There's no way to sugar-coat this: Have I Been Pwned (HIBP) only exists due to a whole bunch of highly illegal activity that has harmed many individuals and organisations alike. That harm extends all the way from those in data breaches feeling a sense of personal violation (that's certainly how I feel when I see my personal information exposed), all the way through to people literally killing themselves (there are many documented examples of this in the wake of the Ashley Madison breach). Plus, of course, there's the ginormous financial impact; TalkTalk claims their 2015 hack cost them £42M and I've heard first-hand from those inside other companies that have suffered data breaches about just how costly they've been ("many millions of dollars" is very common).
Since day 1 of running HIBP, I've been overtly conscious of the shadiness of the realm within which it operates and consequently, I've done everything I possibly could to position it in the most ethical light possible. Transparency has been a huge part of that effort and I've always written and spoken candidly about my thought processes, how I handle data and very often, the mechanics of how I've built the service (have a scroll through the HIBP tag on this blog for many examples of each). Indeed, my own comfort level with the legitimacy of running this service has changed over time and that's really what I wanted to talk about here in this post: where it's come from, where it is today and how over time, it's been increasingly legitimised. This has changed most fundamentally in the last year and a bit so let me start there.
The Industry Cleaned Up a Lot in 2017
I very consciously avoided talking about it publicly at the time (largely because I didn't want to draw attention to it), but particularly around late 2016 and very early 2017, I was quite concerned with the broader genre that is data breach search services. The reason for this was that there were an awful lot of them operating in a very shady space attracting the wrong sorts of attention. Chief among these was LeakedSource which was eventually taken down in Jan last year.
Let's just recap on the value proposition of this service for a moment: for as little as 76c a day, you could subscribe to LeakedSource and view the raw data from a breach. What this meant was that people could pay their cash and access the personal data of anybody, including myself (sent to me by someone who bought access):
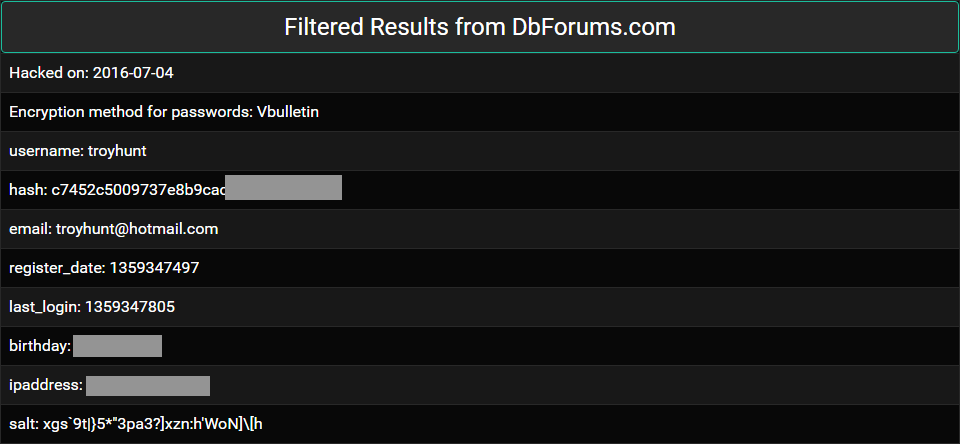
No verification of ownership, no censoring of results just the full (often sensitive) personal information of victims of data breaches. The operator justified the service by saying that the data was "all freely available online" and that in order to search for someone else's data, you must "have his written permission you may do so". Yet at the same time, they had absolutely no checks on data ownership and actively advertised the service on hacking forums which, of course, attracted precisely the sorts of customers you'd expect:
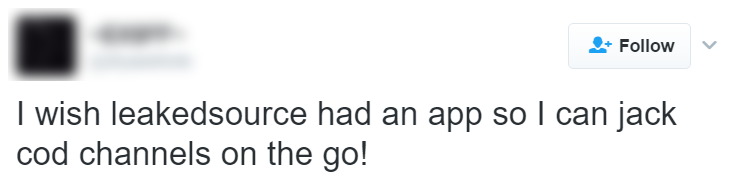
In Jan last year, that all came to a screeching halt. It took another year after that before the Canadian Mounties charged an Ontario man with a host of offences including "trafficking in identity information". (The video with RCMP Staff Sgt. Maurizio Rosa in it is worth a look, note the comment regarding the purchasing of data too, a practice I've always been vehemently against due to the incentives it provides to hackers.) He's yet to face court and answer those charges, but it doesn't look like it's going to work out real well for him.
