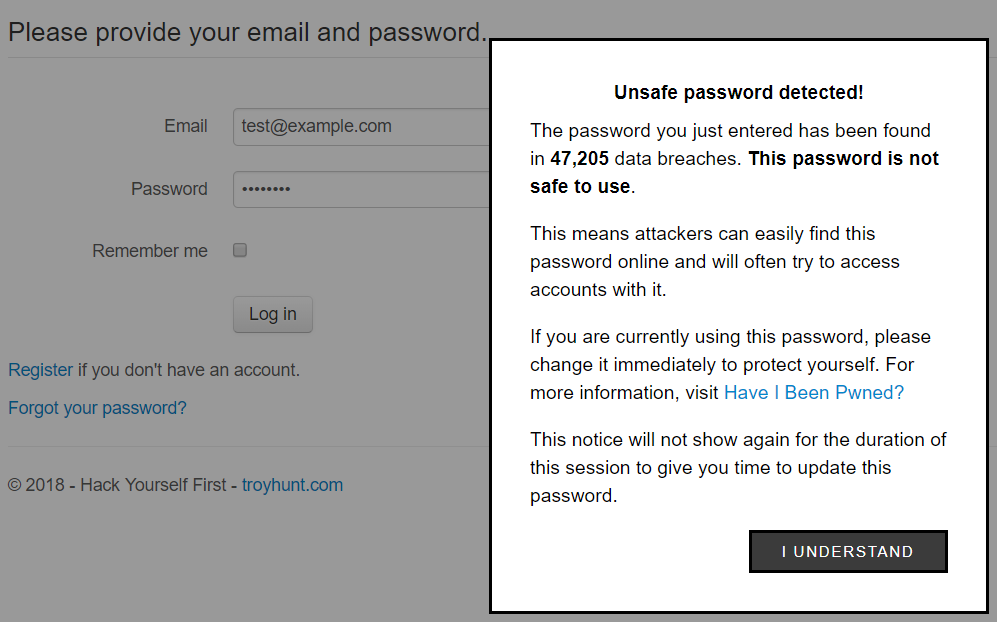
And just in case you're curious, you can observe the call to the Pwned Passwords API in the browser dev tools once focus comes off the password field:
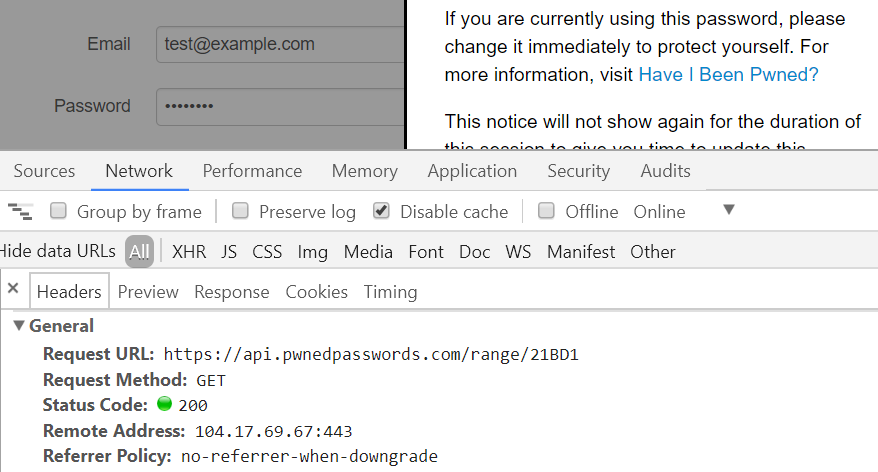
This is a really neat implementation by Okta with the extension simply looking for changes in password fields. I don't mean "simply" in any derogatory form either, there's beauty in the simplicity and that's why they're (quite deservedly) getting such good press.
Other users
I wanted to highlight some of the biggest use cases via the organisations listed above, but I also want to acknowledge some of the multitude of others I've seen pop up just in the last week.
For example, Bittylicious:
In February 2018 we integrated with the excellent HaveIBeenPwned service by @troyhunt to protect users from insecure passwords https://t.co/IUbliCoj0O pic.twitter.com/3Z6W99OqMQ
— Bittylicious (@Bittylicious_) May 22, 2018
There's also Red Shield down in my corner of the world (ok, so New Zealand is a couple of thousand km away, but that's "close" down here!) who provide shielding services to websites. They recently began offering Pwned Passwords to their customers as part of their services to help protect websites:
What I found interesting when Red Shield reached out recently was this comment:
It's much easier to communicate "Your password is a commonly used password" to users than complexity or entropy requirements
I wholeheartedly agree with this and as I've written before, strength indicators help people make ill-informed choices. Don't get me wrong - you still want a minimum bar to some degree (i.e. a min of 8 chars) - but we know that practices like character substitution or adding common punctuation to the end is extremely weak. When it comes to passwords, your average person is making precisely the same sorts of decisions as this bloke:
Security, security, security !https://t.co/JhNtlhFfdH
— CommitStrip (@CommitStrip) April 27, 2018
Inspired by this tweet by @AaronToponcehttps://t.co/EgTWuq1U7a pic.twitter.com/tWS4ep1S3g
Then there's the UK-based company Quidco who runs a cashback service:
Great to see https://t.co/rqmz0dscJH has integrated with https://t.co/f3g9WOlsrl's password checking service! Time to change my password methinks. Thanks @troyhunt - I owe you a few beers by now I'm sure. pic.twitter.com/SZowS9yiHw
— Richard Harlen (@richardharlen) May 25, 2018
Even the web interface for my Belgium mate John Opdenakker's mail account is using Pwned Passwords:
Just noticed that our webmail now has @troyhunt's pwned passwords integrated. This is really awesome ?#Security pic.twitter.com/2PySuxfesR
— John Opdenakker (@j_opdenakker) May 28, 2018
And you know the really cool thing about those last 2 tweets? Neither organisation had to lift a finger because that's actually Okta's PassProtect in action. It's such a slick, integrated experience that both Richard and John didn't even realise the respective services hadn't done any work! That's cool.
And Finally...
Lastly, I just wanted to reiterate the message I provided in the launches of both V1 and V2 of Pwned Passwords: this is 100% free. Not free as in "if you're not paying for a product, you're the product" either; there's no attribution requirement (I welcome it, but don't require it), you can do whatever you want with the downloadable data if you don't want to hit the API and if you do want to use the web service, there's no rate limit (quite the contrary as I've put a lot of effort into ensuring you can absolutely hammer it). There's absolutely no commercial angle from my side either; there's no "enterprise" version of Pwned Passwords, no up-sell and frankly, I've got no idea who's even using it beyond those who've explicitly told me. I do this with Cloudflare's support and because put simply, it's just a good thing for the web. I get a great deal of satisfaction out of building stuff that people love to use and given my access to passwords and having a platform to share this on, I've been able to make it successful and provide something genuinely useful. That is all ?