I don't want to just focus on LeakedSource though, whilst it was the most notable at the time there were many others operating in a similar space (Leakbase was another that "went dark" in 2017). Yet at the same time, other organisations increasingly began using breach data to do good things and this is where my comfort level really started to shift.
A good example of this is the notifications Amazon sends when they find a data breach with the same credentials as one of their customers:
Hi @troyhunt, have any idea to which breach @Amazon are referring to here in this genuine email? Not had a @haveibeenpwned notification! pic.twitter.com/UkQHHjX5tT
— Paul Pitchford (@paulpitchford) March 24, 2017
I love this because it's proactive: Amazon have grabbed data that's circulating and taken proactive steps to protect both their customers and themselves. OpenTable also seems to be pulling data from other breaches:
.@troyhunt @GossiTheDog did @OpenTable get popped? pic.twitter.com/hPvvbFODyZ
— Random Robbie (@Random_Robbie) March 7, 2018
(Side note: getting the wording of these emails right is absolutely critical, as is evidenced by the accompanying tweet which casts suspicion over OpenTable's security posture.)
LinkedIn also does the same thing, this one sent to me by a follower:
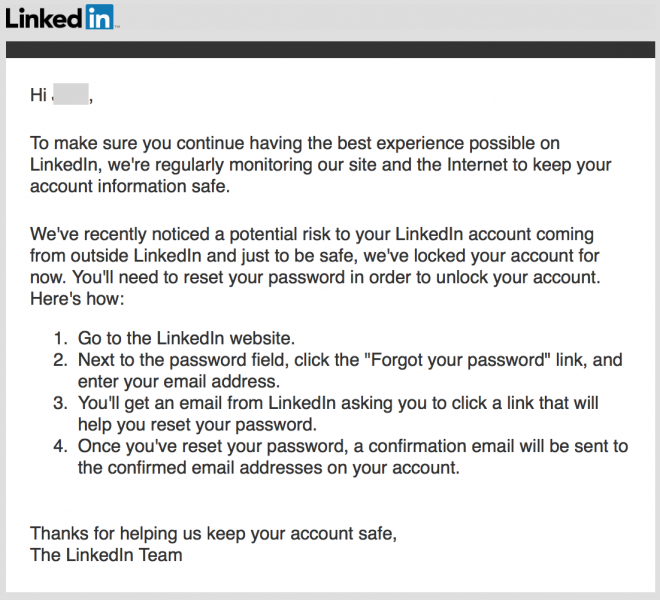
The premise of companies accessing data breaches in order to protect customers has really taken off and frankly, sometimes I think it even goes too far. I received this one myself from Pandora who merely found my email address in another data breach:
Just got this from @pandora_radio, sign of the times: pic.twitter.com/EwDopbSCRx
— Troy Hunt (@troyhunt) June 28, 2016
The point is that there are ways to use this data for good and what we've seen over the last year and a bit is the bad players dropping off whilst the good players gained prominence. What that means for the industry is "a rising tide lifting all boats"; it's becoming more legitimate for all those doing the right thing with the data. Let me shift attention back to HIBP because there's been a heap of other things happen over the last year that have really helped with the legitimisation the title of this post speaks about.
Breached Sites Have Been Embracing HIBP
One of the things that's really pleased me is the way breached sites have embraced HIBP after they've suffered a security incident. A great example of this is the self-submission of their breached data. On 3 separate occasions now, services that have suffered a data breach have reached out and said "we'd like our members to be able to confirm they've been impacted by searching HIBP". TruckersMP first did this in Feb 2 years ago, Ethereum followed in December 2016 as did biohack.me in August last year. They all recognised that HIBP is there to help victims of data breaches after things go wrong and willingly offered a copy of the data that was now in public circulation.
Then there was this one from Daily Motion in August:
I'm very pleased to see @dailymotion reference @haveibeenpwned in this fashion after I loaded their data breach https://t.co/X5zyHm3aLW pic.twitter.com/Yw9lmCLxT8
— Troy Hunt (@troyhunt) August 11, 2017
Their data first turned up on LeakedSource the year before (I suspect the original attacker was paid for it, hence it appearing there before anywhere else), so the data breach itself wasn't a surprise to them, but obviously once it appeared on HIBP the incident received more exposure again.
Oftentimes, the first a company knows of a data breach is when I send them their data. In some cases, this really rattles the organisation, particularly those that are less well-equipped to deal with these incidents (i.e. not as tech savvy). But increasingly, I'm finding the engagement with hacked companies is being well-received, for example after the Disqus disclosure in October:
And the We Heart It breach just a few weeks later (I referred them to the Disqus disclosure measure as an example of best practice hence the similarity in their messaging):
Or it may even just be a little reference and a link per Kickstarter's update breach notice:
Engagement with these organisations may not necessarily always result in them giving a hat-tip to myself or HIBP, but the experiences I've had with many of them have not only led to public disclosure, but also resulted in some very good communication of the incident. For example, the imgur breach in November and the Ancestry data breach in December. The point is that the very organisations I'd once feared would react badly to a presence on HIBP are responding in quite the opposite way. Of course, nobody ever wants to have their logo on the who's been pwned page, but I'm finding organisations increasingly accepting of the fact that data breaches happen and they're simply getting on with the job of managing the aftermath in a responsible fashion.
But it's not just organisations that have already been pwned that are giving HIBP a shout-out, let me share some more proactive examples.
HIBP is Becoming the "Go-To" Resource for Protecting Accounts
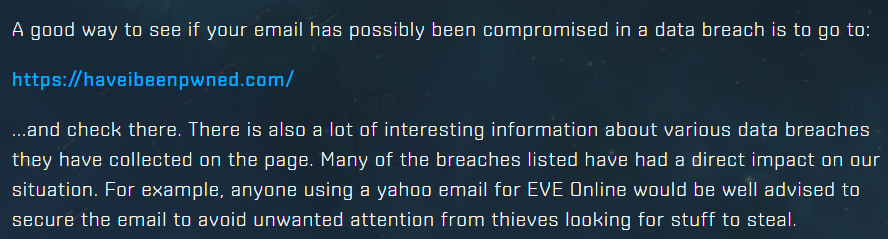
Last month, I noticed this piece pop up on EVE Online:
I love this because it's proactive; it's encouraging people to make a behavioural change by seeing first-hand how extensively they've already been pwned. I saw the same thing again from Epic Games just a couple of weeks ago with the release of their Fortnite blockbuster:
Sage advice by @FortniteGame! https://t.co/p8t8i7mvrK pic.twitter.com/rIBh5Y7dbj
— Troy Hunt (@troyhunt) March 10, 2018
Then there was this nice plug from AwardWallet back in November:
@troyhunt just got this from @AwardWallet for @haveibeenpwned pic.twitter.com/kNiEk2J5nR
— a muppet (@FeMaven) November 29, 2017
Back in September, I saw the same again from Deliveroo
And one that's come as a real surprise - I've heard many similar examples of the following advice from Netflix where an operator recommends HIBP during a support call:
@troyhunt Dealing with some Netflix account issues and the support rep directed me to https://t.co/2D1Rrcvx9K. Maybe you can hit them up for a free account or your own movie. :-)
— DevastationInc (@DevastationInc) February 6, 2018
Incidentally, it's reasons like the Netflix example which demonstrate the value of keeping this data publicly searchable, namely that it helps support staff establish possible sources of account takeover. I touched on this in my September piece on the ethics of running a data breach search service.
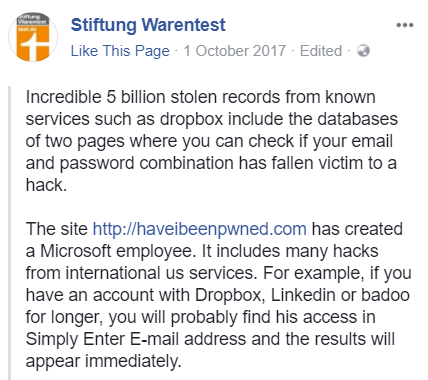
Recommendations for checking HIBP can come from places I never expected, for example German company Stiftung Warentest:
Whilst I may not have previously heard of them, apparently their opinion carries some weight:
They’re considered to have absolute integrity and is trusted by everyone here but conspiracy theorists, including the government afaik.
— Jannis Tenbrink (@the_jannis) October 2, 2017
Or from very familiar names, such as Google:
Nice to see @GoogleForEdu recommending @haveibeenpwned by @troyhunt to schools on @edugeek - https://t.co/dMOzPeJnb7
— Matt Smith (@matt40k) December 11, 2017
Consider why organisations like the ones above do this: they have to deal with account takeovers every single day - it's a massive issue. It's in their best interests to drive more positive security hygiene amongst their members and evidently, having customers check HIBP for breach exposure helps them do this.
Sometimes, endorsement even extends through to the real media!
@troyhunt just to let you know that you and HIBP get a positive mention in the UK press pic.twitter.com/iSIqGGirOr
— mathewbutler (@mathewbutler) March 10, 2018
And a big "thank you" to that organisation for causing me to register yet another variant of the HIBP domain name to ensure that havei-beenpwned.com is fully functional!
Apparently, HIBP is even getting mentions at Harvard these days:
Was excited when ‘have I been pwned?’ & @troyhunt was referenced in class at Harvard. Told the prof how I used to spend summers working in his office at Pfizer making binders for my dad!
— Arjun Bisen (@ArjunBisen1) February 19, 2018
(Fun side story: Arjun's dad was my boss at Pfizer for about 14 years, must have been a weird coincidence when he heard HIBP mentioned!)
But as much as HIBP has received some great plugs by companies recommending people use it, it's the media that's generated the most attention.
Press
I actually used to maintain a page listing major media pieces, but the whole thing got too unwieldy as the press mounted. That's a link to an archive.org copy of it (I've since removed the page), I tend to just link people to a Google news search result these days:
I got to thinking about the press again this week after HIBP popped up on a Belgian TV show:
Tonight @haveibeenpwned was featured on Belgian TV @opVIER, but I wonder if @troyhunt will notice a spike in traffic ? pic.twitter.com/HIsKN6X41k
— Guy Mahieu (@guy_mahieu) March 19, 2018
There's a heap of similar examples to this, perhaps the one which made me most think about how I deal with the sudden influx of traffic was The Martin Lewis Money Show in the UK which ultimately led to this:
So @haveibeenpwned just copped a massive sudden spike of traffic sent faster than Azure could scale. The Money Show? https://t.co/pg94112VlV pic.twitter.com/9TDE5zgFbe
— Troy Hunt (@troyhunt) May 15, 2017
It's a fascinating scaling problem to deal with: how do you handle a 100x change in traffic volumes over a period of 60 seconds whilst also minimising infrastructure costs? I talk about it in that blog post and have since made some other big changes, especially to the aggressiveness with which Cloudflare caches content.
One of the great things the media has done for HIBP is to put it out in front of everyday people, that is folks who may not live and breathe tech like (probably) you and me. Of course, the media can totally misrepresent the mechanics of data breaches and how they actually occur (as I've lamented before), but occasionally, pieces like this one from the Wall Street Journal really nails it:
I especially like the focus on trustworthiness, plus of course the general good advice that an outlet like this can put out in front of normal folks. Mind you, those same media companies struggling with the name have caused me to register some rather odd domains including haveibeenprawned.com and haveibeenporned.com, thank you very much.
But one of my favourites is one targeted more towards us tech people, and it's this one from WIRED:
Want to know if you've been hacked? @troyhunt has all the details https://t.co/YBjZzoWLEa pic.twitter.com/He8radYyo4
— WIRED UK (@WiredUK) August 9, 2016
I remember doing that photo shoot with them a couple of years ago, standing around in the rain in London whilst struggling with a cold and almost no voice. But hey, the pics came out great and I actually have a page from the real print WIRED mag framed on my wall now.
In gathering these references over the last 6 months or so, there was one particular source which popped up over and over again that really surprised me - the police.
Law Enforcement Has Been Extensively Recommending HIBP
Remember how I started this post by referring to all the illegal activity which led to HIBP even being necessary in the first place? You can imagine how tweets like this initially came as a bit of a surprise:
A shout out for @haveibeenpwned by @troyhunt at the Cyber Security Summit today. Held at @LancsPolice by @LanpacLtd and presentation by @TITANROCU! pic.twitter.com/uU315gb1mz
— Scott Helme (@Scott_Helme) November 23, 2017
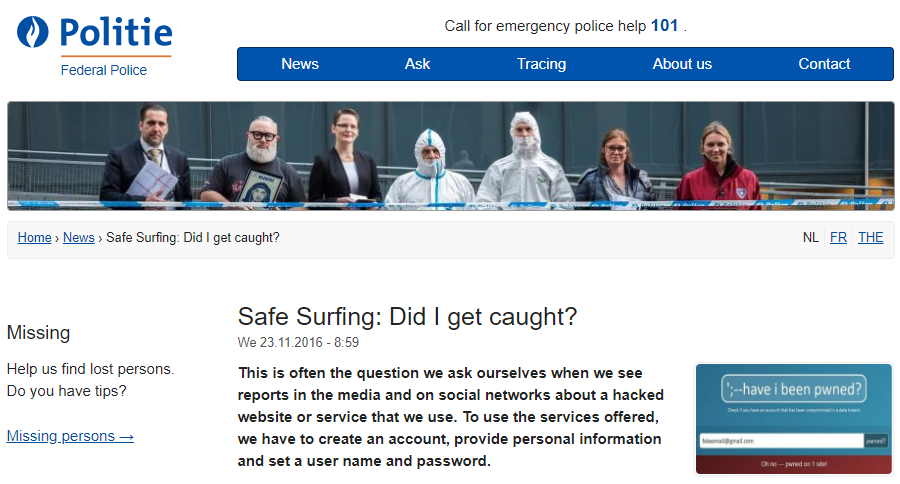
In fact, police forces all over the world have been publicly promoting HIBP, for example the Belgian federal police (Google translated for non-Dutch speakers):
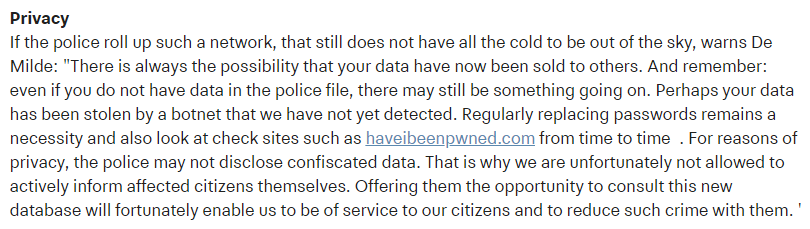
And whilst I'm translating things from Dutch, here's another one from the Netherlands police:
(Ok, we disagree on the regular rotation of passwords, but it's a nice shout-out all the same.)
But it's back in the UK again where law enforcement has been a regular supporter of HIBP via a number of shout-outs over recent months. For example, via the Police Service of Northern Ireland:
Looking to see if your email address has ever been compromised? Why not pay a visit to https://t.co/6YlDI3yBR8.
— PSNI (@PoliceServiceNI) March 13, 2018
Remember always use a strong separate password for your email account. #PSNICyberProtect @CyberProtectUK @cyberawaregov @actionfrauduk pic.twitter.com/Uobx1j5tNk
Back in England, the Leicester Cyber Aware account (and their dogs) recognise HIBP's role in keeping people safe:
#FF These guys ...to keep you safe ?@waynedenner @GlosSaferCyber @TakeFive @UK_SIC @kentpolicecyber @HP_Cyber @MFF_Forum @haveibeenpwned @EC3Europol @TheParentsZone @CifasUK @AgainstScams @GetSafeOnline @CyberProtectUK @NottsFraudCops @thebreckfound @gcluley @WMP_ECU pic.twitter.com/gTG2rrwdrM
— Leics Cyber Aware (@leicscyberaware) December 8, 2017
A bit further south and the Devon and Cornwall Police's Cyber Protect team feels the same way:
“Many well-intentioned people simply give up and don’t report serious security incidents when the effort is too high or the risk is too great. That has to change”
— D&C Police Cyber (@DC_CyberProtect) January 15, 2018
Well said! @troyhunt #databreach #hacking #hibp #CyberSecurity https://t.co/s5fpXMrtyc
Over to Kent and it's the Police Cyber Crime Unit's turn:
#CyberSecurityawarenessmonth , Check to see if your email address has been compromised? https://t.co/mFZ5ZAYBLm pic.twitter.com/hqV8hTvnVw
— Cyber Crime Unit (@kentpolicecyber) October 4, 2017
Even Police Officer Tony Murray recently gave Pwned Passwords a plug and offered some very good advice whilst doing so:
⚠️ONLY check active passwords via the #DOWNLOADED list!
— Police Officer Tony Murray (@CityPoliceTell2) January 29, 2018
You have strong passwords, you use different #passwords for different accounts AND YOU could still be compromised❗️
⚠️Are your passwords already part of the 306 million already known?https://t.co/oaFVw75lSb #Tell2 pic.twitter.com/1vq8ieWchd
All of these came as a surprise and getting back to the original context of this post - "the legitimisation of HIBP" - you can see why I value them. Having law enforcement speak in glowing terms has been enormously encouraging. Let me now take that one step further and talk about government.
HIBP is Increasingly Recognised by Governments Around the World
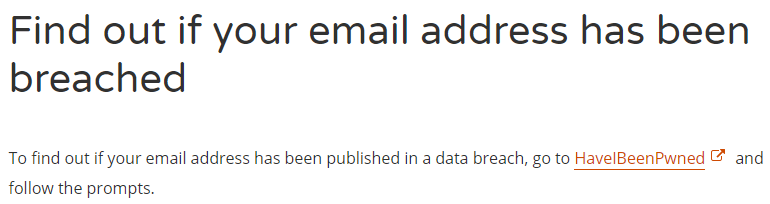
I'm going to talk about some government exposure that will be pretty familiar to many people shortly, but it's the unexpected stuff that, well, I just never saw coming. For example, the Estonian CERT advising people to check HIBP:
Much closer to home for me, our local Aussie Government recently gave HIBP a shout-out via their Stay Smart Online initiative:
But there were 2 especially important recent events tied to government and I want to spend a bit of time explaining the significance of both. The first one was this:

This was my testimony to US Congress in November (there's a video of it in that link). Some people actually joked in advance of this that the invitation was a means of getting me over to the US so that I could subsequently be locked up for sitting on billions of records of breached data! In reality, quite the opposite happened: I sat in front of law-makers and talked about this industry I've found myself in, including the relevance of HIBP. I never saw that coming and it will stick with me for life as both a momentous occasion in my own career and indeed a milestone in the history of HIBP.
More recently, I was especially proud to see something I'd been working on for the past 9 months finally come to fruition:
We’re excited for the opportunity to work alongside Troy and we’re looking forward to trailing the use of his service in the coming weeks to help alert UK Government departments if their users have potentially compromised credentials https://t.co/L1usl2qwUt
— NCSC UK (@ncsc) March 2, 2018
As I wrote earlier this month, both the NCSC in the UK and the ACSC in Australia are now using HIBP to monitor their government domains. This was enormously important to me on many levels; it was obviously recognition from the respective governments that HIBP has a role to play in protecting their people, but it was especially poignant to me that both governments were also happy to acknowledge it publicly. That's a really big deal in terms of the whole legitimisation piece and certainly it was something I was especially conscious of as the arrangement fell into place. These two governments won't be the last either - I'm presently in discussion with multiple other departments from different parts of the world and I hope to be able to share the outcome of that shortly too.
Summary
When I started HIBP back in late 2013, I never envisaged any of what you've read above. Over the last 4 and a bit years, there's certainly been some ups and downs in terms of how comfortable I've felt with the legitimacy of the service and obviously I'm now exceptionally happy with where it sits today. It's where it is due to a combination of good luck and good management; I've been fortunate with the timing in the industry in terms of the prevalence of data breaches, but I've also been exceptionally cautious with how I've positioned HIBP, how I've engaged with corporations and governments and indeed the moral compass I've run it by.
I'll have more to share on the HIBP roadmap in the near future, this post was really just an opportunity for me to take a moment and reflect on where things stand today. A big thanks to everyone who has supported both the project and myself to help get it to this point!